1. What is the Secure Manager package ?
The Secure Manager is an STMicroelectronics trusted execution environment security framework that is compliant with Arm® Platform Security Architecture (PSA) specifications for Cortex®-M (Armv8-M).
The Secure Manager is aiming at simplifying the security development cycle of embedded applications by providing ready to use security services developed according to best practices.
It is linked to our STM32Cube ecosystem and made easy to be installed within our selected STM32 devices.
The Secure Manager is targeting a certification based on PSA level 3 and SESIP3.
Easy to be installed into STM32 products by the customers on their production lines, the Secure Manager package offers a ready-to-use, high-performance, and certified solution to support the Secure Boot, root of trust, cryptography, internal trusted storage, initial attestation, and firmware update functions as defined by the Arm® PSA specifications.
Main features are:
- Arm PSA standard and API compliancy
- Arm PSA services
- Secure Boot
- Cryptography
- Internal trusted storage
- Initial attestation
- Firmware Update
- Multiple-tenant software IP protection
- Sandboxed secure services (PSA isolation level 3)
- Security certified (target)
- PSA Certified L3
- GlobalPlatform SESIP3
2. Secure Manager package overview
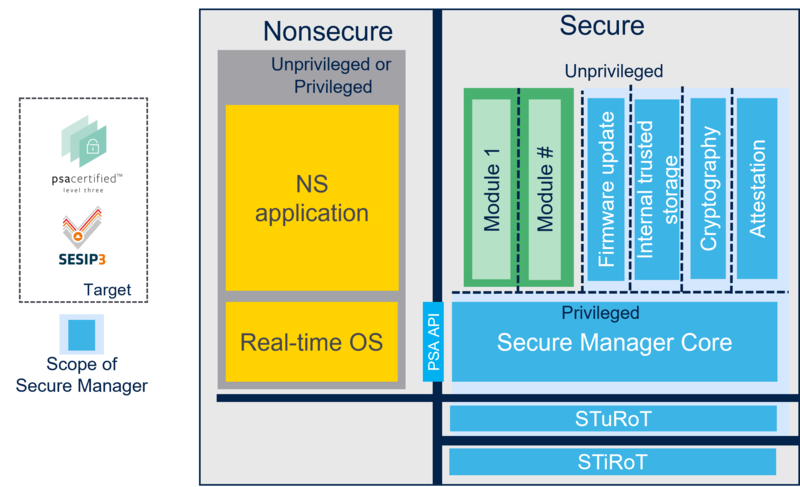
The Secure Manager package is executed in secure processing environment (SPE).
It is composed of the STuRoT plus the Secure Manager.
It is responsible for Secure Boot and Secure Firmware Update, and it provides secure services to nonsecure (NS) applications at runtime.
The Secure Manager package is composed of:
- A 2-level Root of Trust
- An immutable Root of Trust (STiRoT)
- An updatable Root of Trust (STuRoT)
- The Secure Manager core
- Secure Services such as
- Cryptography
- Initial attestation
- Trusted storage
- Firmware update
Additionally, trusted applications, also called modules, can be added by the user, but are not part of the Secure Manager package.
The following figure describes the Secure Manager package architecture.
2.1. Secure Manager components
2.1.1. Immutable Root of Trust (STiRoT)
The immutable Root of Trusted named further STiRoT is responsible for the first stage secure boot and secure firmware update.
The following firmware can be updated:
- STuRoT
During update, integrity, authenticity and confidentiality are covered.
For more details, go to STiRoT article.
2.1.2. Updatable Root of Trust (STuRoT)
The updatable Root of Trusted named further STuRoT is responsible for the second stage secure boot and secure firmware update.
The following firmware can be updated:
- Non-secure application
- Secure Manager (Secure Manager core and secure services)
- Secure modules (updatable independently from the Secure Manager)
During the update, the integrity, authenticity and confidentiality is ensured.
2.1.3. Secure Manager core
The Secure Manager core (SM core) is responsible for supporting the following secure core services:
- Isolation between non-secure application and Secure Manager (using TrustZone®)
- Isolation between secure services (using MPU)
- Communication between non-secure application and secure services, and between secure services themselves (using inter-processor communication - IPC)
- Interrupt handling
- Scheduling of secure services and interrupts
The Secure Manager core is also responsible for multiple-tenant software IP protection.
It is implemented as a secure service that is protected from other software (non-secure application, secure services) using full sandboxing (PSA L3 isolation).
The IP protection is also ensured when the software is installed and updated, thanks to the Secure Firmware Update function.
To develop proprietary secure services, the Secure Manager core supplies PSA API and extensions.
These APIs are used by a secure service to communicate with others secure services, or to access hardware resources.
2.1.4. Secure services
The Secure Manager package is responsible for supplying secure services at runtime. These services can be used by non-secure applications and other secure services.
The following services are supported:
- PSA cryptography: it supplies cryptographic services such as authentication or encryption, based on hardware cryptographic acceleration and side-channel resistance.
- PSA internal trusted storage: it supplies services for storing in internal flash memory the most important assets (such as key and data), ensuring integrity, authenticity, and confidentiality. To be noticed that ITS storage is encrypted.
- PSA attestation: it supplies services to authenticate a device. To do this, a signed token is generated for each device, which is later authenticated by a server.
- PSA firmware update: it supplies services to download new firmware images and perform image update.
2.1.5. Secure modules or trusted applications
A secure module (also named trusted application) is a secure service that can be implemented by an OEM. For this purpose, a secure module development kit (SMDK) is available.
To be noticed that a secure module is installed and updated independently from the Secure Manager image.
