Introduction to Debug Authentication for STM32H5 MCUs
1. Debug Authentication
- Debug authentication controls
- Debug opening
- Regressions
- It can be used
- During development
- During manufacturing
- For field return analysis
- Features
- When TZ disabled: usage of a password (very similar to U5). Only regression possible
- When TZ enabled: usage of cryptography (certificates). Regressions and debug opening
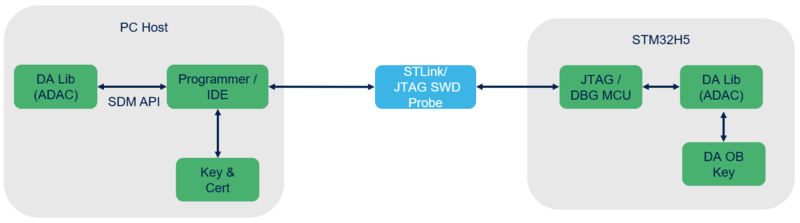
- Debug Authentication principle
- Uses JTAG dedicated access point (ap0) to communicate with the chip
- Secure protocol defined by ARM : PSA ADAC V1.0. (Authenticated Debug Access Control)
2. Debug Authentication - STM32H503 device
Provisioning with password management
- STM32H503 doesn't provide OB-Key area and uses OTP(One time programming) to store the provisioning data
- Provisioning data is the HASH (SHA256) of the Password
- STM32TrustedPackageCreator is used to generate the Hash of the password choosen by user (16 bytes) adding SHA256 to ensure integrity
Debug Authentication allows to control
- Full Regression thanks to the Debug Authentication password
- Debug Authentication password has to be provisioned in OTP to allow this regression
Getting started with Debug Authentication
You can refer to the following page for getting started example of DA access on STM32H503 devices :
How to start with DA access on STM32H503
3. Debug Authentication - STM32H563/573 device when TzustZone disabled
Provisioning with password management
- the provisioning data is located at beginning of the OBK-HDPL1 area
- Provisioning data is the HASH (SHA256) of the Password
- STM32TrustedPackageCreator is used to generate the obk files containing the HASH of the Debug Authentication password adding SHA256 to ensure integrity
Debug Authentication allows to control
- Full Regression thanks to the Debug Authentication password
- Debug Authentication password has to be provisioned in OBKeys to allow this regression
Getting started with Debug Authentication
You can refer to the following page for getting started example of DA access when TrustZone is disabled:
How to start with DA access on STM32H573 – TrustZone disabled
4. Debug Authentication - STM32H563/573 device when TzustZone enabled
Provisioning with certificate management
- the provisioning data is located at beginning of the OBK-HDPL1 area
- Provisioning data contain
- HASH (SHA256) of the root Certificate Pub Key
- SOC_PERMISSION: 16 bits defining the permissions authorized by default
- STM32TrustedPackageCreator is used to generate the obk files containing the provisioning datas adding SHA256 to ensure integrity
Debug Authentication allows to control
- Re-enabling debug possibility
- Partial or full regression
To perform Debug Authentication
- the chip must be provisioned with
- ECC public key
- SOC_PERMISSION: 16 bits defining the permissions authorized by default
- a certificate signed by a private ECC has to be created to be able to authenticate, which embeds
- ECC public key
- PERM_MASK_CERT : which describes the capabilities associated with this certificate.
Getting started with Debug Authentication You can refer to the following pages for getting started example of DA access when TrustZone is enabled: