This page reports measured performance when using the pure software cryptographic library algorithms with an STM32L4 MCU. In addition to performance figures, the required code footprint and memory are also given.
1. Measurement configuration
1.1. Hardware configuration
| STM32 MCU | STM32L476RGT6 |
| Device ID | 0x415 |
| Revision ID | 0x1007 |
| Board | STM32L476RG-Nucleo Rev C |
1.2. Firmware configuration
| Cryptographic Library version | 040000B1[ver. 1] |
- ↑ This value corresponds to the information returned by a call to cmox_getInfos
1.3. System configuration
| System Core Clock Frequency | 80 MHz |
| Flash latency | 4 wait states |
| Voltage scaling | Range 1 |
| Instruction Cache (ART/ICU) | 1 (0: disabled / 1: enabled) |
| Data Cache (ART/DCU) | 1 (0: disabled / 1: enabled) |
| Prefetch Cache (ART) | 1 (0: disabled / 1: enabled) |
1.4. Development toolchains and compilers
| IAR Embedded Workbench | IAR ANSI C/C++ Compiler V8.50.4.261/W32 for ARM |
2. Performance values
2.1. AES symmetric key encryption & decryption
This section provides the performance results for AES-CBC using different modes of operation:
- Sole buffer: one sole buffer is encrypted or decrypted. Time to perform is given in µs.
- Data flow: a big message is encrypted or decrypted by chunk. Bit rate is given in kilobytes per second.
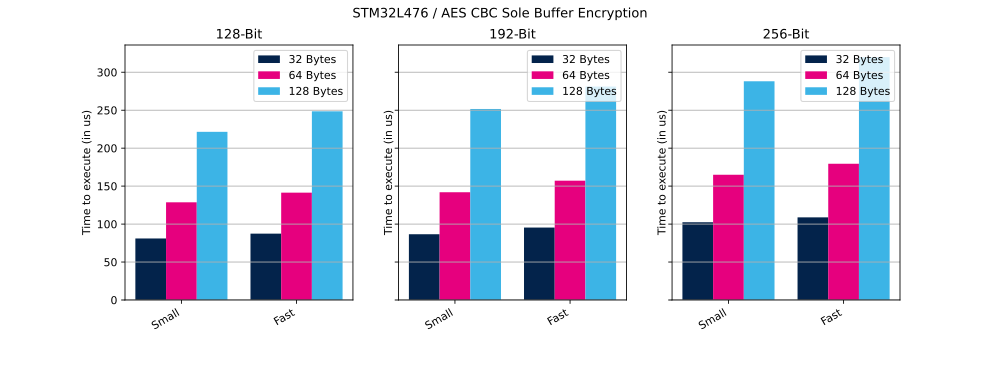
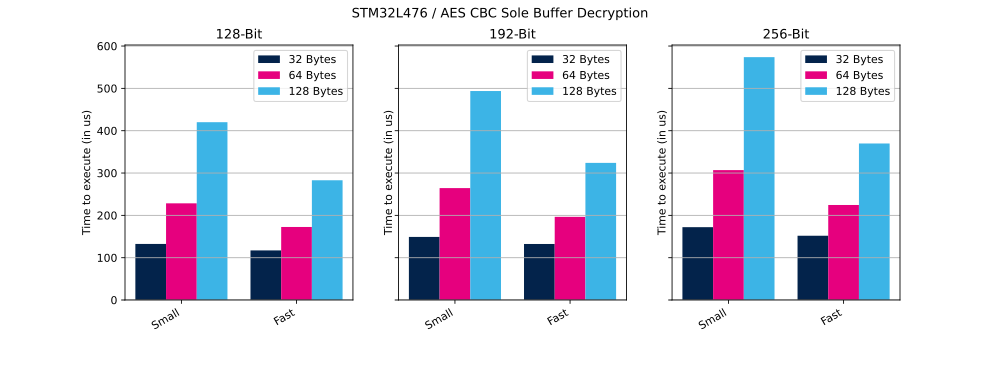
2.1.1. Sole buffer mode
In this mode the entire encryption or decryption process, for the whole message size, is managed through a single API call provided by the CMOX library.
The table below shows the number of clock cycles and time (in µs) needed to perform the described operation in small and fast configurations.
| AES mode | Key size | Buffer size | Cipher operation | Configuration | Cycles | Time |
|---|---|---|---|---|---|---|
| AES CBC | 128 bits | 32 bytes | Encryption | Small | 6484 | 81 µs |
| AES CBC | 128 bits | 32 bytes | Encryption | Fast | 6993 | 87 µs |
| AES CBC | 128 bits | 64 bytes | Encryption | Small | 10 295 | 128 µs |
| AES CBC | 128 bits | 64 bytes | Encryption | Fast | 11 312 | 141 µs |
| AES CBC | 128 bits | 128 bytes | Encryption | Small | 17 722 | 221 µs |
| AES CBC | 128 bits | 128 bytes | Encryption | Fast | 19 885 | 248 µs |
| AES CBC | 192 bits | 32 bytes | Encryption | Small | 6930 | 86 µs |
| AES CBC | 192 bits | 32 bytes | Encryption | Fast | 7634 | 95 µs |
| AES CBC | 192 bits | 64 bytes | Encryption | Small | 11 356 | 141 µs |
| AES CBC | 192 bits | 64 bytes | Encryption | Fast | 12 573 | 157 µs |
| AES CBC | 192 bits | 128 bytes | Encryption | Small | 20 130 | 251 µs |
| AES CBC | 192 bits | 128 bytes | Encryption | Fast | 22 494 | 281 µs |
| AES CBC | 256 bits | 32 bytes | Encryption | Small | 8194 | 102 µs |
