1. Environment setup
As explained in SFI Image generation, the secure firmware install (SFI) image generation and the SFI image test rely on the secure manager access kit ( SMAK).
Follow SMAK prerequisites and SMAK package contents for the SFI environment setup.
2. Development at OEM: firmware creation
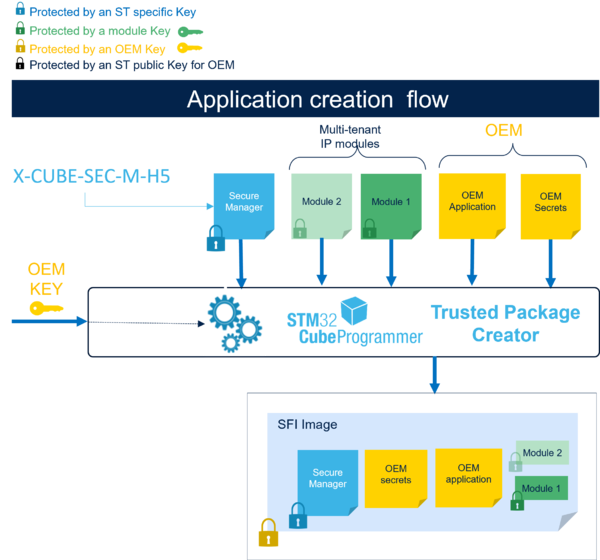
The purpose of this SFI service is to securely install the OEM firmware developed with secure manager.
Therefore, to use this SFI service, the OEM must develop its nonsecure application with the SMAK development phase.
The OEM firmware file is .hex extension.
ST provides an application example in \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\Applications\ROT\SMAK_Appli\Binary\appli_enc_sign.hex.
3. Secure room at OEM: SFI image generation and HSM provisioning
3.1. SFI image generation
Once the OEM completes its nonsecure application development, the OEM must prepare and test the final encrypted image (SFI image) used for OEM secure manufacturing with the SMAK production preparation phase.
3.1.1. step by step procedure
3.1.1.1. Step 0
- Replace the default applications with the OEM application (called oem_app.hex hereafter)
cp oem_app.hex \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Binary\appli_0.hex
cp oem_app.hex \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Binary\appli_1.hex
- module without license:
- copy module in \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Binary
cp module.hex \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Binary
- modify \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\provisioning.bat with
line 316:
add
set modules= --firmware "%projectdir%module.hex"
- modify \STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\provisioning.sh with
line 419:
add
modules=" --firmware $projectdir/SM/module.hex"
3.1.1.2. Step 1
Follow SMAK SFI image generation.
After this step, the SFI image is generated.
3.1.1.3. Step 2
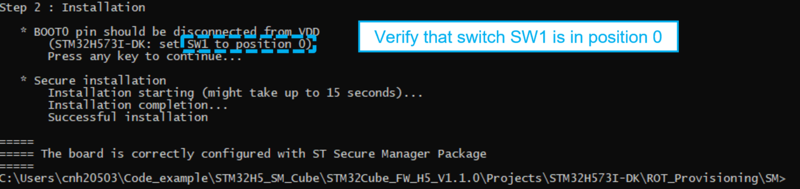
To test the generated SFI image, follow the indications of the script as shown in the figure below.
The step 2 of the script installs the secure manager, the OEM application application and the module (if any).
Once the installation is complete, the OEM application is running on target.
In case of issue:
- Check the provisioning.log file (in directory: STM32Cube_H5_V1.1.0\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM).
- Perform a regression (\STM32Cube_FW_H5\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\DA\regression.bat) and restart at the beginning of this article.
3.1.2. SMAK production preparation phase outputs
Once the previous steps have been completed, the OEM holds:
- the tested SFI image ready for manufacturing (called image.sfi hereafter)
- the SFI global license (called sfi_global_license.bin hereafter)
- the module information in case of module with license (it is needed for the secure firmware installation) (called module.mcsv hereafter)
3.2. HSM programming
inputs for HSM programming:
- OEM key (encryption AES key + nonce)
To program the HSM, you can follow the steps described in HSM programming using the STM32H573I-DK Discovery kit and its MB1677 main board.
