TF-M Overview
1. What is TF-M ?
TF-M (Trusted Firmware for Cortex-M) is an open-source reference implementation of runtime trusted execution environment operating system that follows the Arm(R) Platform Security Architecture (PSA) for Cortex-M. TF-M is hosted under www.trustedfirmware.org.
It supports ArmV8-M and ArmV8.1-M architectures.
For the STM32 series, it targets products implementing TrustZone (STM32L5, STM32U5, STM32WBA).
TF-M supports the following security functions:
- Secure boot
- Secure firmware update
- Isolation
- Internal trusted storage
- Protected storage
- Cryptography
- Attestation
In addition, TF-M supports 3 isolation levels and trusted applications (TA) that can be developed and integrated to support various types of applications requiring a strong physical and logical isolation.
The main advantages of TF-M are:
- Arm(R) PSA standard and API compliancy
- Availability on most STM32 series supporting TrustZone
- Multiple configurations (for example, crypto algorithm selection)
- Core security services
- Multiple isolation strategies
- Secure boot, Secure firmware update capability
- Trusted apps support
2. TF-M
TF-M applications are part of the STM32Cube package.
They are certified for ARM PSA Level 1, Level 2, and Level 3.
The open-source TF-M revisions are available at the following armDeveloper: Git Repository
For more information about ST PSA certified products refer to:
STM32MCU PSA certification
For more information about PSA security certification refer to:
ARM PSA for IOT
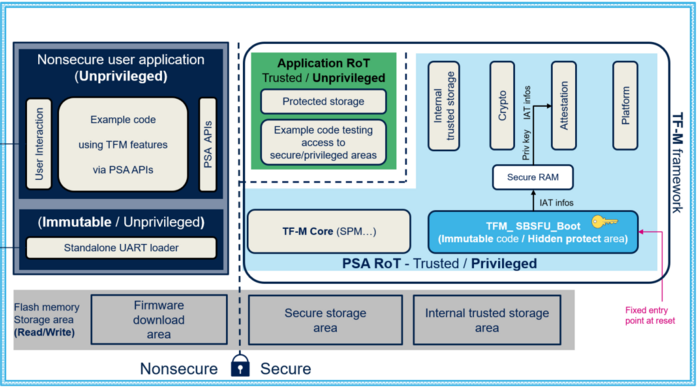
This figure shows the TF-M implementation overview that is explained in the following sections.
2.1. Secure boot (SB)
The first TF-M feature is the secure boot, an immutable (not possible to modify) embedded application executed after a system reset.
This application is based on the MCUboot open-source software MCUboot.
The secure boot ensures that no unauthorized or modified (for instance, malware) software is executed.
- It checks the MCU static protections and activates the runtime protections.
- Note: The secure boot code is immutable if the hardware protection mechanisms of the device are correctly activated (responsibility of the customer).
Embedded cryptography is used to ensure:
- Integrity: verification that the image that is going to be executed has not been altered.
- Authenticity: verification that the image that is going to be executed is coming from a trusted and known source. It prevents unauthorized software from being installed and executed.
Note: Also applicable to data image.
2.2. Secure firmware update (SFU)
The second TF-M feature is the secure firmware update, an immutable (not possible to modify) embedded application to download a new firmware image to a device in a secure way.
The new firmware can be installed to an internal or external flash.
The integrity and authenticity of this new firmware is verified before installing and executing it.
Two modes are supported:
- Single slot: the current firmware is replaced with the new downloaded firmware (rollback is not possible).
- Dual slot: the current firmware is kept, and the new downloaded firmware is installed additionally, implicitly requiring more flash memory space, but advised for over-the-air firmware updates and ensures a safer firmware update (possible rollback).
Two firmware download modes are possible:
- Download of a single binary image including both the secure and nonsecure part of the new firmware
- Download of two different binary images, one for the secure and one for the nonsecure part of the new firmware
- Note: The secure firmware update code is immutable if the hardware protection mechanisms of the device are correctly activated (responsibility of the customer).
The secure firmware update executes the following steps:
- 1) The new created firmware image is encrypted and stored in the server.