| AES CBC | 256 bits | 32 bytes | Encryption | Fast | 8709 | 108 µs |
| AES CBC | 256 bits | 64 bytes | Encryption | Small | 13 199 | 164 µs |
| AES CBC | 256 bits | 64 bytes | Encryption | Fast | 14 358 | 179 µs |
| AES CBC | 256 bits | 128 bytes | Encryption | Small | 23 050 | 288 µs |
| AES CBC | 256 bits | 128 bytes | Encryption | Fast | 25 593 | 319 µs |
| AES CBC | 128 bits | 32 bytes | Decryption | Small | 10 596 | 132 µs |
| AES CBC | 128 bits | 32 bytes | Decryption | Fast | 9371 | 117 µs |
| AES CBC | 128 bits | 64 bytes | Decryption | Small | 18 270 | 228 µs |
| AES CBC | 128 bits | 64 bytes | Decryption | Fast | 13 802 | 172 µs |
| AES CBC | 128 bits | 128 bytes | Decryption | Small | 33 605 | 420 µs |
| AES CBC | 128 bits | 128 bytes | Decryption | Fast | 22 630 | 282 µs |
| AES CBC | 192 bits | 32 bytes | Decryption | Small | 11 921 | 149 µs |
| AES CBC | 192 bits | 32 bytes | Decryption | Fast | 10 588 | 132 µs |
| AES CBC | 192 bits | 64 bytes | Decryption | Small | 21 150 | 264 µs |
| AES CBC | 192 bits | 64 bytes | Decryption | Fast | 15 718 | 196 µs |
| AES CBC | 192 bits | 128 bytes | Decryption | Small | 39 497 | 493 µs |
| AES CBC | 192 bits | 128 bytes | Decryption | Fast | 25 916 | 323 µs |
| AES CBC | 256 bits | 32 bytes | Decryption | Small | 13 765 | 172 µs |
| AES CBC | 256 bits | 32 bytes | Decryption | Fast | 12 145 | 151 µs |
| AES CBC | 256 bits | 64 bytes | Decryption | Small | 24 549 | 306 µs |
| AES CBC | 256 bits | 64 bytes | Decryption | Fast | 17 958 | 224 µs |
| AES CBC | 256 bits | 128 bytes | Decryption | Small | 45 901 | 573 µs |
| AES CBC | 256 bits | 128 bytes | Decryption | Fast | 29 581 | 369 µs |
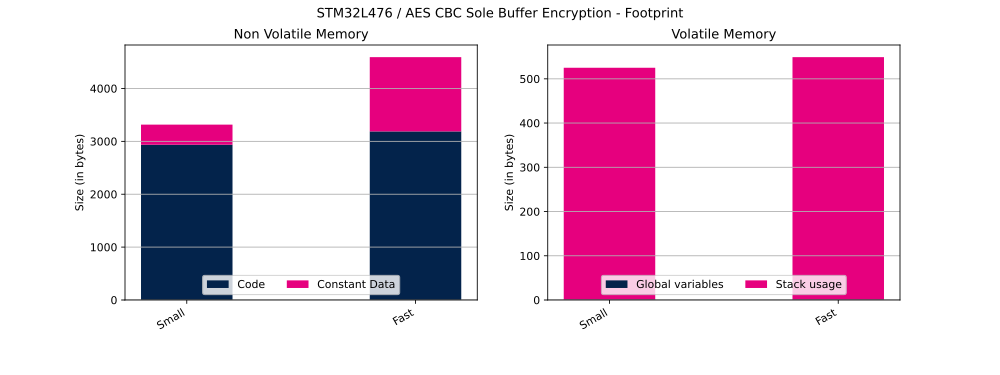
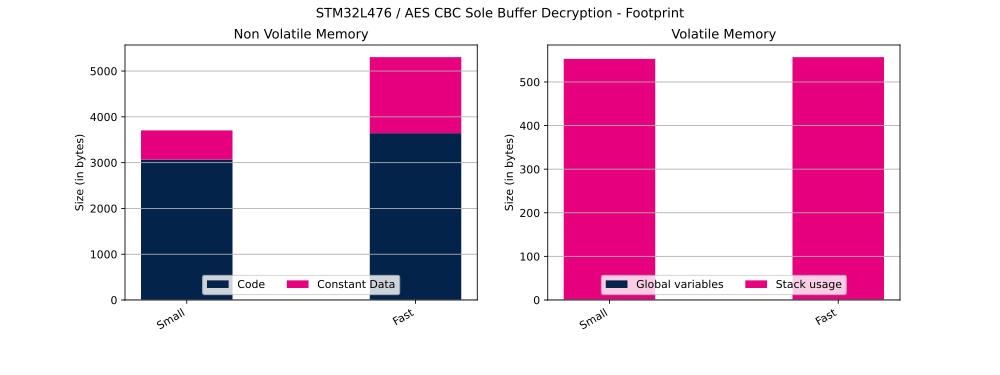
The table below shows Flash and RAM usage (in bytes).
| Cipher operation | Configuration | Code | Constant data | Global data | Stack usage |
|---|---|---|---|---|---|
| Encryption | Small | 2936 bytes | 380 bytes | 1 bytes | 524 bytes |
| Encryption | Fast | 3188 bytes | 1404 bytes | 1 bytes | 548 bytes |
| Decryption | Small | 3068 bytes | 636 bytes | 1 bytes | 552 bytes |
| Decryption | Fast | 3644 bytes | 1660 bytes | 1 bytes | 556 bytes |
2.1.2. Data flow mode
In this mode, operation is performed in several calls to the CMOX library APIs, as below:
- cmox_cipher_init
- cmox_cipher_setKey
- cmox_cipher_setIV
- cmox_cipher_append: called several times to encrypt or decrypt the whole message by chunk of fixed size
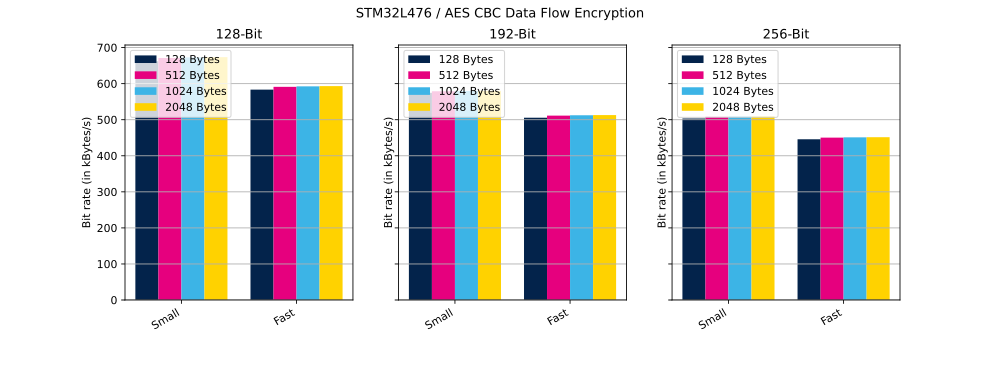
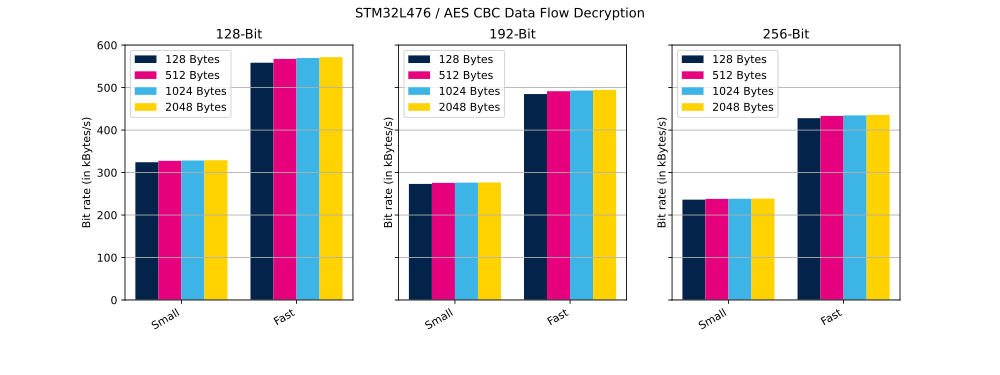
The table below shows the number of clock cycles and bit rate (in kilobytes per second) needed to perform described operation in small and in fast configuration.