After programming the HSM, it is now ready to be shipped to the contract manufacturer (CM) together with the SFI package created before.
4. Manufacturing at CM: secure firmware installation
In this step, the CM receives from the OEM:
- the SFI image to be installed (image.sfi)
- the SFI global license (sfi_global_license.bin) or in case of sfi chip specific license, the HSM card provisioned with the OEM key and initialized with a max counter of licenses
- in case of module with license:
- the module information (module.mcsv)
- the module global license file (module_global_license.bin) or in case of module chip specific license, the HSM card provisioned with the module secret key and initialized with a max counter of licenses
The SFI process could be performed through a regular JTAG/SWD interface or the system bootloader interface (you can refer to the application note AN2606[1] for details on the supported interface for each microcontroller).
The following covers the JTAG/SWD and system bootloader interface for each of the sections below:
- Hardware connection
- Software adaptation
- Target initial state
- Secure firmware install
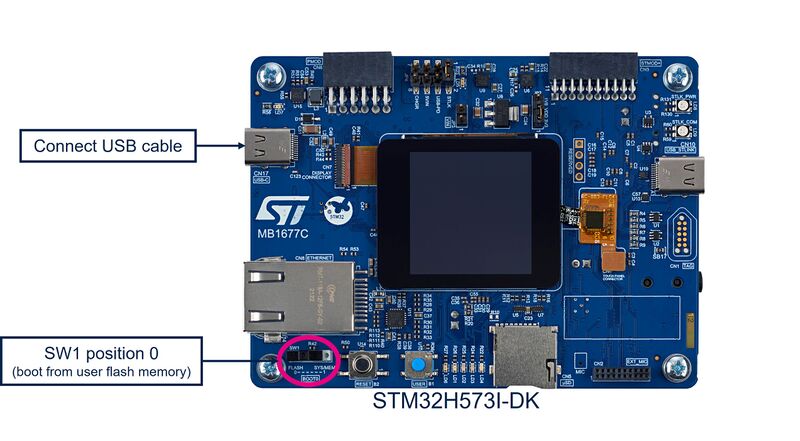
4.1. Hardware connection
4.1.1. Board
4.1.2. HSM card
Plug your HSM card provisioned with the SFI OEM key in case of SFI chip specific license.
Let us assume that the HSM card is plugged in the smart card reader slot 0.
Plug your HSM card provisioned with the module secret key in case of module chip specific license.
Let us assume that the HSM card is plugged in the smart card reader slot 1.
4.2. Software adaptation
Modify module.mcsv with the smart card reader slot index of the HSM card provisioned with the module secret key in case of module chip specific license (slot=1 in our example) or the path of the module global license.
4.3. Target initial state
The target must be in Open product state.
If it is not the case, a debug authentication (DA) full regression must be performed.
After this step, the device is ready for the SFI process.
