1. Overview of the Trusted Firmware-M project[edit source]
Trusted Firmware-M (TF-M) is an open source project manage by TrustedFirmware group[1].
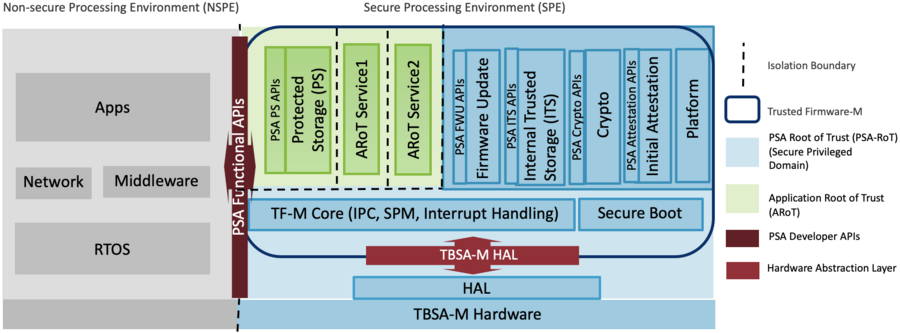
The software environment is design to run in the Secure Processing Environment (SPE) of ARMv8-M microcontrollers following the PSA Certified guidelines[2]
TF-M uses secure partitions that offers services. They can be isolated following different isolation levels:
- Level 1: SPE and NSPE isolation
- Level 2: Level 1 + Application Root of Trust (ARoT) protection from NSPE and PSA Root of Trust (PRoT) protection from NSPE and ARoT.
- Level 3: Level 2 + Secure partition protection from NSPE and other secure partitions. PSA Root of Trust (RoT) domain protection from NSPE and all Secure Partitions.
The default secure partitions that can be isolated to the non secure environment :
- Initial attestation
- Crypto services
- Internal trusted storage
- Firmware update
- Protected storage
The secure partitions are accessible using PSA dedicated API[3].
1.1. License[edit source]
TF-M is delivered under a BSD-3-Clause style license and can run secure partitions without restriction on their licensing model. It also includes different sub-projects with their dedicated license[4].
1.2. Architecture overview[edit source]
1.3. Software profile[edit source]
TF-M defines different profile offered to the user to select the security level targeted:
- Small profile
- ARot-IOT profile
- Medium profile
- Large
Each profile define a subset of services embedded in the TF-M software. They are listed in the table below:
| Option | Base | Small | ARoT-less | Medium | Large |
|---|---|---|---|---|---|
| TFM_ISOLATION_LEVEL | 1 | 1 | 1 | 2 | 3 |
| CONFIG_TFM_SPM_BACKEND | SFN | SFN | SFN | IPC | IPC |
| TFM_PARTITION_CRYPTO | OFF | ON | ON | ON | ON |
| TFM_PARTITION_INTERNAL_TRUSTED_STORAGE | OFF | ON | ON | ON | ON |
| TFM_PARTITION_PLATFORM | OFF | OFF | ON | ON | ON |
| TFM_PARTITION_PROTECTED_STORAGE | OFF | OFF | OFF | ON | ON |
| TFM_PARTITION_INITIAL_ATTESTATION | OFF | ON | ON | ON | ON |
| SYMMETRIC_INITIAL_ATTESTATION | OFF | ON | OFF | OFF | OFF |
| TFM_PARTITION_FIRMWARE_UPDATE | OFF | OFF | ON | OFF | OFF |
| PS_CRYPTO_AEAD_ALG | GCM | - | - | CCM | CCM |
| PSA_FRAMEWORK_HAS_MM_IOVEC | OFF | ON | OFF | OFF | OFF |
| MCUBOOT_IMAGE_NUMBER 1 | 2 | 1 | 2 | 2 | 2 |
| Advanced options, defined in the corresponded header (.h) file | |||||
| CRYPTO_ENGINE_BUF_SIZE | 0x2080 | 0x400 | 0x2080 | 0x2080 | 0x2380 |
| CRYPTO_ASYM_SIGN_MODULE_ENABLED | ON | OFF | ON | ON | ON |
| CRYPTO_ASYM_ENCRYPT_MODULE_ENABLED | ON | OFF | OFF | OFF | ON |
| CRYPTO_SINGLE_PART_FUNCS_DISABLED | OFF | ON | OFF | OFF | OFF |
| CRYPTO_CONC_OPER_NUM | 8 | 4 | 8 | 8 | 8 |
| CONFIG_TFM_CONN_HANDLE_MAX_NUM | 8 | 3 | 8 | 8 | 8 |
| ITS_BUF_SIZE 2 | 512 | 32 | 32 | 32 | 512 |
1.4. TF-M Core[edit source]
The TF-M core is the main part of the software that manages the secure partition manager, the scheduler and the inter-communication mechanism (IPC or SFN).
1.5. Secure boot[edit source]
The secure boot is driven by the BL2 boot level that is an external project MCUboot[5] used by TF-M to ensure the authentication and the decryption of the different slot that are loaded in memory.
1.6. Secure Partitions[edit source]
1.6.1. Crypto[edit source]
Crypto partitions offers PSA Crypto API[6] implementation in a dedicated RoT secure partition. The implementation is base on mbed crypto[7]
1.6.2. Firmware update[edit source]
The Firmware update partition implements the PSA Firmware update API [8]. It gives all the mandatory features to authenticate, verify and install a new updated image and manage the security about the update process.
1.6.3. Initial attestation[edit source]
Initial attestation partition implement the PSA Attestation API [9]. It provides a verifiable report of the state of the platform.
1.6.4. Internal trusted storage[edit source]
ITS implements PSA secure storage API [10]. The internal storage is design to store the most secure and critical assets used by the RoT.
1.6.5. Protected storage[edit source]
Secure partition in the ARoT that implements the PSA secure storage API [10] and allows to store secure data on external storage.
1.7. TF-M on target[edit source]
On STM32MP2 series, the TF-M can be used on the Cortex-M processor. TF-M must run in the Trustzone area.
When Cortex-A is the main processor, for security reason, the TF-M has to be started following the secure coprocessor loading process.
2. References[edit source]
- ↑ https://www.trustedfirmware.org/projects/tf-m
- ↑ https://www.psacertified.org
- ↑ https://www.psacertified.org/getting-certified/functional-api-certification/
- ↑ https://tf-m-user-guide.trustedfirmware.org/introduction/readme.html
- ↑ https://docs.mcuboot.com/
- ↑ https://arm-software.github.io/psa-api/crypto/
- ↑ https://github.com/Mbed-TLS
- ↑ https://arm-software.github.io/psa-api/fwu/
- ↑ https://arm-software.github.io/psa-api/attestation/1.0/
- ↑ 10.0 10.1 https://arm-software.github.io/psa-api/storage/1.0/