| AES mode | Key size | Message size | Chunk size | Cipher operation | Configuration | Cycles | Bit rate |
|---|---|---|---|---|---|---|---|
| AES CBC | 128 bits | 8000 bytes | 128 bytes | Encryption | Small | 966 832 | 661 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 128 bytes | Encryption | Fast | 1 097 208 | 583 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 512 bytes | Encryption | Small | 953 736 | 671 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 512 bytes | Encryption | Fast | 1 082 816 | 591 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 1024 bytes | Encryption | Small | 951 504 | 672 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 1024 bytes | Encryption | Fast | 1 080 368 | 592 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 2048 bytes | Encryption | Small | 950 432 | 673 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 2048 bytes | Encryption | Fast | 1 079 152 | 593 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 128 bytes | Encryption | Small | 1 114 096 | 574 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 128 bytes | Encryption | Fast | 1 266 304 | 505 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 512 bytes | Encryption | Small | 1 105 760 | 578 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 512 bytes | Encryption | Fast | 1 251 912 | 511 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 1024 bytes | Encryption | Small | 1 104 240 | 579 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 1024 bytes | Encryption | Fast | 1 249 456 | 512 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 2048 bytes | Encryption | Small | 1 103 576 | 579 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 2048 bytes | Encryption | Fast | 1 248 232 | 512 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 128 bytes | Encryption | Small | 1 271 672 | 503 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 128 bytes | Encryption | Fast | 1 436 048 | 445 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 512 bytes | Encryption | Small | 1 258 896 | 508 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 512 bytes | Encryption | Fast | 1 421 552 | 450 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 1024 bytes | Encryption | Small | 1 256 712 | 509 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 1024 bytes | Encryption | Fast | 1 419 104 | 450 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 2048 bytes | Encryption | Small | 1 255 648 | 509 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 2048 bytes | Encryption | Fast | 1 417 864 | 451 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 128 bytes | Decryption | Small | 1 973 416 | 324 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 128 bytes | Decryption | Fast | 1 145 800 | 558 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 512 bytes | Decryption | Small | 1 953 560 | 327 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 512 bytes | Decryption | Fast | 1 127 760 | 567 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 1024 bytes | Decryption | Small | 1 949 088 | 328 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 1024 bytes | Decryption | Fast | 1 123 528 | 569 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 2048 bytes | Decryption | Small | 1 944 896 | 329 kbyte/s |
| AES CBC | 128 bits | 8000 bytes | 2048 bytes | Decryption | Fast | 1 119 480 | 571 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 128 bytes | Decryption | Small | 2 341 896 | 273 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 128 bytes | Decryption | Fast | 1 320 088 | 484 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 512 bytes | Decryption | Small | 2 321 328 | 275 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 512 bytes | Decryption | Fast | 1 302 072 | 491 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 1024 bytes | Decryption | Small | 2 316 696 | 276 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 1024 bytes | Decryption | Fast | 1 297 832 | 493 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 2048 bytes | Decryption | Small | 2 312 440 | 276 kbyte/s |
| AES CBC | 192 bits | 8000 bytes | 2048 bytes | Decryption | Fast | 1 293 792 | 494 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 128 bytes | Decryption | Small | 2 709 424 | 236 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 128 bytes | Decryption | Fast | 1 495 328 | 427 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 512 bytes | Decryption | Small | 2 689 440 | 237 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 512 bytes | Decryption | Fast | 1 477 128 | 433 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 1024 bytes | Decryption | Small | 2 685 016 | 238 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 1024 bytes | Decryption | Fast | 1 472 864 | 434 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 2048 bytes | Decryption | Small | 2 680 880 | 238 kbyte/s |
| AES CBC | 256 bits | 8000 bytes | 2048 bytes | Decryption | Fast | 1 468 800 | 435 kbyte/s |
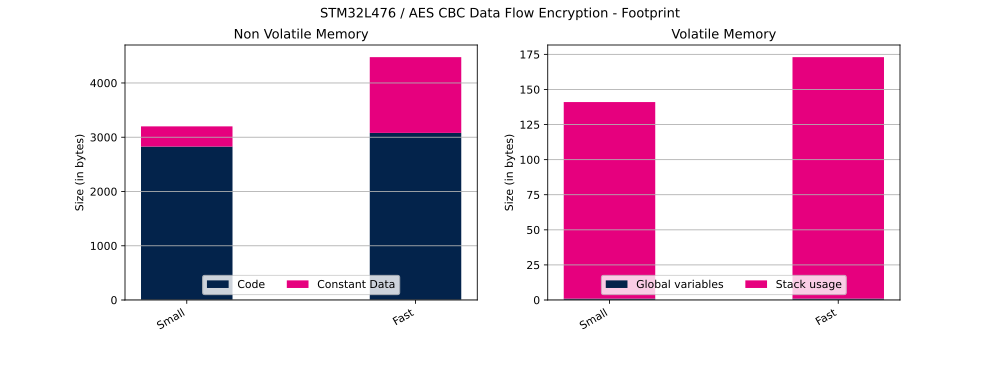
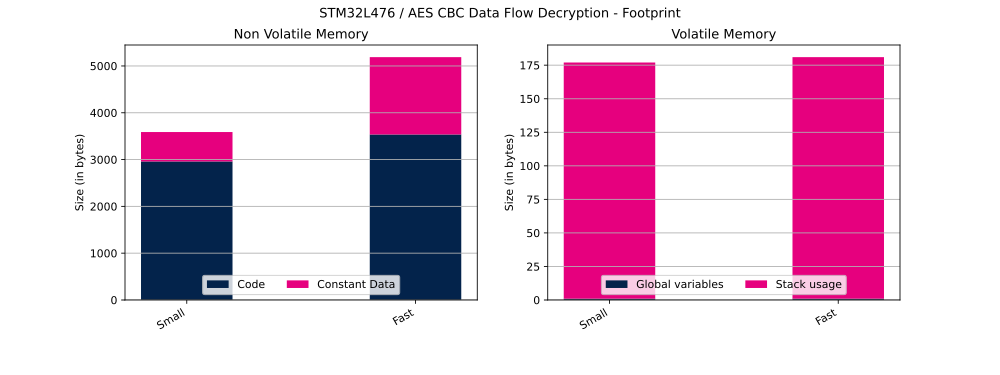
The table below shows Flash and RAM usage (in bytes).
| Cipher operation | Configuration | Code | Constant data | Global data | Stack usage |
|---|---|---|---|---|---|
| Encryption | Small | 2828 bytes | 372 bytes | 1 bytes | 140 bytes |
| Encryption | Fast | 3080 bytes | 1396 bytes | 1 bytes | 172 bytes |
| Decryption | Small | 2960 bytes | 628 bytes | 1 bytes | 176 bytes |
| Decryption | Fast | 3536 bytes | 1652 bytes | 1 bytes | 180 bytes |
2.2. HASH digest
In this section we provide the performance results for HASH using different modes of operation:
- Sole buffer: one sole buffer is hashed. Time to perform is given in us.
- Data flow: a big message is hashed by chunk. Bit rate is given in bytes per s.
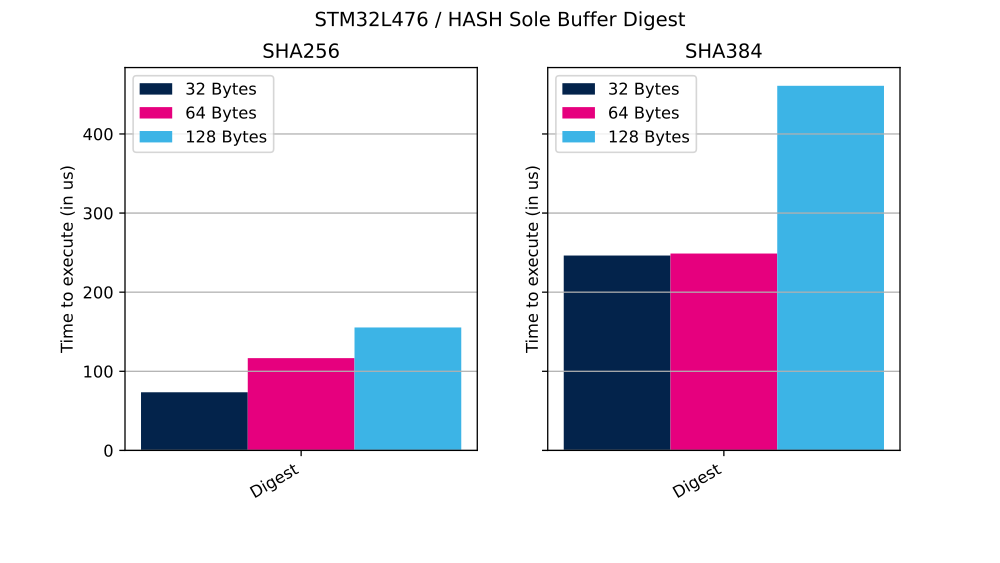
2.2.1. Sole buffer mode
In this mode, the entire message hashing process is managed through a single API call provided by the CMOX library.