4.4. Secure firmware install
This command starts the SFI process with:
- sfi chip specific license
- module with license
and proceeds with the installation:
STM32_Programmer_CLI.exe -log .\sfi.log -c port=SWD mode=HOTPLUG -sfi .\image.sfi hsm=1 slot=0 -rsse C:\Program Files\STMicroelectronics\STM32Cube\STM32CubeProgrammer\bin\RSSe\H5\enc_signed_RSSe_SFI_STM32H5_v2.0.0.0.bin -mcsv .\module.mcsv
This command starts the SFI process with:
- sfi global license
- module with license
and proceeds with the installation:
STM32_Programmer_CLI.exe -log .\sfi.log -c port=SWD mode=HOTPLUG -sfi .\image.sfi hsm=0 license=.\sfi_global_license.bin -rsse C:\Program Files\STMicroelectronics\STM32Cube\STM32CubeProgrammer\bin\RSSe\H5\enc_signed_RSSe_SFI_STM32H5_v2.0.0.0.bin -mcsv .\module.mcsv
This command starts the SFI process with:
- sfi global license
- module without license
and proceeds with the installation:
STM32_Programmer_CLI.exe -log .\sfi.log -c port=SWD mode=HOTPLUG -sfi .\image.sfi hsm=0 license=.\sfi_global_license.bin -rsse C:\Program Files\STMicroelectronics\STM32Cube\STM32CubeProgrammer\bin\RSSe\H5\enc_signed_RSSe_SFI_STM32H5_v2.0.0.0.bin
This command starts the SFI process:
- with sfi global license
- without module
and proceeds with the installation:
STM32_Programmer_CLI.exe -log .\sfi.log -c port=SWD mode=HOTPLUG -sfi .\image.sfi hsm=0 license=.\sfi_global_license.bin -rsse C:\Program Files\STMicroelectronics\STM32Cube\STM32CubeProgrammer\bin\RSSe\H5\enc_signed_RSSe_SFI_STM32H5_v2.0.0.0.bin
You can check the log of the process saved in the file sfi.log:
-------------------------------------------------------------------
STM32CubeProgrammer v2.14.0
-------------------------------------------------------------------
ST-LINK SN : 003600374D46501220383832
ST-LINK FW : V3J10M3
Board : STM32H573I-DK
Voltage : 3.29V
SWD freq : 8000 KHz
Connect mode: Hot Plug
Reset mode : Software reset
Device ID : 0x484
Revision ID : --
Device name : STM32H5xx
Flash size : 2 MBytes
Device type : MCU
Device CPU : Cortex-M33
BL Version : 0xE4
SFSP Version: v2.4.0
Protocol Information : static
SFI File Information :
SFI file path : .\image.sfi
SFI license file path : .\HSM_License_V1.bin
SFI header information :
SFI protocol version : 2
SFI total number of areas : 11
SFI image version : 0
SFI Areas information :
Parsing Area 1/11 :
Area type : H
Area size : 16
Area destination address : 0x0
Parsing Area 2/11 :
Area type : O
Area size : 112
Area destination address : 0xFFD0100
Parsing Area 3/11 :
Area type : O
Area size : 272
Area destination address : 0xFFD0200
Parsing Area 4/11 :
Area type : O
Area size : 192
Area destination address : 0xFFD09D0
Parsing Area 5/11 :
Area type : O
Area size : 112
Area destination address : 0xFFD0A80
Parsing Area 6/11 :
Area type : S
Area size : 102952
Area destination address : 0x0
Parsing Area 7/11 :
Area type : S
Area size : 99350
Area destination address : 0x0
Parsing Area 8/11 :
Area type : F
Area size : 5744
Area destination address : 0x8100000
Parsing Area 9/11 :
Area type : K
Area size : 16
Area destination address : 0x0
Parsing Area 10/11 :
Area type : m
Area size : 131072
Area destination address : 0x8172000
Parsing Area 11/11 :
Area type : C
Area size : 48
Area destination address : 0x0
Warning: Option byte: BOOT_UBE, value: 0xB4, was not modified.
Warning: Option bytes are unchanged, Data won't be downloaded
Time elapsed during option bytes configuration: 00:00:00.002
Reconnecting...
Reconnected !
Reconnecting...
Reconnected !
Time elapsed during option bytes configuration: 00:00:02.442
ST-LINK SN : 003600374D46501220383832
ST-LINK FW : V3J10M3
Board : STM32H573I-DK
Voltage : 3.29 V
SWD freq : 8000 kHz
Connect mode: Hot Plug
Reset mode : Software reset
Device ID : 0x484
Revision ID : --
Warning: Option byte: SECBOOT_LOCK, value: 0xC3, was not modified.
Warning: Option bytes are unchanged, Data won't be downloaded
Time elapsed during option bytes configuration: 00:00:00.004
Warning: Option Byte: SECBOOTADD, value: 0xC0000, was not modified.
