Template:ArticleMainWriter Template:ArticleApprovedVersion
1. Purpose[edit source]
Secure boot is a key feature to guarantee a secure platform.
STM32MP1 boot sequence supports a trusted boot chain that ensures that the loaded images are authenticated and checked in integrity before being used.
2. Authentication processing[edit source]
2.1. STM32 Header[edit source]
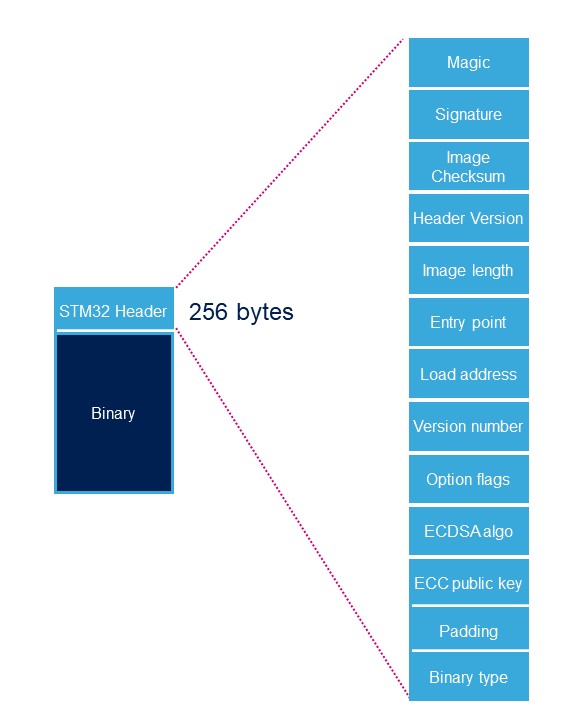
Each signed binary image includes a specific STM32 header added on top of the binary data. The header includes the authentication information.
| Name | Length | Byte Offset | Description |
|---|---|---|---|
| Magic number | 32 bits | 0 | ‘S’ ; ‘T’ ; ‘M’ ; 0x32 |
| Image Signature | 512 bits | 4 | ECDSA signature for image authentication1 |
| Image Checksum | 32 bits | 68 | Checksum of the payload2 |
| Header version | 32 bits | 72 | Header version v1.0 = 0x00010000 Byte0: reserved Byte1:major version = 0x01 Byte2: minor version = 0x00 Byte3: reserved |
| Image Length | 32 bits | 76 | Length of image in bytes3 |
| Image Entry Point | 32 bits | 80 | Entry point of image |
| Reserved1 | 32 bits | 84 | Reserved |
| Load address | 32 bits | 88 | Load address of image4 |
| Reserved2 | 32 bits | 92 | Reserved |
| Version Number | 32 bits | 96 | Image Version (monotonic number)5 |
| Option flags | 32 bits | 100 | b0=1: no signature verification6 |
| ECDSA Algorithm | 32 bits | 104 | 1: P-256 NIST ; 2: brainpool 256 |
| ECDSA Public key | 512 bits | 108 | ECDSA public key to be used to verify the signature.7 |
| PAD | 84 Bytes | 172 | Reserved padding bytes8. Must all be set to 0 |
- 1 Signature is calculated from first byte of header version field to last byte of image given by image length field.
- 2 32-bit sum of all payload bytes accessed as 8-bit unsigned numbers, discarding any overflow bits. Used to check the downloaded image integrity when signature is not used (if b0=1 in Option flags).
- 3 Length is the length of the built image, it does not include the length of the STM32 header.
- 4 This field is used by ROM code for specific executable images.
- 5 Image version is an anti rollback monotonic counter. The ROM code checks that it is higher or equal to the monotonic counter stored in OTP.
- 6 Enabling signature verification is mandatory on secure closed chips.
- 7 Hash of (algorithm+pubKey) is stored in OTP WORD 24 to 31.
- 8 This padding forces Header size to 0x100 bytes.
2.2. Verification[edit source]
STM32 MPU provides authentication processing with ECDSA [1] verification algorithm, based on ECC [2]. ECDSA offers better result than RSA with a smaller key. STM32 MPU relies on a 256 bits ECDSA key.
Two algorithms are supported for ECDSA calculation:
- P-256 NIST
- Brainpool 256
The EDCSA verification follows the process below:
The ROM code provides secure services to the FSBL for image authentication with the same ECC pair of keys, so there is no need to support ECDSA algorithm in FSBL.
OTP WORD 24 to 31 are used to store the public key hash (PKH).