The table below shows the number of clock cycles and time (in µs) needed to perform described operation.
| HASH mode | Buffer size | Cycles | Time |
|---|---|---|---|
| SHA256 | 32 bytes | 5878 | 73 µs |
| SHA256 | 64 bytes | 9333 | 116 µs |
| SHA256 | 128 bytes | 12 434 | 155 µs |
| SHA384 | 32 bytes | 19 703 | 246 µs |
| SHA384 | 64 bytes | 19 909 | 248 µs |
| SHA384 | 128 bytes | 36 871 | 460 µs |
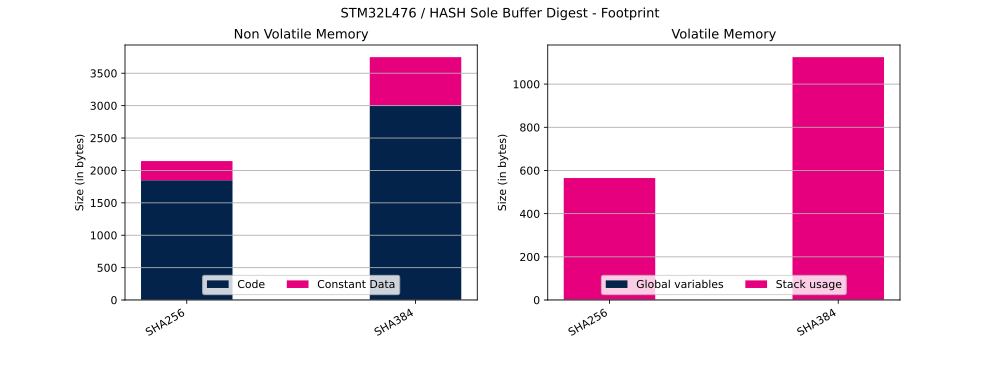
The table below shows Flash and RAM usage (in bytes).
| HASH mode | Code | Constant data | Global data | Stack usage |
|---|---|---|---|---|
| SHA256 | 1848 | 296 bytes | 1 bytes | 564 bytes |
| SHA384 | 3004 | 744 bytes | 1 bytes | 1124 bytes |
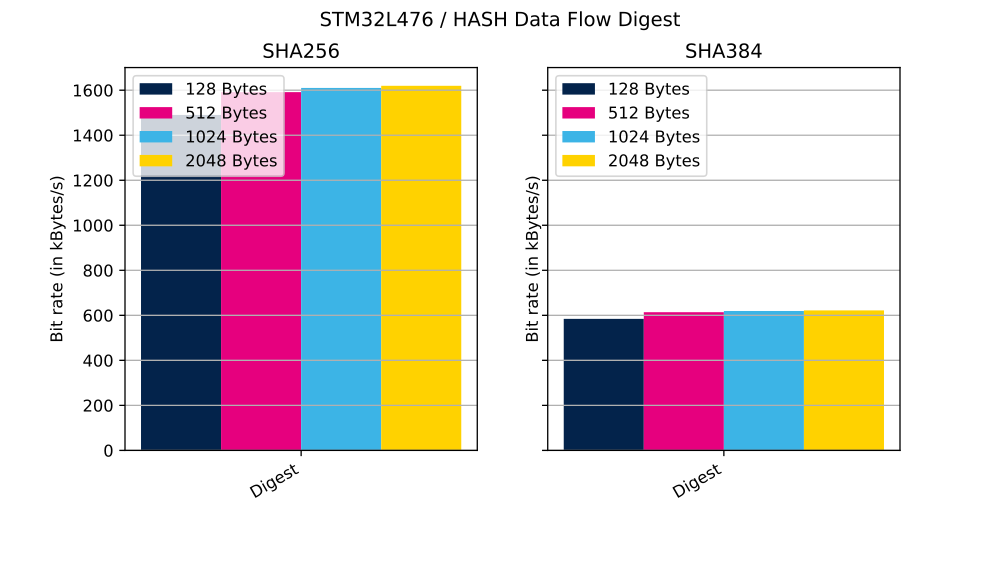
2.2.2. Data flow mode
In this mode, operation is performed in several calls to the CMOX library APIs, as below:
- cmox_hash_init
- cmox_hash_append: called several times to hash the whole message by chunk of fixed size
- cmox_hash_generateTag
The table below shows the number of clock cycles and bit rate (in kilobytes per second) needed to perform described operation.
| HASH mode | Message size | Chunk size | Cycles | Bit rate |
|---|---|---|---|---|
| SHA256 | 8000 bytes | 128 bytes | 429 503 | 1490 kbyte/s |
| SHA256 | 8000 bytes | 512 bytes | 402 149 | 1591 kbyte/s |
| SHA256 | 8000 bytes | 1024 bytes | 397 493 | 1610 kbyte/s |
| SHA256 | 8000 bytes | 2048 bytes | 395 165 | 1619 kbyte/s |
| SHA384 | 8000 bytes | 128 bytes | 1 095 542 | 584 kbyte/s |
| SHA384 | 8000 bytes | 512 bytes | 1 042 745 | 613 kbyte/s |
| SHA384 | 8000 bytes | 1024 bytes | 1 033 593 | 619 kbyte/s |
| SHA384 | 8000 bytes | 2048 bytes | 1 029 017 | 621 kbyte/s |
The table below shows final tag generation done through the call to cmox_hash_generateTag.
| HASH mode | Cycles | Time |
|---|---|---|
| SHA256 | 4766 | 59 µs |
| SHA384 | 18 346 | 229 µs |
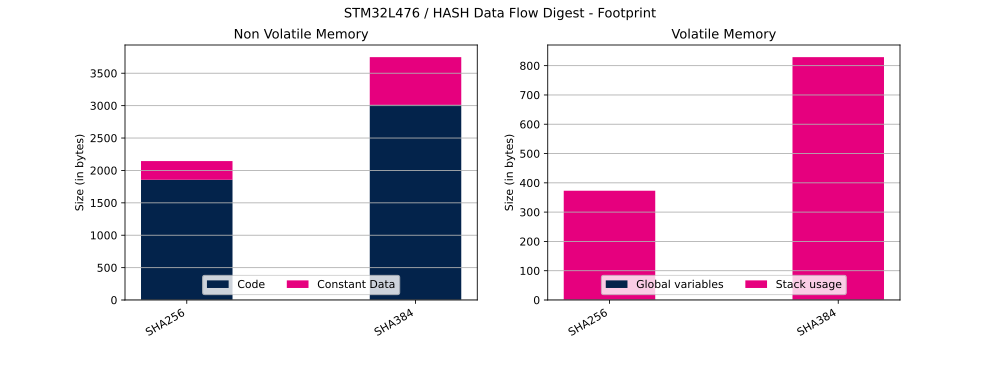
The table below shows Flash and RAM usage (in bytes).
| HASH mode | Code | Constant data | Global data | Stack usage |
|---|---|---|---|---|
| SHA256 | 1856 bytes | 288 bytes | 1 bytes | 372 bytes |
| SHA384 | 3012 bytes | 736 bytes | 1 bytes | 828 bytes |
2.3. ECDSA signature & verification
In this section we provide the performance results for ECDSA signature & verification.
