This article contains an overview of the security features[1] available on STM32U0 MCUs. The table below contains detailed information based on the different product lines.
| Security features embedded on: | |||
|---|---|---|---|
| Secure Boot and Firmware Update | |||
| OEMiSB | |||
| OEMiRoT | |||
| Application isolation | |||
| HDP | |||
| Cryptography | |||
| ST crypto lib | |||
| Crypto libraries | |||
| Silicon device life cycle | |||
| RDP with regression | |||
| Product state | |||
| Debug authentication | |||
- Possible, but needs more development effort by customer, because it's not supported by an example.
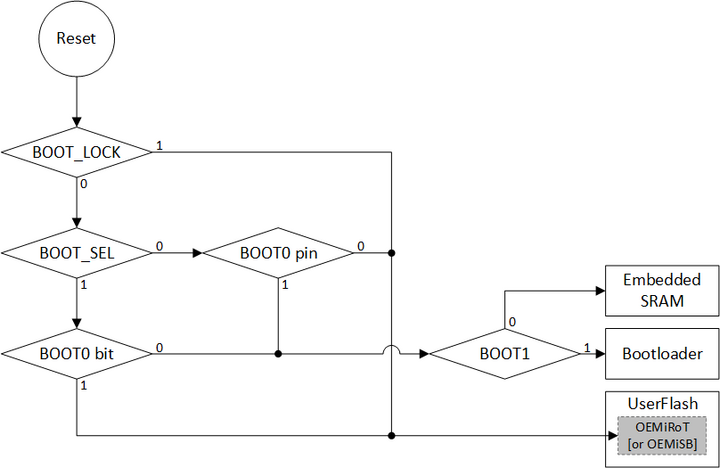
1. Secure Boot and Firmware Update
When a product's code needs securing, it becomes necessary to embed a Root of Trust (RoT).
This RoT ensures the next stage of security ensuring the code integrity and its authenticity.
By definition, a RoT must be based on an immutable code handling the reset of the platform.
The RoT is the foundation to build a secure product.
On STM32U0, the implementation of the root of trust is based on boot lock and HDP features allowing to design robust secure boot solutions.
Two solutions are proposed:
- OEMiSB
- OEMiRoT
1.1. OEMiSB
OEMiSB stands for OEM immutable (unchangeable) Secure Boot. OEMiSB offers only one service:
- The Secure Boot (root of trust service) is an immutable code, which is always executed after a system reset. It checks static protections (options bytes), activates runtime protections, and then verifies the integrity of the user application code before every execution.
1.2. OEMiRoT
OEMiRoT stands for OEM immutable (unchangeable) Root of Trust and acts as a first boot stage. It is based on the MCUboot open-source software[2] provided with STM32CubeU0.
OEMiRoT offers two services:
- The Secure Boot (root of trust service) is an immutable code, which is always executed after a system reset. It checks static protections (option bytes), activates runtime protections, and verifies the authenticity and integrity of the user application code before every execution.
- The Secure Firmware Update application is an immutable code that detects new firmware image candidates. It checks the version (version downgrade prevention), authenticity, and integrity before installing it after decryption.
2. Application isolation
2.1. Securable memory area by Hide Data Protect (HDP)
The main purpose of the securable memory area is to protect a specific part of the flash memory against undesired access. Following a system reset, the code in the securable memory area is executable only until this area is hidden. It remains inaccessible until a system reset occurs. This allows implementing software security services with root parameters including secret parameters owned only by the secure boot.
2.2. Securable memory area extension
The HDP area can be extended though a dedicated volatile register indicating the number of supplementary pages added to the securable memory area.
3. Cryptography
Means of performing cryptography depends on the STM32U0 product line.
| Cryptography features embedded on: | |||
|---|---|---|---|
| Hardware Tiny AES | NO | NO | YES |
| Hardware HASH | NO | NO | NO |
| Hardware SAES | NO | NO | NO |
| Hardware PKA | NO | NO | NO |
| ST crypto lib | YES | YES | YES |
| Crypto libraries | YES | YES | YES |
STM32Cube HAL can be used to work with the crypto IP.
3.1. ST crypto lib
ST crypto library v4[3] is available for the STM32U0 MCUs.
ST crypto library is delivered through X-CUBE-CRYPTOLIB with many examples.
3.2. Crypto libraries
Third-party libraries such as Mbed™ are available for STM32U0 MCUs.
Mbed™ library implements PSA crypto API. Mbed™ is distributed as source code.
4. Silicon device life cycle
The flexible device life cycle scheme is based on the readout protection (RDP) mechanism, including support for product decommissioning (auto-erase):
- Opened, closed, or limited debug protection, depending on the RDP level.
- Optional password-based RDP level regressions, including for RDP Level 2.
5. References