1. Introduction
The STM32H5 series provide a security framework with a trusted execution environment: the Secure Manager. It simplifies the security development cycle of embedded applications, by providing ready-to-use security services that are developed following the recommended industry standards.
The OEM can choose to develop its application using the Secure Manager or not.
As 2 SFI procedures can be applied to the STM32H5 series, this choice has an impact on the SFI procedure to follow:
2. SFI for STM32H5 series with Secure Manager
This procedure must be followed when the OEM installs an application developed using the Secure Manager. In that case, there are several additional components to prepare, to test and to install.
The list of applicable products is detailed below:
| Type | Products |
|---|---|
| Microcontroller | STM32H573xx |
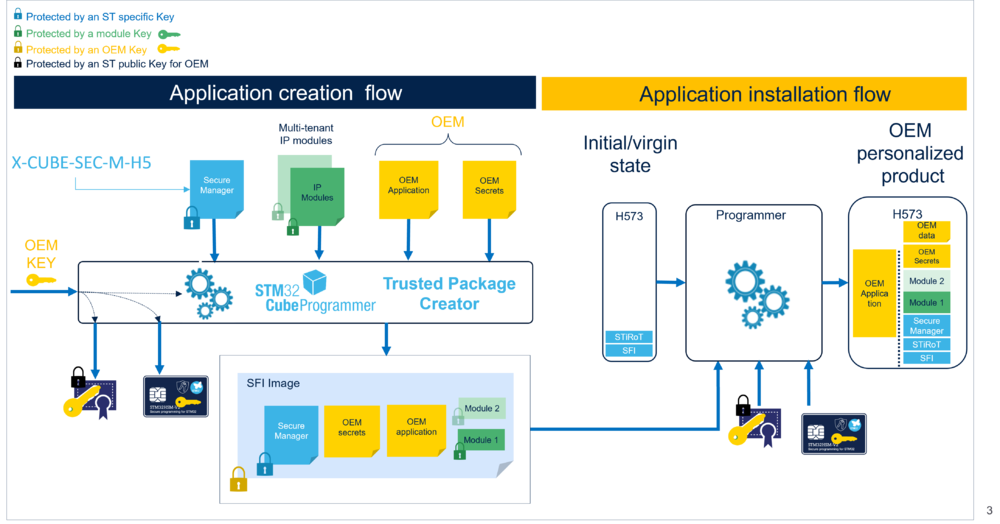
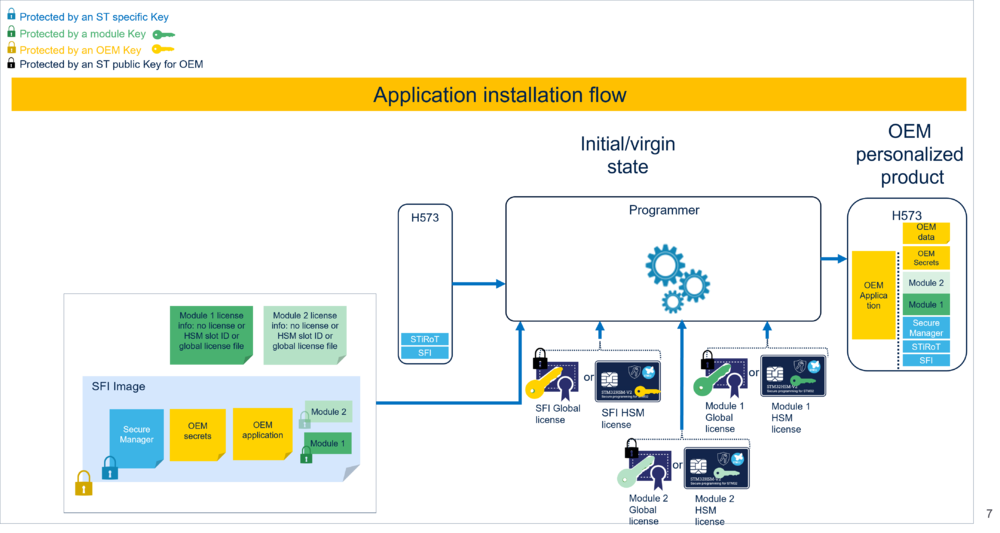
The preparation and installation flow is described in the image below:
STMicroelectronics provides the SFI solution to perform the preparation and installation flows.