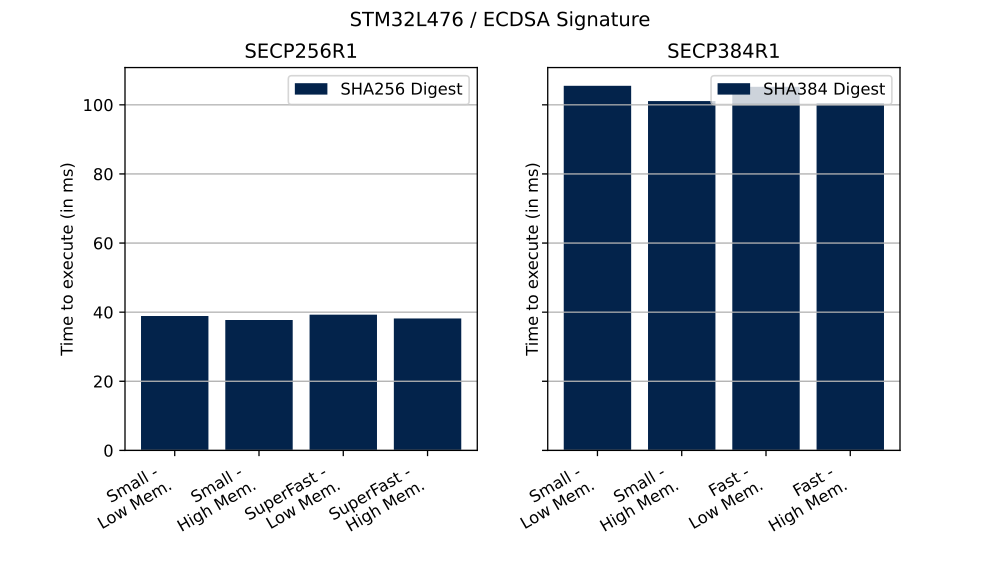
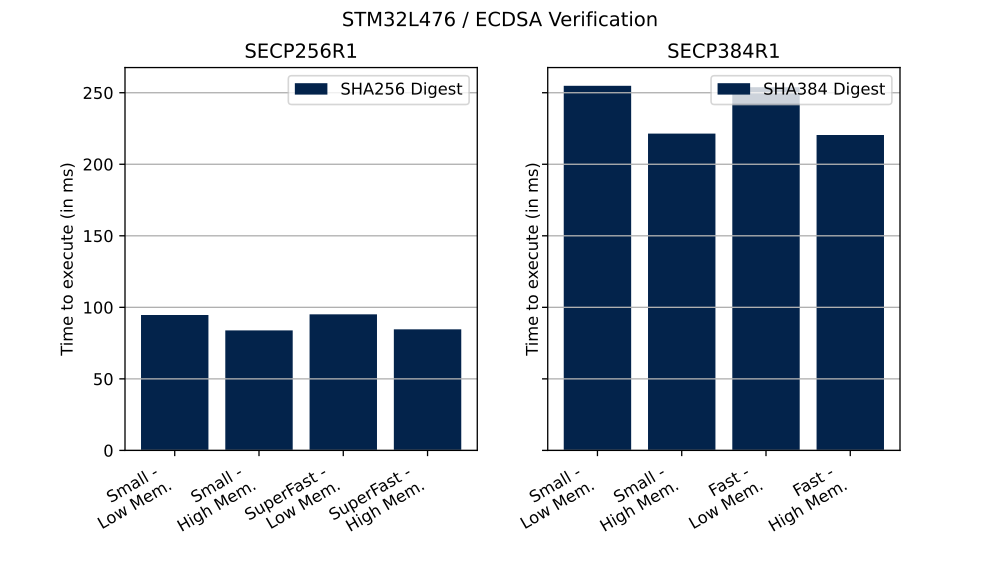
The table below shows the number of clock cycles and time (in ms) needed to perform described operation in different configurations.
| Curve | Operation | ECC mathematics configuration | Curve definition | Cycles | Time |
|---|---|---|---|---|---|
| SECP256R1 | Signature | Small | Low | 3 110 704 | 38 ms |
| SECP256R1 | Signature | Small | High | 3 019 288 | 37 ms |
| SECP256R1 | Signature | SuperFast | Low | 3 142 208 | 39 ms |
| SECP256R1 | Signature | SuperFast | High | 3 055 024 | 38 ms |
| SECP256R1 | Verification | Small | Low | 7 572 160 | 94 ms |
| SECP256R1 | Verification | Small | High | 6 710 744 | 83 ms |
| SECP256R1 | Verification | SuperFast | Low | 7 606 584 | 95 ms |
| SECP256R1 | Verification | SuperFast | High | 6 767 896 | 84 ms |
| SECP384R1 | Signature | Small | Low | 8 440 616 | 105 ms |
| SECP384R1 | Signature | Small | High | 8 087 160 | 101 ms |
| SECP384R1 | Signature | Fast | Low | 8 416 504 | 105 ms |
| SECP384R1 | Signature | Fast | High | 8 034 424 | 100 ms |
| SECP384R1 | Verification | Small | Low | 20 387 224 | 254 ms |
| SECP384R1 | Verification | Small | High | 17 715 128 | 221 ms |
| SECP384R1 | Verification | Fast | Low | 20 307 552 | 253 ms |
| SECP384R1 | Verification | Fast | High | 17 633 912 | 220 ms |
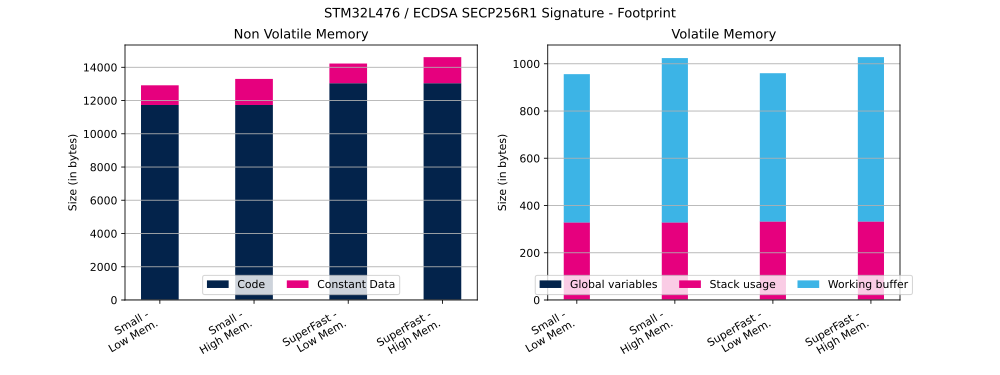
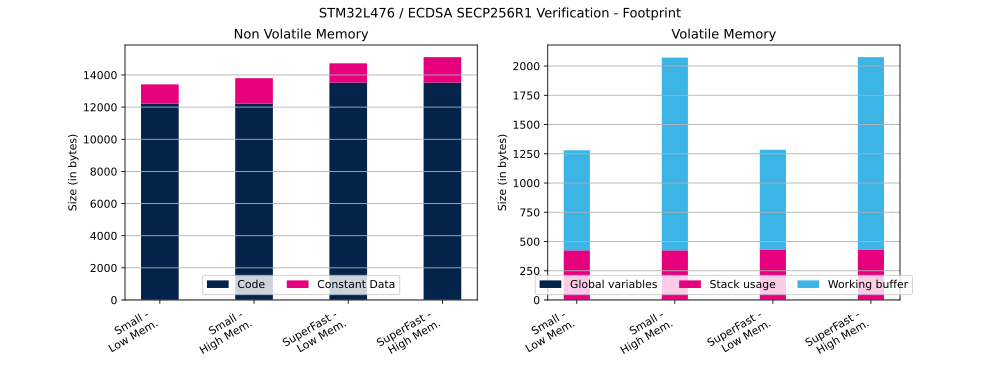
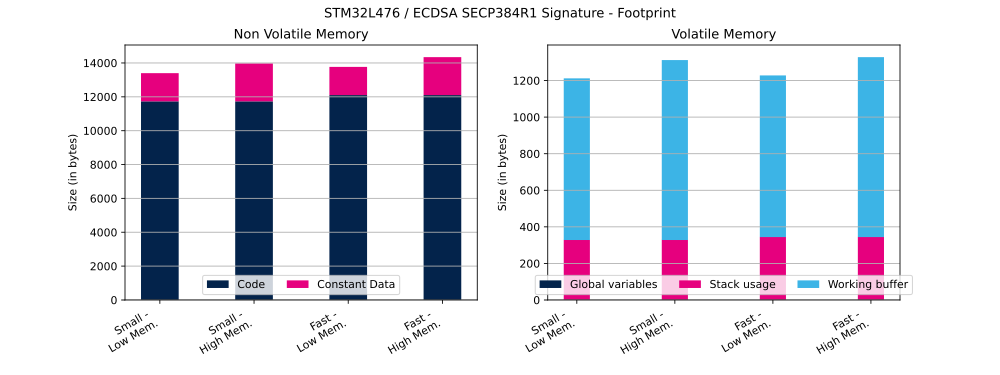
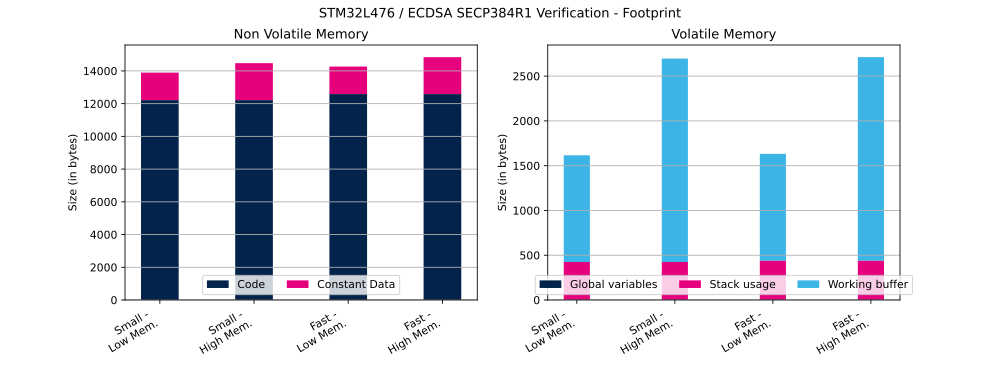
The table below shows ECDSA Flash and RAM usage (in bytes).
| Curve | Operation | ECC mathematics configuration | Curve definition | Code | Constant data | Global data | Stack usage | Working buffer |
|---|---|---|---|---|---|---|---|---|
| SECP256R1 | Signature | Small | Low | 11 732 bytes | 1184 bytes | 1 bytes | 328 bytes | 628 bytes |
