1. Overview of the Trusted Firmware-M project[edit | edit source]
Trusted Firmware-M (TF-M) is an open-source project managed by TrustedFirmware group[1]:
- Source code is available from git repositories:
- STMicroelectronics version of TF-M Source Tree used in OpenSTLinux for STM32MP2 series is available in STMicroelectronics Github with associated releases [2]
- Official source code [3], without STM32MP2 series support
- Documentation is available
- for the latest official version in https://trustedfirmware-m.readthedocs.io
- for the latest LTS version on which our software is based in Unsupported domain!
- for OpenSTLinux, the documentation is generated from source, with STMicroelectronics add-ons
The software environment is design to run in the Secure Processing Environment (SPE) of ARMv8-M microcontrollers following the PSA Certified guidelines[4].
TF-M uses secure partitions that offers services. They can be isolated following different isolation levels:
- Level 1: SPE and NSPE isolation.
- Level 2: Level 1 + Application Root of Trust (ARoT) protection from NSPE and PSA Root of Trust (PRoT) protection from NSPE and ARoT.
- Level 3: Level 2 + Secure partition protection from NSPE and other secure partitions. PSA Root of Trust (RoT) domain protection from NSPE and all Secure Partitions.
The default secure partitions that can be isolated to the nonsecure environment:
- Initial attestation
- Crypto services
- Internal trusted storage
- Firmware update
- Protected storage
The secure partitions are accessible using PSA dedicated API[5].
2. License[edit | edit source]
TF-M is delivered under a BSD-3-Clause style license and can run secure partitions without restriction on their licensing model. It also includes different sub-projects with their dedicated license, see Unsupported domain! for details.
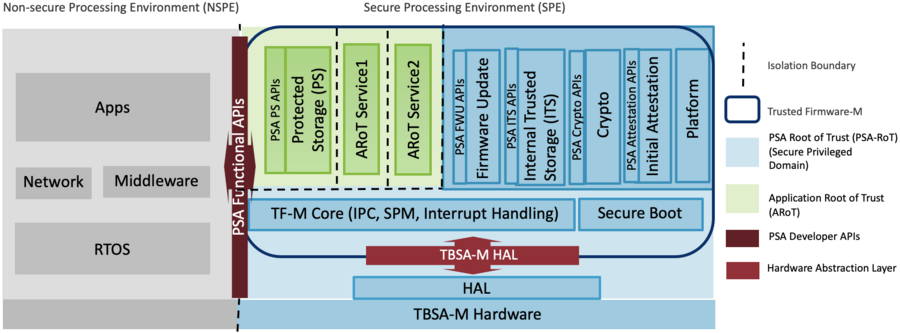
3. Architecture overview[edit | edit source]
4. Software profile[edit | edit source]
TF-M defines different profiles offered to the user to select the security level targeted. See Unsupported domain!for more information.
STMicroelectronics implementation uses the medium profile by default.
5. Secure boot[edit | edit source]
The Unsupported domain! is driven by the platform first stage boot loader.
On STM32MP2 series, depending on the TD flavor (A35-TD or M33-TD) ![]() defined on the platform, different flavors are allowed to achieve the secure boot.
defined on the platform, different flavors are allowed to achieve the secure boot.
5.1. For A35-TD flavor  [edit | edit source]
[edit | edit source]
For A35-TD flavor ![]() , the secure boot is ensured by default trusted boot bootchain.
, the secure boot is ensured by default trusted boot bootchain.
To complete the secure boot chain and run TF-M in TrustZone area, it has to be started following the secure coprocessor loading process.
This will ensure that the TF-M and associated nonsecure part (NSPE) is authenticated and follows the secure boot requirements.
5.2. For M33-TD flavor  [edit | edit source]
[edit | edit source]
For M33-TD flavor ![]() , the ROM code authenticates an FSBL-M, which is MCUboot, as it is the default secure bootloader (BL2) for TF-M. This FSBL-M authenticates (and decrypts) the defined slots to be loaded: one for the the DDR firmware, one for the TF-M image and its associated NSPE.
, the ROM code authenticates an FSBL-M, which is MCUboot, as it is the default secure bootloader (BL2) for TF-M. This FSBL-M authenticates (and decrypts) the defined slots to be loaded: one for the the DDR firmware, one for the TF-M image and its associated NSPE.