- 2) The new encrypted firmware image is sent to the device through a communication channel for instance, over-the-air.
- 3) The new firmware is checked, decrypted, and installed.
Embedded cryptography ensures:- Confidentiality: only devices having access to the encryption key can decrypt the new firmware image.
- Integrity: ensures that the downloaded firmware image has not been modified maliciously or corrupted.
- Authenticity: ensures that only authorized entities can install and execute code.
Note: Also applicable to data image.
2.3. Secure services at run time
The TF-M package provides a set of services that manage critical assets isolated from nonsecure applications.
These services can be called during execution of a nonsecure application.
However, only the called service can access the critical assets (for instance, an encryption key). The nonsecure application can only call the secure services.
These secure services are compliant to PSA recommendations to achieve PSA certification.
- PSA (Platform Security Architecture) is an architecture-agnostic framework proposed by ARM and their partners. A product can be certified to ensure a specific security level (level 1 to level 3), refer to https://developer.arm.com/architectures/architecture-security-features/platform-security.
The secure services address the following topics:
- Confidentiality: protection against unauthorized accesses through hardware/software exploitation.
- Access authentication: mechanism to ensure the requester’s identity (a nonsecure entity, secure entity, or a remote server).
- Integrity: prevents unauthorized content modification or corruption.
- Reliability: protection against power failure scenarios and incomplete write cycles.
- Configurability: high level configurability to scale up/down memory footprint to cater for a variety of devices with varying security requirements.
2.3.1. Protected storage (PS)
The TF-M protected storage (PS) service implements the PSA protected storage APIs.
The PS supports data encryption and writing encrypted data in a possible untrusted storage.
The provided reference code uses AES-GCM based AEAD encryption to ensure data confidentiality, integrity, and authenticity.
The PS ensures data protection against tampering by either the normal users of a product, package, or system or others with physical access to it. If the content of the protected storage is changed maliciously, the service is able to detect it.
2.3.2. Internal storage services (ITS)
The TF-M internal trusted storage (ITS) service implements PSA internal trusted storage APIs.
The ITS supports writing of data in the device built-in flash memory region.
The access to this flash region is protected through hardware isolation and hardware security protection mechanisms.
This guarantees the data confidentiality and prevents unauthorized (nonsecure or unprivileged secure) flash domain accesses without requiring a data encryption.
The ITS ensures data protection against tampering by individuals with physical access through the internal flash device itself, while resistance to tampering by nonsecure or application updatable Root of Trust (RoT) entities is provided by a hardware isolation mechanism.
2.3.3. Secure cryptographic service
The TF-M cryptographic service is a reference implementation of the PSA crypto API.
This service is based on open-source software supports, symmetric and asymmetric ciphers, hash, message authentication codes (MACs), authenticated encryption with associated data (AEAD), randomization, and key derivation. This secure service can be used by other services running in the secure processing or by applications executed in nonsecure mode.
2.3.4. Initial attestation service (IAT)
The TF-M initial attestation service proves the device identity through an entity attestation token (EAT).
The EAT is a fixed set of device specific data provided on demand by this secure service.
The device embeds an attestation key pair (private and public) programmed during manufacturing and unique for each device.
The token is signed with these two keys. The token authenticity is verified using the public key.
2.4. TF-M application architecture
The following section describes the TF-M applications.
2.4.1. TF-M applications
2.4.1.1. TFM _SBSFU_Boot
This application manages the TF-M secure boot and secure firmware update services.
It also manages the first level of security protections on the platform required during TFM_SBSFU_Boot application execution.
It is an immutable code (not possible to modify) and executed after a device reset.
The core function of this application uses the MCUboot middleware, the trusted firmware (TFM) middleware, and the Mbed-crypto library middleware (see TF-M Middleware section).
2.4.1.2. TFM_Appli secure
This application manages the secure run time services offered to a nonsecure application.
It can be called by the nonsecure application at run time by the PSA API.
It also finalizes the security protections required during the application execution.
