1. Article purpose[edit source]
The main purpose of this article is to give main steps on how to enable security on MPU platforms.
2. Overview[edit source]
A STM32 MPU offers multiple ways to control and enforce security on the device. It exists some hardware and software mechanism that can be adapted by the users to set the MPU to the expected security level. These security protection mechanism are offers to users and fully customizable.
3. Device life cycle[edit source]
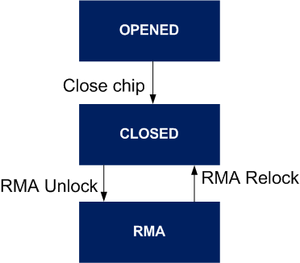
The STM32MP1 proposes different hardware state that manage different protection levels when changing state.
There are 3 modes defined at hardware level:
- OPEN state: By default the device is in open state. Authentication is not mandatory. It can be used to test authentication as error does not prevent FSBL from being started. Debugger is enabled with a limited access.
- CLOSED state: Once product secretsTODO link to keys have been provisioned into the device, it can be closed. On closed devices, authentication is mandatory. An authentication error prevents FSBL from being started. All debug access are default turn off.
- RMA state: A closed device can be put once in RMA state and back again in CLOSED state. When the device is in RMA state, all ROM code features are disabled.
On STM32MP15x lines ![]() , it is possible to go back to close state.
, it is possible to go back to close state.
4. Secure Boot[edit source]
The secure boot is essential to ensure the integrity and security of the platform at runtime.
The STM32 MPU trusted boot chain is designed to guarantee such a secure boot sequence.
It performs the following tasks:
- Configuration of the platform firewall, which is the foundation for a safe execution of the platform
- Configuration of the platform debug capabilities
- Verification of the integrity (thanks to a hash algorithm) and authentication (using asymmetric cryptography algorithms) of the started software components, including the Secure and non-secure worlds.
TF-A is the recommended open source bootloader. Its implementation supports the trusted boot and peripheral access control with firewall.
Once the STM32 MPU is in CLOSED state, the secure boot is enabled and cannot be bypass.
4.1. STM32MPU keys[edit source]
The secure boot relies on different keys fit the secure boot implementation.
STM32MP15x lines ![]() :
:
- PKH : Hash of the ECC Public Key (ECDSA is the authentication algorithm STM32MP15_OTP_mapping) used to compare the public root key. This file is automatically generated by the KeyGen_tool.
- ROM code used it to compare against the public key included in the STM32 header.
- TF-A BL2 used it to compare against the public root key from the trusted certificate.
- PKHTH : Hash of the 8 ECC Public Keys Hashes Table (ECDSA is the authentication algorithm STM32MP13_OTP_mapping) used to compare the public root key. This file is automatically generated by the KeyGen_tool.
- ROM code used it to compare against the public key table hash included in the STM32 header.
- TF-A BL2 used it to compare against the public key table hash included in the STM32 header.
- EDMK :
4.1.1. Provisionning[edit source]
4.1.1.1. U-Boot command stm32key[edit source]
U-Boot in OpenSTLinux embeds a stm32key command that can be called from U-Boot command line interface to manage the keys in OTPs.
stm32key help
stm32key - Manage key on STM32 Usage: stm32key list : list the supported key with description stm32key select [<key>] : Select the key identified by <key> or display the key used for read/fuse command stm32key read [<addr> | -a ] : Read the curent key at <addr> or current / all (-a) key in OTP stm32key fuse [-y] <addr> : Fuse the current key at addr in OTP stm32key close [-y] : Close the device, force use of PKH stored in OTP
The optional option -y is used to skip the confirmation message.
stm32key list PKHTH : Hash of the 8 ECC Public Keys Hashes Table (ECDSA is the authentication algorithm) OTP24..32 EDMK : Encryption/Decryption Master Key" OTP92..95
stm32key list PKH : Hash of the ECC Public Key (ECDSA is the authentication algorithm) OTP24..32
4.2. STM32MP1 secure boot[edit source]
The STM32MP1 secure boot implementation is described in :
- the STM32 MPU ROM code secure boot article for the ROM code authentication process based on STM32 header.
- the TF-A BL2 trusted board boot using FIP.
- the coprocessor authentication.
5. References[edit source]