6. Secure Partitions[edit | edit source]
Unsupported domain! (aka Service) is the component providing secure functionalities in SPE, and Client is the user of the Service. A service acts as a client when it is accessing its depending services.
Services are grouped into Secure Partition (aka partition). A partition: Contains services with the same purpose.
The TF-M secure partitions described in the next chapters are generic and provided by default in TF-M by the TrustedFirmware group.
6.1. Crypto[edit | edit source]
Unsupported domain! offer PSA Crypto API[6] implementation in a dedicated RoT secure partition. The implementation is based on Mbed crypto[7].
For the keys and secrets management on STMicroelectronics products, you can also check the page How to manage keys and secrets in TF-M.
6.2. Firmware update[edit | edit source]
The Unsupported domain! implements the PSA Firmware update API [8]. It gives all the mandatory features to authenticate, verify and install a new updated image and manage the security about the update process.
6.3. Initial attestation[edit | edit source]
Unsupported domain! implements the PSA Attestation API [9]. It provides a verifiable report of the state of the platform.
6.4. Internal trusted storage[edit | edit source]
Unsupported domain! implements PSA secure storage API [10]. The internal storage is designed to store the most secure and critical assets used by the RoT.
6.5. Protected storage[edit | edit source]
The protecte storage (PS) partition in the ARoT that implements the PSA secure storage API [10] and allows to store secure data on external storage, see Unsupported domain! for details.
7. STM32MP2 series secure partitions[edit | edit source]
STMicroelectronics provides STM32MP2 series specific partitions and secure services to nonsecure applications running on Arm®-Cortex®-M33:
- partitions in platform/ext/target/stm/common/stm32mp2xx/secure_fw/partitions/
- services API in platform/ext/target/stm/common/stm32mp2xx/secure/services/include/uapi/
For M33-TD flavor ![]() , it has been extended to also provide system and secure services to Arm®-Cortex®-A35.
, it has been extended to also provide system and secure services to Arm®-Cortex®-A35.
7.1. Coprocessor CPU management[edit | edit source]
This service is used to control other CPUs (Cortex®-A35 or Cortex®-M0+) from Cortex®-M33. This is only available for M33-TD flavor ![]() .
.
The API is described in tfm_ioctl_cpu_api.h .
7.2. Low Power[edit | edit source]
The low power service is provided by the PM partition (platform/ext/target/stm/common/stm32mp2xx/secure_fw/partitions/pm/ ) and based on the STM32MP2 low power firmware.
This is only available for M33-TD flavor ![]() .
.
This firmware is compiled with TF-M, integrated in the PM partition and loaded in RETRAM during partition initialization.
The API is described in tfm_pm_api.h
7.3. SCMI[edit | edit source]
The SCMI service is provided by the SCP partition (platform/ext/target/stm/common/stm32mp2xx/secure_fw/partitions/scp/ ) and based on the SCP-firmware[11]. Please check SCMI overview for more details.
This is only available for M33-TD flavor ![]() .
.
The API is described in tfm_scmi_api.h
7.4. Watchdog[edit | edit source]
This service is used to manage secure Cortex®-M33 watchdog.
The API is described in tfm_ioctl_wdt_api.h .
7.5. PSA ADAC[edit | edit source]
The Authenticated Debug Access Control (ADAC)[12] Unsupported domain! is only available for STM32MP21x lines ![]() and M33-TD flavor
and M33-TD flavor ![]() .
.
The API is described in tfm_adac_api.h
8. To go further[edit | edit source]
Please refer to the TF-M documentation :
And the WIKI pages:
9. References[edit | edit source]
- ↑ https://www.trustedfirmware.org/projects/tf-m
- ↑ https://github.com/STMicroelectronics/trusted-firmware-m/releases
- ↑ https://git.trustedfirmware.org/plugins/gitiles/TF-M/trusted-firmware-m.git
- ↑ https://www.psacertified.org
- ↑ https://www.psacertified.org/getting-certified/functional-api-certification/
- ↑ https://arm-software.github.io/psa-api/crypto/
- ↑ https://github.com/Mbed-TLS
- ↑ https://arm-software.github.io/psa-api/fwu/
- ↑ https://arm-software.github.io/psa-api/attestation/1.0/
- ↑ 10.0 10.1 https://arm-software.github.io/psa-api/storage/1.0/
- ↑ System Control Processor (SCP) firmware:
https://gitlab.arm.com/firmware/SCP-firmware - ↑ https://developer.arm.com/documentation/den0101/latest