This article gives an overview of the OEMiSB solution integrated in STM32U0.
How to use it, step by step, is described in wiki pages Getting started with STM32U0 security.
List of applicable products:
| Type | Products |
|---|---|
| Microcontroller | STM32U083xx, STM32U073xx, STM32U031xx |
1. OEMiSB presentation
1.1. Overview
OEMiSB stands for OEM immutable (unchangeable) Secure Boot. OEMiSB offers only one service:
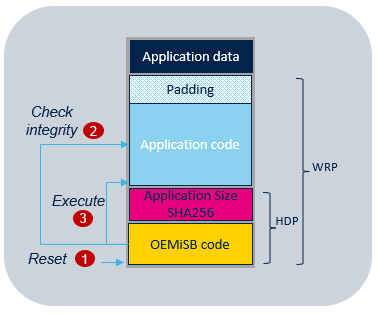
- The Secure Boot (root of trust service) is an immutable code, which is always executed after a system reset. It checks static protections (Options Bytes), activates runtime protections and then verifies the integrity of the user application code before every execution.
1.2. Protection measures and security strategy
A set of measures and system-level strategies are needed for protecting critical operations and sensitive data (such as the SHA256 of the application), and the execution flow, in order to improve security robustness. On STM32U0, the security strategy is based on:
- RDP: Read protection level 2 achieves the highest protection level. Read protection level 2 with OEM2 password capability is used to ensure that a JTAG debugger cannot access the device, except to inject the OEM2 password. In RDP level 2, when the OEM2 password is injected on the JTAG port, the RDP level is regressed to level 1. The OEM2 password must first have been provisioned when the RDP level is 0. Refer to RDP for U0 wiki article for more details.
- Boot lock: BOOT_LOCK option byte is set to establish a chain of trust, by forcing the system to boot from the user flash memory in 0x08000000.
- MPU: The MPU is a memory protection mechanism that allows specific access rights to be defined for any memory-mapped resources of the device: flash memory, SRAM, and peripheral registers. The MPU is configured to limit the execution surface to the code section of OEMiSB_Boot project during its execution then extended to the application code region after verifying its integrity. This protection is dynamically managed at runtime.
- HDP: when the HDP secure hide protection is activated, any accesses to the protected flash memory area (fetch, read, programming, erase) are rejected. All the code and secrets located inside the protected flash memory area are fully hidden. In the OEMiSB example, the system is configured to hide the OEMiSB_Boot code, and OEMiSB data (SHA256) area located in flash memory (Refer to the Flash memory layout for more details on HDP area) just before launching the verified user application.
- WRP: write protection is used to ensure code and data immutability as requested by the state-of-the-art standards in secure boot implementation. In the OEMiSB example, the system is configured to make the OEMiSB_Boot code, OEMiSB data (SHA256) and application code as immutable.
See also STM32U0 Reference manual for more description on each feature.
Secure software coding techniques such as doubling critical tests, doubling critical actions, random delay, checking parameter values, and flow control mechanism, are implemented to improve security robustness.
A SHA256 control is implemented to verify the integrity of the user application. This cryptography operation is done in software (no hardware acceleration).
1.3. OEMiSB activation
On STM32U0, OEMiSB activation is done by:
- Configuring the BOOT_LOCK to 1
- Configuring the SHA256 and the size of the user application
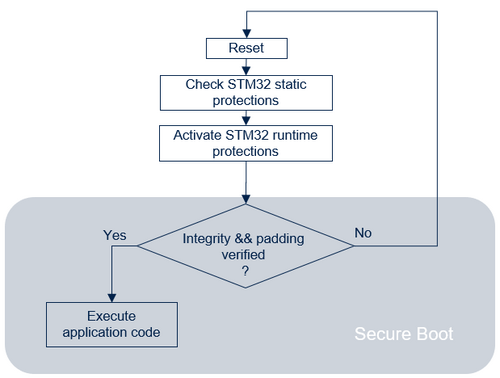
The following figure illustrates the secure boot process by showing all the steps required to boot the user application:
- At reset, boot is forced on OEMiSB when BOOT_LOCK is set to 1.