2.1. Preparation flow
2.1.1. Overview
The purpose of this step is to:
- prepare the installation of the encrypted firmware image, which is called SFI image. It is composed of the OEM application and the additional components (OEM secrets, Secure Manager and modules).
- provision the OEM key within an HSM or within a global license.
2.1.2. SFI image
2.1.2.1. Overview
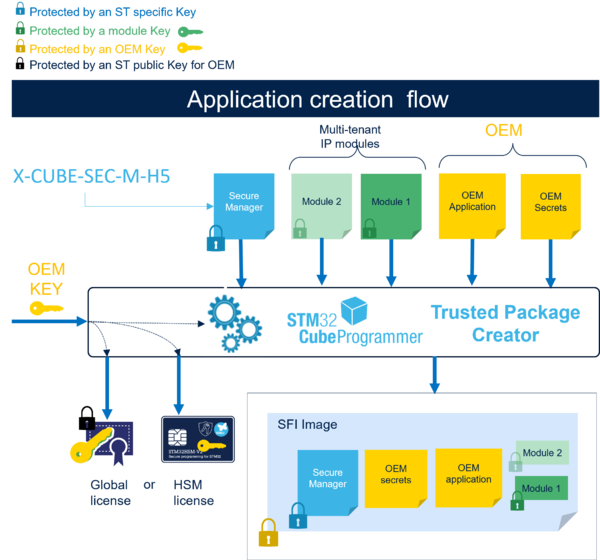
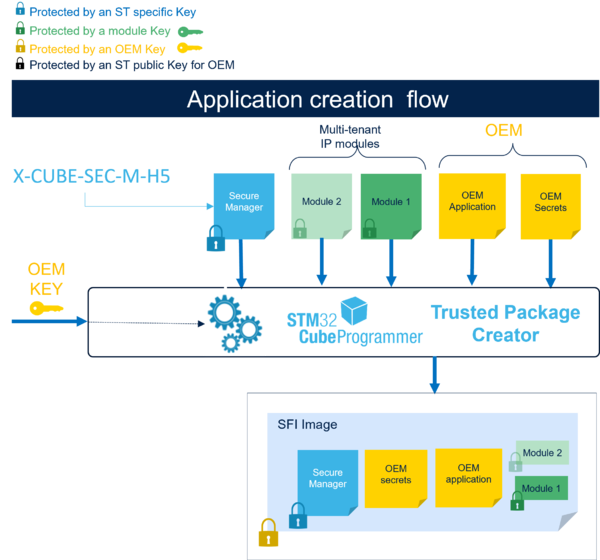
The image below contains an overview of the SFI image creation flow.
2.1.2.2. SFI image generation
Once the OEM application has been developed using the SMAK, the OEM must prepare and test the SFI image to install during manufacturing.
For that purpose, the OEM must use the SMAK in the production preparation phase. This allows to correctly generate the SFI image (for instance, setting the Secure Manager configuration according to the OEM application) and to test it before manufacturing.
The output of the SMAK production preparation phase is the tested SFI image, ready to be installed during manufacturing.
2.1.2.3. Description of the SFI image inputs
The OEM must provide the following inputs:
- The OEM application: The OEM must provide its application binary, developed using the Secure Manager.
- The Secure Manager: The Secure Manager binary is available as an encrypted image from STM32TRUSTEE-SM[1].
- The modules: The Secure Manager offers the possibility to install secure modules. However, the Secure Manager requires these modules to have an specific format. Only SMDK provides this format for modules. The modules must be developed via the SMDK.
