1. Article purpose[edit source]
This article aims to explain, step by step, how to run the SSP process from the OEM secret generation till the chip provisioning. This example will use the STM32CubeProgrammer and its associated tools to manage the complete SSP.
2. OEM secret management[edit source]
The aim of SSP is to protect OEM secrets. It includes multiple secrets:
- Secrets that will be provisioned in OTP
- OEM authentication keys for Secure Boot
- OEM secrets encryption key
2.1. Key generation[edit source]
2.1.1. Authentication keys[edit source]
The initial keys to generate for STM32MP is the authentication keys. This is the root of trust of the STM32MP secure boot.
The PKH (on STM32MP15xC/F lines ![]() ) or PKHTH (on STM32MP13xC/F lines
) or PKHTH (on STM32MP13xC/F lines ![]() ) will be automatically install during the SSP process in the dedicated OTP.
) will be automatically install during the SSP process in the dedicated OTP.
To generate the keys (1 for STM32MP15, 8 for STM32MP13), you can use the KeyGen_tool:
Example to generate 1 ECC key pair (Prime256v1) using AES_256_cbc encryption:
STM32MP_KeyGen_CLI -abs /home/user/KeyFolder/ -pwd testkey
Example to generate 8 ECC key pair (Prime256v1) using AES_256_cbc encryption:
STM32MP_KeyGen_CLI -abs /home/user/KeyFolder/ -pwd testkey1 testkey2 testkey3 testkey4 testkey5 testkey6 testkey7 testkey8 -n 8
2.1.2. Encryption key[edit source]
The SSP process uses a symmetric encryption to hide OEM secrets exchange with the chip. This encryption/decryption uses a AES encryption scheme using:
- a 128 bit symmetric key
- a 128 bit nonce value
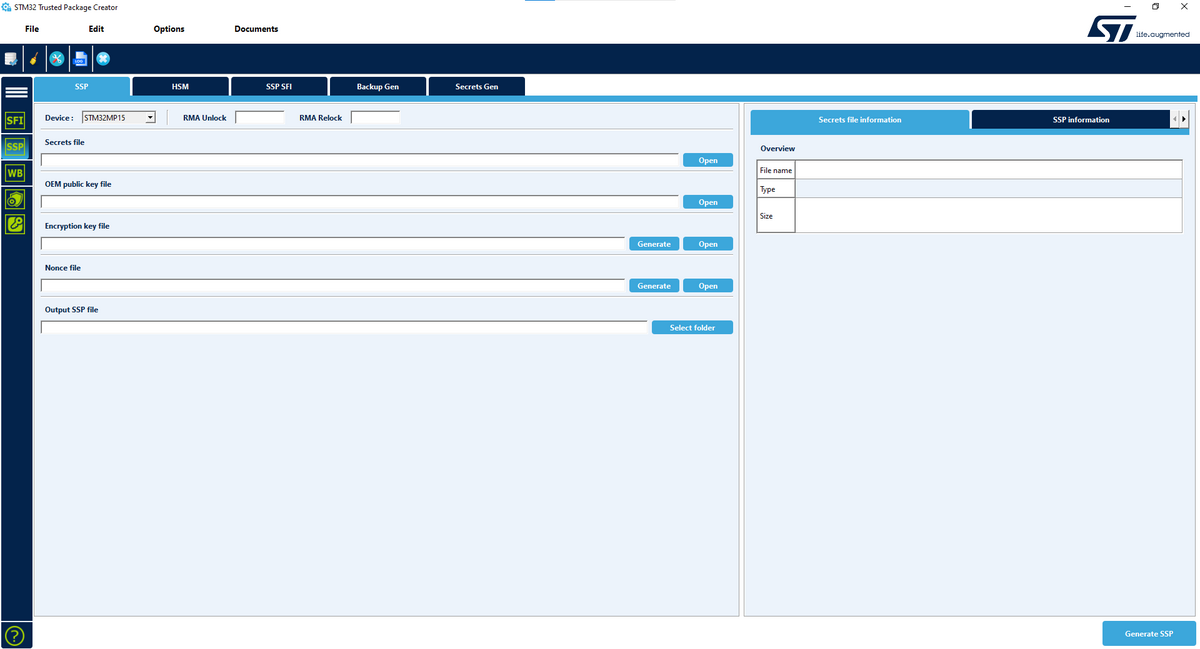
Both values will first be stored in the HSM and send to the chip using a unique chip encrypted flow. The two values can be directly generated with the STM32 Trusted Package Creator that will also manage the secret file encryption with the given key:
An alternative is to prepare both key using the KeyGen_tool (till version 2.12.0) with the command:
STM32MP_KeyGen_CLI -rand 16 enc_key.bin STM32MP_KeyGen_CLI -rand 16 nonce.bin
2.2. Secret file[edit source]
2.2.1. Secret file creation[edit source]
The secret file that must be generated by OEM must represent the OTP 59 to 95 On STM32MP1 series) named Free for user.