| SECP256R1 | Signature | Small | High | 11 732 bytes | 1568 bytes | 1 bytes | 328 bytes | 696 bytes |
| SECP256R1 | Signature | SuperFast | Low | 13 042 bytes | 1184 bytes | 1 bytes | 332 bytes | 628 bytes |
| SECP256R1 | Signature | SuperFast | High | 13 042 bytes | 1568 bytes | 1 bytes | 332 bytes | 696 bytes |
| SECP256R1 | Verification | Small | Low | 12 216 bytes | 1200 bytes | 1 bytes | 424 bytes | 856 bytes |
| SECP256R1 | Verification | Small | High | 12 216 bytes | 1584 bytes | 1 bytes | 424 bytes | 1648 bytes |
| SECP256R1 | Verification | SuperFast | Low | 13 526 bytes | 1200 bytes | 1 bytes | 428 bytes | 856 bytes |
| SECP256R1 | Verification | SuperFast | High | 13 526 bytes | 1584 bytes | 1 bytes | 428 bytes | 1648 bytes |
| SECP384R1 | Signature | Small | Low | 11 732 bytes | 1664 bytes | 1 bytes | 328 bytes | 884 bytes |
| SECP384R1 | Signature | Small | High | 11 732 bytes | 2240 bytes | 1 bytes | 328 bytes | 984 bytes |
| SECP384R1 | Signature | Fast | Low | 12 102 bytes | 1664 bytes | 1 bytes | 344 bytes | 884 bytes |
| SECP384R1 | Signature | Fast | High | 12 102 bytes | 2240 bytes | 1 bytes | 344 bytes | 984 bytes |
| SECP384R1 | Verification | Small | Low | 12 216 bytes | 1680 bytes | 1 bytes | 424 bytes | 1192 bytes |
| SECP384R1 | Verification | Small | High | 12 216 bytes | 2256 bytes | 1 bytes | 424 bytes | 2272 bytes |
| SECP384R1 | Verification | Fast | Low | 12 586 bytes | 1680 bytes | 1 bytes | 440 bytes | 1192 bytes |
| SECP384R1 | Verification | Fast | High | 12 586 bytes | 2256 bytes | 1 bytes | 440 bytes | 2272 bytes |
2.4. EdDSA signature & verification
In this section we provide the performance results for EdDSA signature & verification.
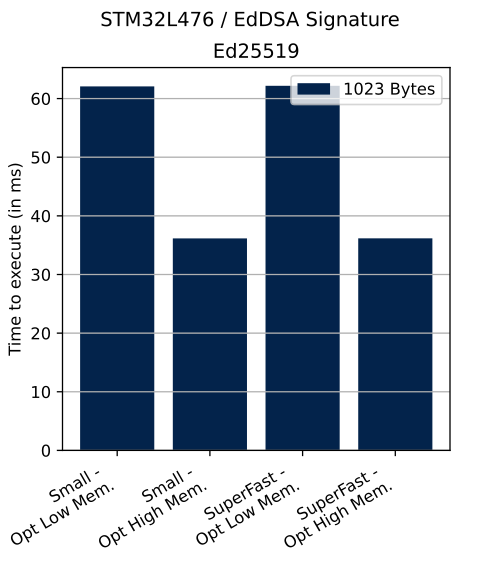
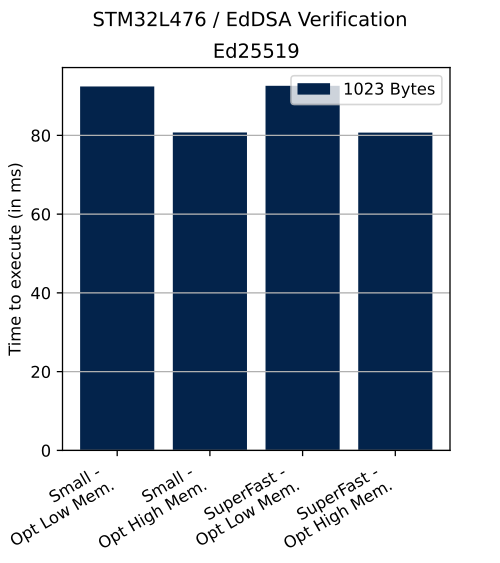
The table below shows the number of clock cycles and time (in ms) needed to perform described operation in different configurations.
