STiRoT stands for ST Immutable (unchangeable) Root of Trust. This is a ROM code developed by STMicroelectronics, which targets a SESIP level 3 certified implementation. Since STiRoT requires hardware cryptographic features, it is only available on STM32H7Sxx product lines.
One of the major specificities of this series is that STM32H7xx integrates only 64 Kbytes of user flash. As a consequence, the user application is stored most of the time in the external memory selected by the OEM.
A detailed description of STiRoT is provided in AN6045
List of applicable products:
| Type | Products |
|---|---|
| Microcontroller | STM32H7S7A8, STM32H7S7I8, STM32H7S7L8, STM32H7S7N8 STM32H7S7Z8, STM32H7S3A8, STM32H7S3I8, STM32H7S3L8, STM32H7S3L8U, STM32H7S3N8, STM32H7S3R8, STM32H7S3V8, STM32H7S3Z8 |
1. STiRoT services
STiRoT provides two services:
- The Secure Boot (root of trust services) is an immutable code, which is always executed after a system reset. It activates runtime protections and then it verifies the authenticity and integrity of the application code before every execution.
- The Secure Firmware Update application is an immutable code that detects that a new firmware image is available. It checks its authenticity, then checks the integrity of the code before installing it after decryption.
2. STiRoT activation
STiRoT is activated in two different use cases:
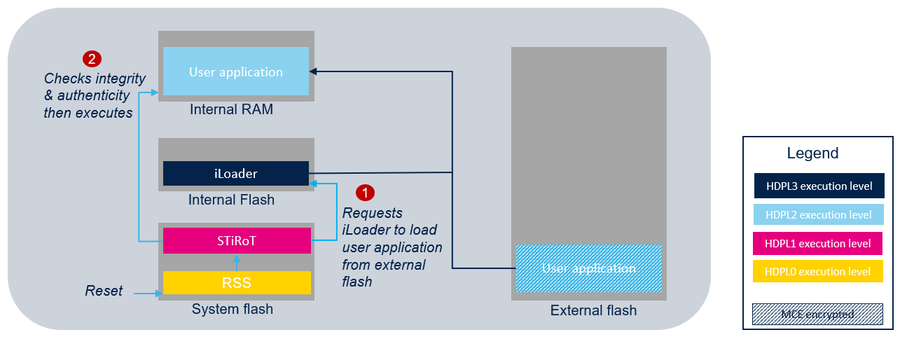
- One boot stage: STiRoT directly manages the user application. At reset, STiRoT first requests iLoader to load the user application from external flash to internal RAM. Then after a successful verification of the authenticity and the integrity of the user application, STiRoT executes it.
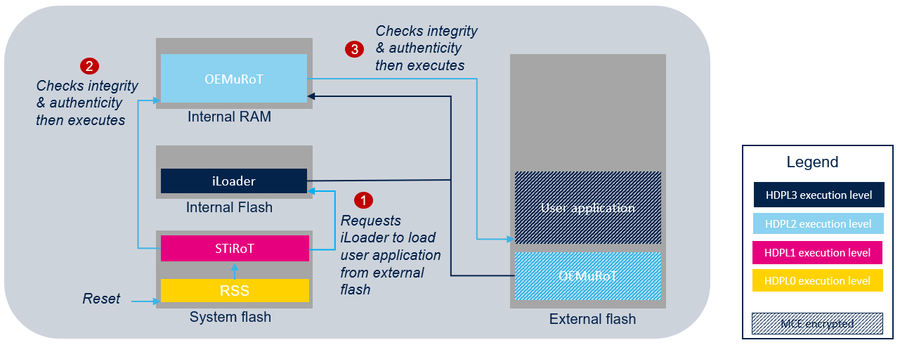
- Two boot stages: STiRoT manages an updatable boot stage (OEMuRoT) which manages the user application. The updatable boot stage can be customized to fit the customer needs.
In both cases, STiRoT never accesses the external flash memory. The control of the authenticity and the integrity as well as the execution of the user application or the OEMuRoT is always done in the internal RAM memory. To do this, STiRoT relies on the iLoader application to copy the user application or the OEMuRoT from the external flash memory to the internal RAM memory.
Refer to AN6045 to get all the details on the STiRoT activation use cases.
An example of one boot stage configuration is provided through How to start with STiRoT on STM32H7S article.
An example of two boot stages configuration is provided through How to start with STiRoT-OEMuRoT on STM32H7S article.
3. STiRoT configuration
The STiRoT configuration provides the possibility to:
- Define the RAM and the external flash memory mapping by selecting the location and the size of each area (download area, installation area, execution area).
- Configure the authentication and encryption keys.
- Allow the jump in the bootloader (external access) when no valid image is installed.
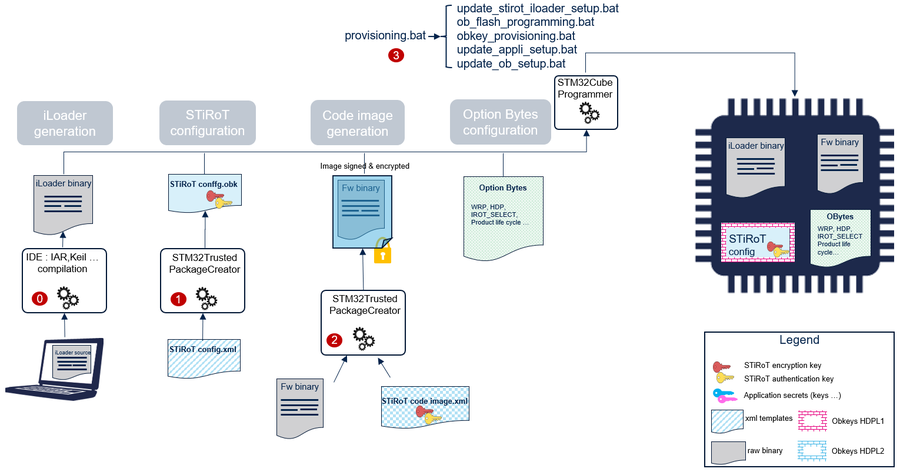
The product provisioning to activate and configure STiRoT is done following the four steps below when executing provisionning.bat:
- 0- Generation of iLoader binary.
- 1- Configuration of STiRoT. At this stage, the locations of the image, and the cryptographic keys are defined.
- 2- Generation of the code image (user application or OEMuRoT).
- 3- Programming of the OBKeys, the option bytes, the iLoader, and the image in the device.
Note: A set of scripts is provided in the STM32CubeH7RS MCU package (Firmware/Projects/STM32H7S78-DK/ROT_Provisioning/STiROT folder). It guides the user all along the provisioning process.
Refer to AN6045 to get all the details on the STiRoT provisioning process including the OBkeys configuration files and the code image generation.