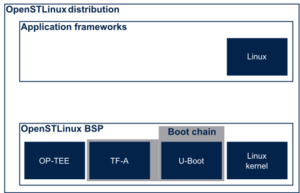
1. What's OP-TEE[edit source]
OP-TEE is an open source SW component hosted by [Firmware] organisation. It allows the development and integration of services and applications running on Cortex-A trusted execution environment (also called secure context), that is isolated from Cortex-A non-secure context running the Linux® -based OS.
Description extracted from the OP-TEE site[1]:
- "OP-TEE is a Trusted Execution Environment (TEE) designed as companion to a non-secure Linux kernel running on Arm; Cortex-A cores using the TrustZone technology. OP-TEE implements TEE Internal Core API v1.1.x which is the API exposed to Trusted Applications and the TEE Client API v1.0, which is the API describing how to communicate with a TEE. Those APIs are defined in the GlobalPlatform API specifications."
OP-TEE is delivered under a BSD style license and can run secure (trusted) applications, named TAs, without restriction on their licensing model.
For more details about OP-TEE open source project and internal architecture, please refer to OP-TEE overview (name to change)
The OP-TEE project is maintained by the Linaro Security Working Group.
GlobalPlatform Device TEE specifications (TEE Client API, TEE Internal Core API and few more) are available from the GlobalPlatform site[6].