| Curve | Message size | Operation | ECC mathematics configuration | Curve definition | Cycles | Time |
|---|---|---|---|---|---|---|
| Ed25519 | 1023 bytes | Signature | Small | OptLow | 4 966 168 | 62 ms |
| Ed25519 | 1023 bytes | Signature | Small | OptHigh | 2 892 016 | 36 ms |
| Ed25519 | 1023 bytes | Signature | SuperFast | OptLow | 4 974 464 | 62 ms |
| Ed25519 | 1023 bytes | Signature | SuperFast | OptHigh | 2 893 096 | 36 ms |
| Ed25519 | 1023 bytes | Verification | Small | OptLow | 7 393 224 | 92 ms |
| Ed25519 | 1023 bytes | Verification | Small | OptHigh | 6 459 280 | 80 ms |
| Ed25519 | 1023 bytes | Verification | SuperFast | OptLow | 7 406 968 | 92 ms |
| Ed25519 | 1023 bytes | Verification | SuperFast | OptHigh | 6 456 536 | 80 ms |
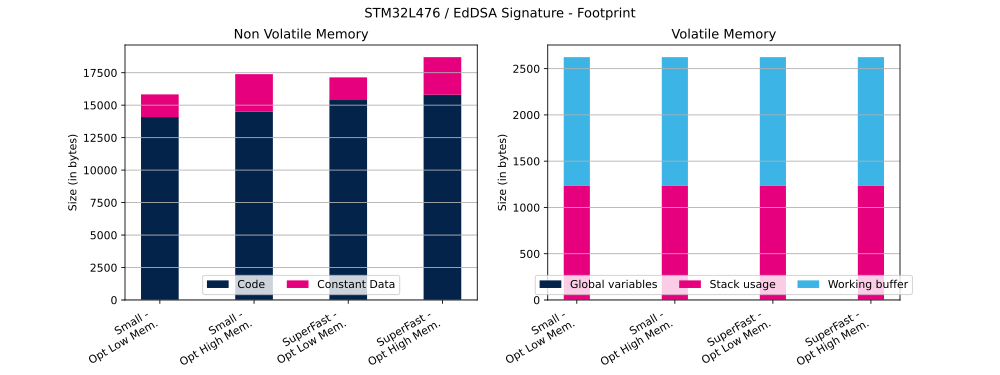
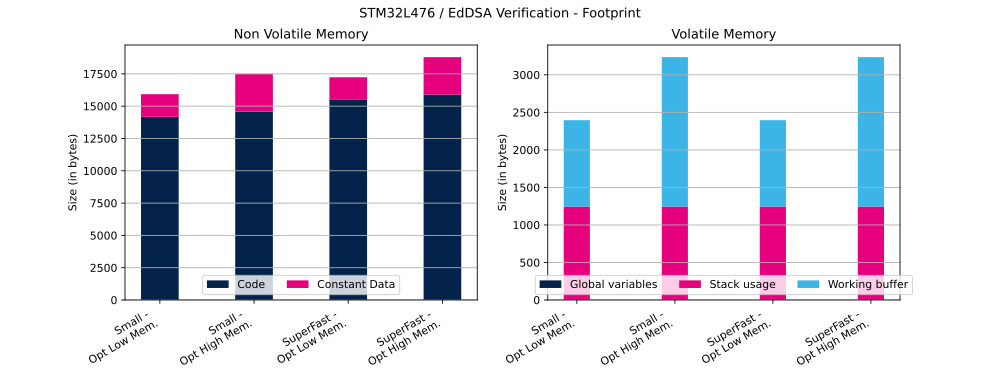
The table below shows EdDSA Flash and RAM usage (in bytes).
| Curve | Message size | Operation | ECC mathematics configuration | Curve definition | Code | Constant data | Global data | Stack usage | Working buffer |
|---|---|---|---|---|---|---|---|---|---|
| Ed25519 | 1023 bytes | Signature | Small | OptLow | 14 088 bytes | 1744 bytes | 1 bytes | 1236 bytes | 1388 bytes |
| Ed25519 | 1023 bytes | Signature | Small | OptHigh | 14 494 bytes | 2896 bytes | 1 bytes | 1236 bytes | 1388 bytes |
| Ed25519 | 1023 bytes | Signature | SuperFast | OptLow | 15 398 bytes | 1744 bytes | 1 bytes | 1236 bytes | 1388 bytes |
| Ed25519 | 1023 bytes | Signature | SuperFast | OptHigh | 15 804 bytes | 2896 bytes | 1 bytes | 1236 bytes | 1388 bytes |
| Ed25519 | 1023 bytes | Verification | Small | OptLow | 14 178 bytes | 1748 bytes | 1 bytes | 1244 bytes | 1152 bytes |
| Ed25519 | 1023 bytes | Verification | Small | OptHigh | 14 584 bytes | 2900 bytes | 1 bytes | 1244 bytes | 1992 bytes |
| Ed25519 | 1023 bytes | Verification | SuperFast | OptLow | 15 488 bytes | 1748 bytes | 1 bytes | 1244 bytes | 1152 bytes |
| Ed25519 | 1023 bytes | Verification | SuperFast | OptHigh | 15 894 bytes | 2900 bytes | 1 bytes | 1244 bytes | 1992 bytes |
2.5. RSA signature & verification
In this section we provide the performance results for RSA signature & verification.
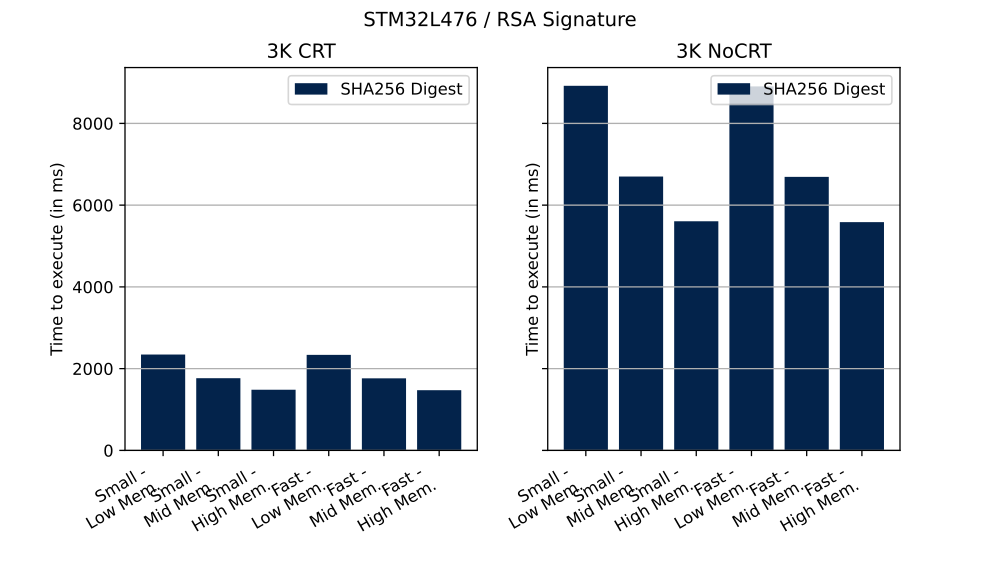
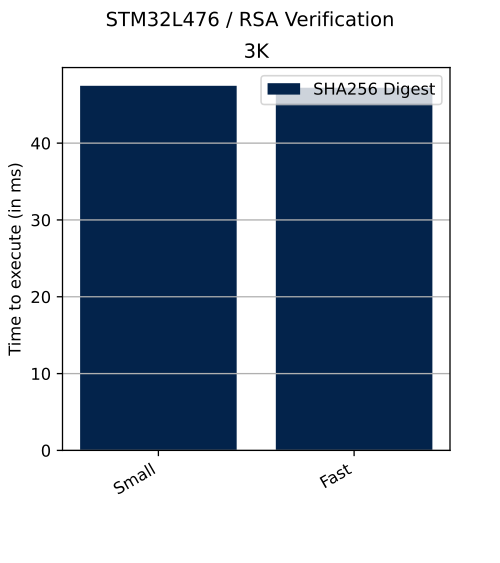
The table below shows the number of clock cycles and time (in ms) needed to perform described operation in different configurations.