- OEMiSB calculates the SHA256 on the application code using the application size parameter.
- If the result matches the SHA256 stored as reference and if the padding area is fulfilled with 0xFFFFFFFF, OEMiSB jumps into the application code. The jump to the application code is done using a service from bootloader located in the system flash memory. This service activates the HDP (see also Bootloader documentation) then update the MPU configuration to allow the execution of the application code.
Note: For security robustness, when OEMiSB jumps into the user application, the MPU is configured to ensure that only the user application code area is allowed to be executed (execution surface controlled via MPU configuration). It is the user application responsibility to reconfigure the MPU to fit with its security needs.
2. Features list
The main features of the OEMiSB are:
- SHA256 cryptography for application code integrity check.
- Configurable data area : from 0 Kbytes to 16 Kbytes.
- Integration of the full entropy TRNG source (RNG hardware peripheral) for random delays generation.
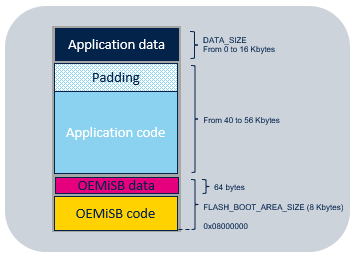
3. Flash memory layout
The STM32CubeU0 OEMiSB relies on flash memory layout defining several regions:
- Application data region: region where the read/write capabilty is enabled in the MPU configuration. This region is removed when the application data size is set to 0 during provisioning.
- Padding region: this region must be filled with 0xFFFFFFFF to ensure there is no malicious code.
- Application code region: region configured with execution capability in the MPU once the controls of the user application integrity and the padding value are done.
- OEMiSB_Boot data region: the SHA256 and the size of the application is stored in this 64 bytes region.
- OEMiSB_Boot code region: region to program the OEMiSB_Boot code binary that manages the function "Secure Boot".
Flash memory layout is as follow:
4. Provisioning process
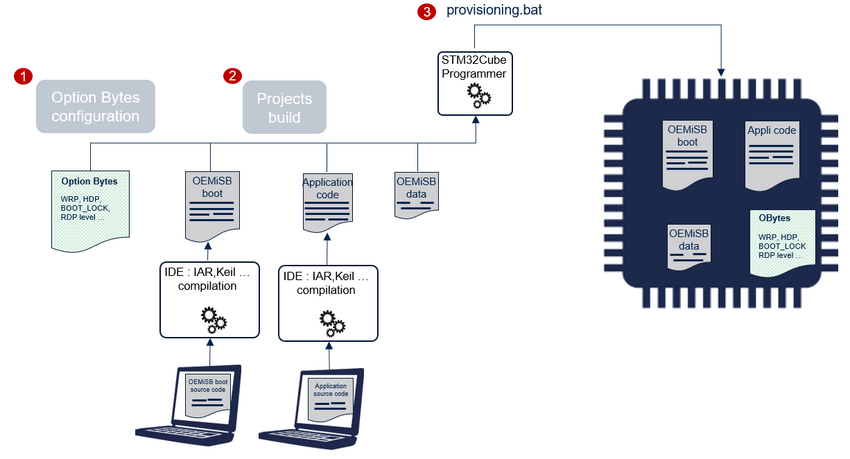
The product provisioning to activate and configure OEMiSB is done following the three steps below:
- Selecting the RDP level and the data area size.
- Generation of OEMiSB_Boot and application projects. The OEMiSB data containing the size and the SHA256 of the application is automatically generated during the provisioning.
- Programing of the option bytes, the OEMiSB_Boot binary and the OEMiSB data containing the reference SHA256 and the application size in the device.
Note: A set of scripts is provided in Firmware/Projects/NUCLEO-U031R8/ROT_Provisioning/OEMiSB folder. It guides the user all along the provisioning process. Refer to Getting started with STM32U0 security article.
5. Appendix
5.1. OEMiSB start-up sequence
Performance measured @ 48 MHz:
| 40 Kbytes | 56 Kbytes | |
|---|---|---|
| Application boot time | 122 ms | 172 ms |