Warning: Option Byte: SECWM1_END, value: 0x7F, was not modified.
Warning: Option Byte: SECWM1_STRT, value: 0x0, was not modified.
Warning: Option Byte: SECWM2_END, value: 0x7F, was not modified.
Warning: Option Byte: SECWM2_STRT, value: 0x0, was not modified.
Warning: Option Byte: SRAM1_3_RST, value: 0x1, was not modified.
Reconnecting...
Reconnected !
Time elapsed during option bytes configuration: 00:00:01.253
ST-LINK SN : 003600374D46501220383832
ST-LINK FW : V3J10M3
Board : STM32H573I-DK
Voltage : 3.29 V
SWD freq : 8000 kHz
Connect mode: Hot Plug
Reset mode : Software reset
Device ID : 0x484
Revision ID : --
Reconnecting...
Reconnected !
Reconnecting...
Reconnected !
Time elapsed during option bytes configuration: 00:00:02.884
ST-LINK SN : 003600374D46501220383832
ST-LINK FW : V3J10M3
Board : STM32H573I-DK
Voltage : 3.29 V
SWD freq : 8000 kHz
Connect mode: Hot Plug
Reset mode : Software reset
Device ID : 0x484
Revision ID : --
Installing RSSe
Memory Programming ...
Opening and parsing file: enc_signed_RSSe_SFI_STM32H5_v2.0.0.0.bin
File : enc_signed_RSSe_SFI_STM32H5_v2.0.0.0.bin
Size : 53.81 KB
Address : 0x20054100
Erasing memory corresponding to segment 0:
Download in Progress:
File download complete
Time elapsed during download operation: 00:00:00.134
MCU Reset
ST-LINK SN : 003600374D46501220383832
ST-LINK FW : V3J10M3
Board : STM32H573I-DK
Voltage : 3.29 V
SWD freq : 8000 kHz
Connect mode: Hot Plug
Reset mode : Software reset
Device ID : 0x484
Revision ID : --
Get RSSe status...
RSS version = 2.2.0
RSSe version = 2.0.0
Starting SFI
Processing license...
Get RSSe status...
Processing Image Header
Get RSSe status...
Processing Area 1...
Get RSSe status...
Area Address = 0x0
Area Type = H
Processing Area 2...
Get RSSe status...
Area Address = 0xFFD0100
Area Type = O
Processing Area 3...
Get RSSe status...
Area Address = 0xFFD0200
Area Type = O
Processing Area 4...
Get RSSe status...
Area Address = 0xFFD09D0
Area Type = O
Processing Area 5...
Get RSSe status...
Area Address = 0xFFD0A80
Area Type = O
Processing Area 6...
Get RSSe status...
Area Address = 0x0
Area Type = S
Processing Area 7...
Get RSSe status...
Area Address = 0x0
Area Type = S
Processing Area 8...
Get RSSe status...
Area Address = 0x8100000
Area Type = F
Processing Area 9...
Get RSSe status...
Area Address = 0x0
Area Type = K
MCSV file parsing...
Total modules number: 1
+ Module number : [0]
Name : .\module.smu
Type : Global license
Size : 128.00 KB
Address : 0x08172000
Prepare module payload with license data...
Processing Area 10...
Get RSSe status...
Area Address = 0x8172000
Area Type = m
Processing Area 11...
Can not verify last area
Area Address = 0x0
Area Type = C
SFI Process Finished!
SFI file .\image.sfi Install Operation Success
Time elapsed during SFI install operation: 00:00:18.984
At this step, the device is programmed with the secure manager, the module, the OEM nonsecure application, and the option bytes. The product state is Closed or Locked.
4.5. Troubleshooting
In case of failure:
- check sfi.log
- if not in Locked state, run the \STM32Cube_FW_H5\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\DA\regression.bat to come back in Open state and be able to launch a new SFI procedure.
5. References