| PKCS#1 | Priv. key mod. exp. method | Hash method | Modulus size | Operation | RSA mathematics configuration | Priv. key mod. exp. implementation | Cycles | Time |
|---|---|---|---|---|---|---|---|---|
| v2.2 | CRT | SHA-256 | 3K | Signature | Small | Low | 187 670 752 | 2345 ms |
| v2.2 | CRT | SHA-256 | 3K | Signature | Small | Mid | 141 306 808 | 1766 ms |
| v2.2 | CRT | SHA-256 | 3K | Signature | Small | High | 118 682 200 | 1483 ms |
| v2.2 | CRT | SHA-256 | 3K | Signature | Fast | Low | 186 957 488 | 2336 ms |
| v2.2 | CRT | SHA-256 | 3K | Signature | Fast | Mid | 141 014 392 | 1762 ms |
| v2.2 | CRT | SHA-256 | 3K | Signature | Fast | High | 117 869 760 | 1473 ms |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Small | Low | 713 570 976 | 8919 ms |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Small | Mid | 536 007 032 | 6700 ms |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Small | High | 448 383 432 | 5604 ms |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Fast | Low | 712 342 056 | 8904 ms |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Fast | Mid | 535 327 672 | 6691 ms |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Fast | High | 446 742 296 | 5584 ms |
| v2.2 | n/a | SHA-256 | 3K | Verification | Small | n/a | 3 797 048 | 47 ms |
| v2.2 | n/a | SHA-256 | 3K | Verification | Fast | n/a | 3 776 552 | 47 ms |
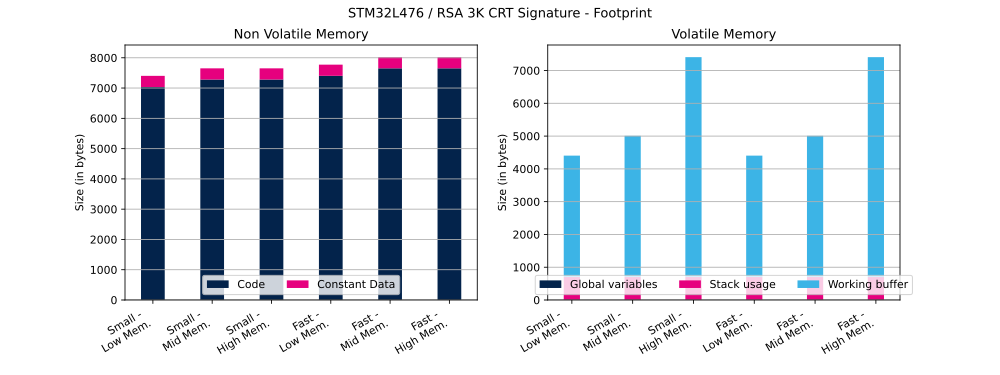
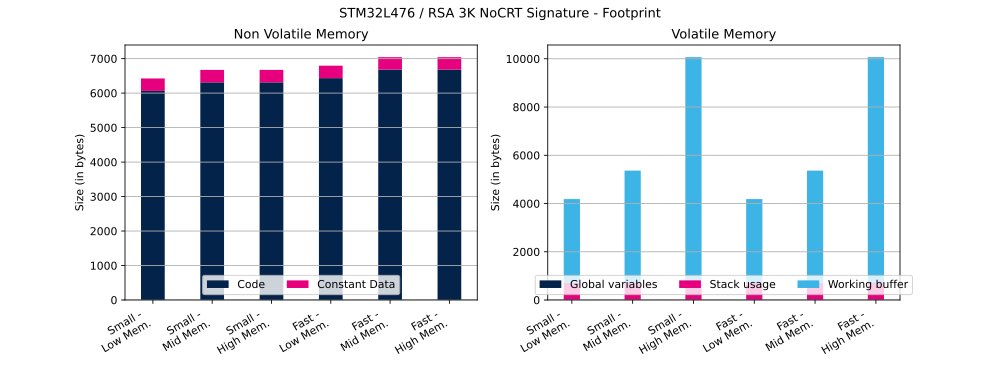
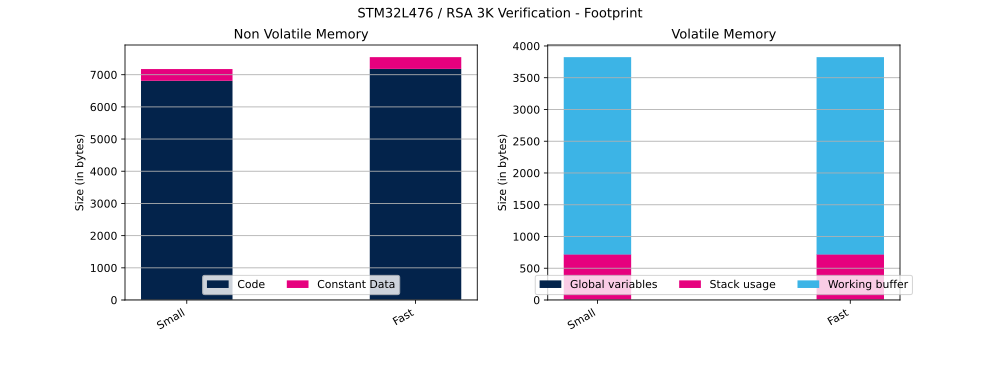
The table below shows RSA Flash and RAM usage (in bytes).
| PKCS#1 | Priv. key mod. exp. method | Hash method | Modulus size | Operation | RSA mathematics configuration | Priv. key mod. exp. implementation | Code | Constant data | Global data | Stack usage | Working buffer |
|---|---|---|---|---|---|---|---|---|---|---|---|
| v2.2 | CRT | SHA-256 | 3K | Signature | Small | Low | 7034 bytes | 369 bytes | 5 bytes | 700 bytes | 3704 bytes |
| v2.2 | CRT | SHA-256 | 3K | Signature | Small | Mid | 7282 bytes | 369 bytes | 5 bytes | 700 bytes | 4308 bytes |
| v2.2 | CRT | SHA-256 | 3K | Signature | Small | High | 7282 bytes | 369 bytes | 5 bytes | 700 bytes | 6708 bytes |
| v2.2 | CRT | SHA-256 | 3K | Signature | Fast | Low | 7404 bytes | 369 bytes | 5 bytes | 700 bytes | 3704 bytes |
| v2.2 | CRT | SHA-256 | 3K | Signature | Fast | Mid | 7652 bytes | 369 bytes | 5 bytes | 700 bytes | 4308 bytes |
| v2.2 | CRT | SHA-256 | 3K | Signature | Fast | High | 7652 bytes | 369 bytes | 5 bytes | 700 bytes | 6708 bytes |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Small | Low | 6064 bytes | 361 bytes | 5 bytes | 700 bytes | 3484 bytes |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Small | Mid | 6312 bytes | 361 bytes | 5 bytes | 700 bytes | 4664 bytes |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Small | High | 6312 bytes | 361 bytes | 5 bytes | 700 bytes | 9368 bytes |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Fast | Low | 6434 bytes | 361 bytes | 5 bytes | 700 bytes | 3484 bytes |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Fast | Mid | 6682 bytes | 361 bytes | 5 bytes | 700 bytes | 4664 bytes |
| v2.2 | No CRT | SHA-256 | 3K | Signature | Fast | High | 6682 bytes | 361 bytes | 5 bytes | 700 bytes | 9368 bytes |
| v2.2 | n/a | SHA-256 | 3K | Verification | Small | n/a | 6810 bytes | 365 bytes | 5 bytes | 716 bytes | 3108 bytes |
| v2.2 | n/a | SHA-256 | 3K | Verification | Fast | n/a | 7180 bytes | 365 bytes | 5 bytes | 716 bytes | 3108 bytes |