2.4.1.3. TFM_Appli nonsecure
This application is a code example of a nonsecure user application, demonstrating how to use TF-M secure services available in the TFM_Appli secure application.
The user can modify this code to include their own user application.
2.4.1.4. TFM_Loader secure
This application manages the secure flash memory access offered to TFM_Loader nonsecure application.
2.4.1.5. TFM_Loader nonsecure
This application is a code example of standalone local loader using Ymodem protocol. It allows downloading a new version of the secure firmware image (TFM_Appli secure application) and a new version of the nonsecure firmware image (TFM_Appli nonsecure application).
2.4.2. TF-M middleware
2.4.2.1. MCUboot
MCUboot is a secure bootloader for easy software upgrade.
It is an open source code.
This application manages the TF-M secure boot and secure firmware update services. It also manages the first
level of security protections on the platform required during TFM_SBSFU_Boot application execution.
2.4.2.2. Trusted firmware middleware
TF-M trusted firmware includes the services at run-time.
The core services at runtime are: inter-process communication (IPC), secure partition manager (SPM), and interrupt handling.
The secure services at runtime are: initial attestation, cryptography (relying on the Mbed-crypto middleware for the cryptographic part), protected storage, and internal trusted storage.
These services are open source code.
2.4.2.3. Mbed-crypto library
The Mbed-crypto library is a C library supporting symmetric and asymmetric cryptography as well as hash computation.
It is an open source code and includes a reference implementation of the PSA cryptography API.
This library is used by MCUboot middleware during the "secure boot" operation or during "secure firmware update" operation, and by TF-M middleware to implement cryptographic services.
2.4.3. TF-M drivers
2.4.3.1. Board support package (BSP)
The BSP is a set of APIs related to the configurations needed to support specific hardware boards (e.g. LCD, external memory interfaces, audio, MEMs drivers).
2.4.3.2. Hardware abstraction layer (HAL)
The HAL drivers are an abstraction layer simplifying the user code development for MCU and peripherals configurations.
2.4.3.3. Low layer (LL)
The LL drivers are a set of APIs for direct configurations and usage of embedded features.
LL is a fast, light-weight layer but requires a more in-depth know-how of the IPs embedded in the MCU.
Since the LL drivers are more specific to a given MCU architecture, it is less portable to another MCU than the HAL.
2.4.4. TF-M third party secure function
These application updatable services can access any assets in the system except the assets stored in the privileged area.
These secure services are executed in unprivileged mode and located in the secure environment.
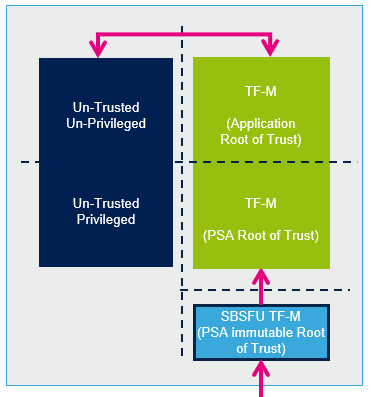
2.5. Resource isolation
The ARM TF-M architecture is defined with two levels of isolation.
- A first isolation between the secure processing environment (trusted) and the nonsecure processing environment (untrusted), guaranteed by ARM TrustZone.
- A second isolation level for both trusted and untrusted environment is defined through privileged and unprivileged attributes
3. Documentation and resources
TF-M documentation and resources can be found on STM32Trust page[1].
The following documents are available on this page:
- UM2671: Getting started with STM32CubeL5 TF-M applications
- UM2851: Getting started with STM32CubeU5 TF-M applications
- UM3128: Getting started with STM32CubeWBA TF-M applications
Further available references:
The following URLs belong to third parties. It is active at document publication. However, STMicroelectronics shall not be liable for any change, move, or inactivation of the URL or the referenced material.
- Open-source software resource reference: TF‑M (Trusted firmware-M) Arm Limited driven open-source software framework page[2]
- Open-source software resource: MCUboot page[3]
- Open-source software resource: mbed-crypto page[4]
- PSA certification website[5]
4. References
Short introdution to Trusted Firmware