2.2. Secure Manager functions
2.2.1. Configurability
The Secure Manager package can be configured during the installation phase using parameters selected by the OEM, such as the non-secure application installation key, the number of modules, and the ITS storage size.
2.2.2. Security functions
The Secure Manager package supports the following STM32Trust security functions:
- Secure Boot
- Secure Firmware Install/Update
- Silicon device life cycle
- Isolation
- Secure Storage
- Cryptography
- Secure manufacturing
- Attestation
- Software IP protection
- Abnormal situation handling
Refer to stm32trust/security functions[1] for the definition of the security functions.
3. Secure Manager package ecosystem
The Secure Manager package is delivered with an ecosystem used to handle its life cycle.
This ecosystem is composed of:
- The Secure Manager access kit (SMAK): used to develop non-secure applications using Secure Manager services
- The secure module development kit (SMDK): used to develop secure modules and associated APIs to access these modules from non-secure applications.
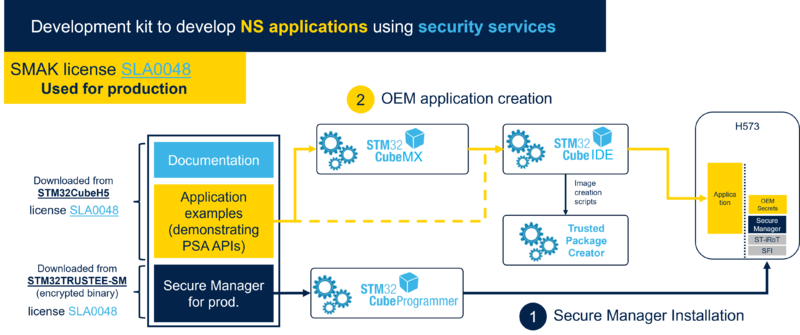
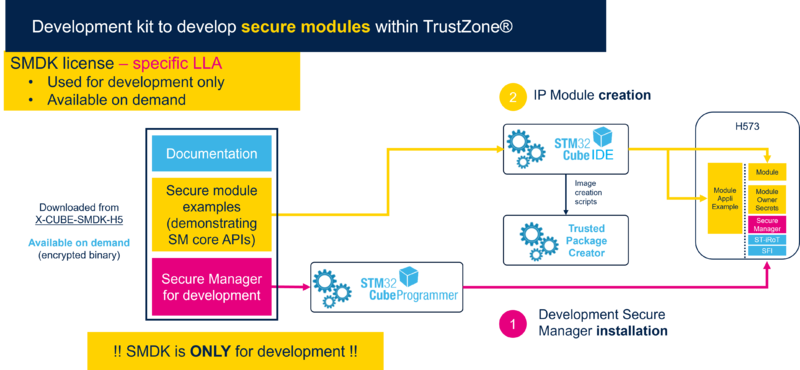
The following diagram shows the Secure Manager development and installation flow.
The SMDK is used for module development and the SMAK is used for non-secure application development, respectively.
During the flow:
- STMicroelectronics develops the encrypted Secure Manager image
- Module owner develops the encrypted module image
- OEM develops its non-secure application image and installs the whole images
The following diagram shows the Secure Manager ecosystem.
It includes tools used for development, image creation and installation.

3.1. Secure Manager access kit (SMAK)
The SMAK provides the environment to develop non-secure application that uses the Secure Manager services.
It is composed of:
- Secure Manager package, available as an encrypted image from st.com (STM32TRUSTEE-SM)
- It is delivered under the SLA0048 (PLEASE DO LINK ON SLA0048, remove this line !!!!!!!!!!!!!!!!!!!!) software license agreement.
- It can be used for production purposes.
- STM32Cube embedded firmware package containing:
- Templates and examples to develop an non-secure application
- Scripts to provision/install the Secure Manager package
- STM32 Trusted Package Creator (PLEASE USE RIGHT NAME!!!!!!!!!!!!!!!!!!!!!!!!) to build signed and encrypted images
- STM32CubeProgrammer (PLEASE MAKE LINK ON CUBE SITE!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!) to program signed and encrypted images
- STM32CubeMX (PLEASE MAKE LINK ON CUBE SITE!!!!!!!!!!!!!!!!!!!!!!!!!!!!!), to configure and generate non-secure application code (using Secure Manager package APIs)
- IDEs
3.2. Secure module development kit (SMDK)
The SMDK provides the environment for developing secure modules.
The SMDK is composed of:
- Secure Manager package, available as an encrypted image from st.com (STM32TRUSTEE-SM[2])
- It must be used for development purposed only.
- It features UART trace capability.
- It is available under a signed license agreement - Contact your ST representative.
- STM32Cube embedded firmware package (PLEASE MAKE LINK TO CUBE!!!!!!!!!!!!!!!!!) containing templates and examples to develop a secure module
- STM32 Trusted Package Creator (PLEASE MAKE LINK TO CUBE!!!!!!!!!!!!!!!!!!!) to build signed and encrypted images
- STM32CubeProgrammer ((PLEASE MAKE LINK TO CUBE!!!!!!!!!!!!!!!!!!!!!) to program signed and encrypted images
- IDEs
The SMDK can also be used to securely install and update secure modules
4. To go further
For details on Secure Manager for H5, please see Secure Manager for STM32H5.
5. Abbreviations
IPC: Inter-processor communication
NS: Nonsecure
NSPE: Nonsecure processing environment
SPE: Secure processing environment
SMAK: Secure Manager access kit
SMDK: Secure module development kit
STiRoT: STMicroelectronics immutable root of trust
STuRoT: STMicroelectronics updatable root of trust
6. References
Platform Security Architecture (PSA)
PSA Security Model