On STM32MP1 series:
- the words 57 and 58 are reserved for mac_address.
- the final file size must be (96 - 59) * 4 bytes = 148 bytes.
2.2.2. Secret file encryption[edit source]
The STM32 Trusted Package Creator is used to encrypted and prepare the final secret file used for provisioning. This encrypted final file will contains: - the PKH or PKHTH - the RMA password - the OEM secrets
All the previous generated keys must be properly selected in the STM32 Trusted Package Creator interface to generate the final encrypted file (.ssp). The chip and RMA password must be registered in the interface.
2.3. HSM provisioning[edit source]
The HSMv2[1] must be provisioned with the OEM associated SSP file.
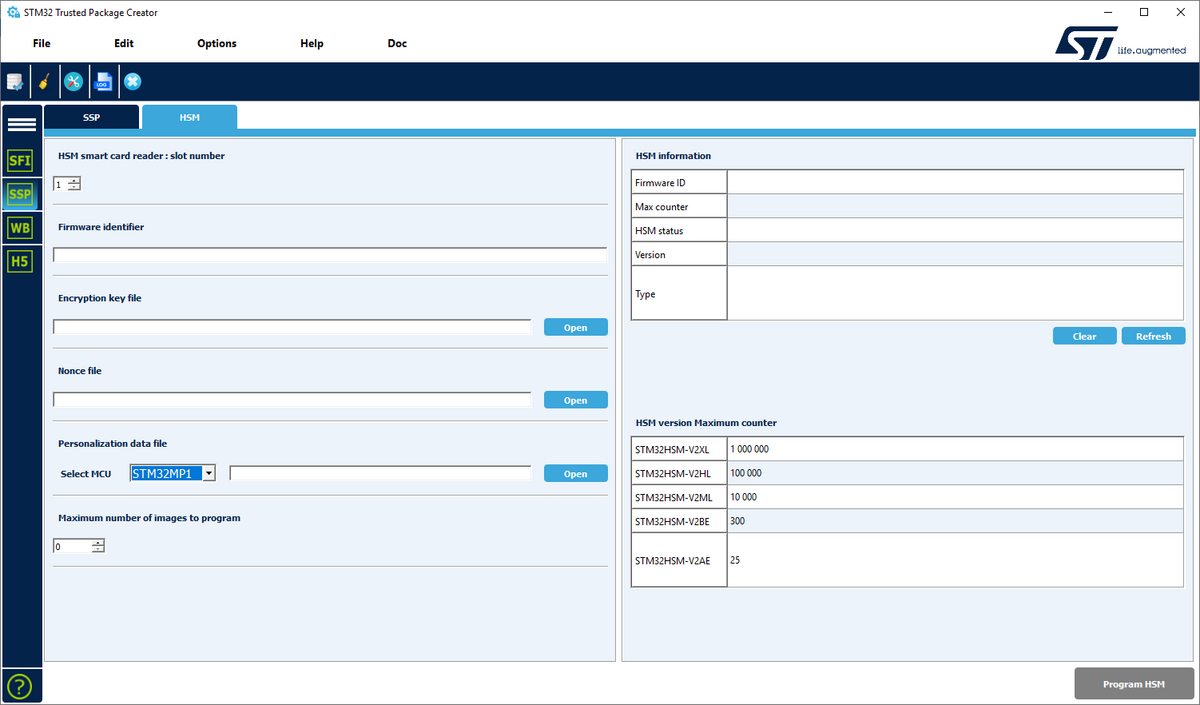
The STM32 Trusted Package Creator has a dedicated SSP HSM provisioning interface to select:
- the encryption key used to encrypt SSP secret file
- the nonce used to encrypt SSP secret file
- select the personalization data file (used to identify the chip):
- the maximum of image to program (depends also on the HSMv2 used).