- The OEM secrets: The OEM secrets are the OEM data, the OEM keys and also the Secure Manager OEM configuration.The OEM secrets are described in detail in the Secure Manager configuration.
During the SFI procedure, the OEM must set its secrets, paying specific attention to the following elements:
- Factory Internal Trusted Storage (ITS): The OEM can change the factory ITS blob default content to include its own keys and data.
- Secure Manager keys: The OEM must update the default Secure Manager keys and use their own keys.
- Secure Modules configuration: The OEM must set the license type for each module (no license, global license or chip specific license).
The OEM must set the licensed modules installation model. The same model is used for all the licensed modules. The OEM must set the secure SRAM size used by the modules (one secure SRAM area is shared between all the modules).
- Option Bytes: The OEM must set carefully the Product state.
2.1.2.4. SFI image output description
The Trusted Package Creator encrypts the SFI image inputs with the OEM key, and generates the SFI image.
The SFI image is then an encrypted image containing the Secure Manager, the OEM application, the OEM secrets, and the modules.
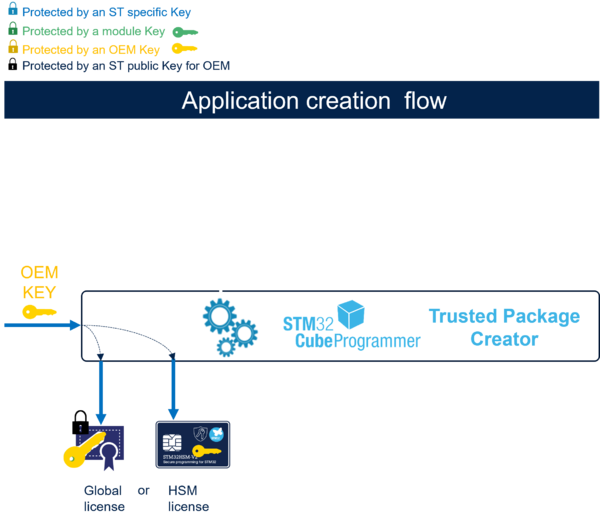
2.1.3. OEM key provisioning
The OEM must provide its OEM key to the Contract Manufacturer (CM) in a way the OEM key cannot be read or extracted clearly by the CM. Only the STMicroelectronics STM32 microcontrollers can handle the OEM key.
In SFI for STM32H5 with Secure Manager, there are 2 ways to provide the OEM key to the CM:
- The OEM provisions its OEM key, using the Trusted Package Creator, in one HSM.
- The OEM provisions its OEM key, using the Trusted Package Creator, in one global license file.
Then:
- Only the STMicroelectronics STM32 microcontrollers can securely install the SFI image.
- Authenticity, integrity, and confidentiality of the SFI image content is ensured.
When using the HSM, the number of STM32 chips to program can be counted.
2.2. Installation flow
Compared to other platforms, there is one additional input, which is the module license information file.
This file indicates if the module to install is licensed or not.
If the module is licensed, the file can provide the module global license file path, or can indicate the HSM slot ID. The HSM card is provisioned with the module secret key and initialized with a max counter of licenses, in case of module chip specific license.
The installation procedure is similar to the generic SFI installation procedure, deployed on other STM32 products supporting SFI.
2.3. Step by Step SFI procedure
Follow How to start SFI on STM32H5 with Secure Manager to run the SFI procedure on STM32H5 with Secure Manager.
3. SFI for STM32H5 without Secure Manager
This procedure must be followed when the OEM installs an application developed without the use of the Secure Manager.
The table below indicates the list of applicable products:
| Type | Products |
|---|---|
| Microcontroller | STM32H573xx, STM32H563xx, STM32H533xx, STM32H523xx |
In this case, the SFI procedure on the STM32H5 series is similar to the SFI procedure applied on other platforms.
Follow SFI Step-by-step on STM32 boards to run the SFI procedure on the STM32H5 without Secure Manager.
4. References