1. Introduction
In the context of the Secure Manager, an RTOS can be used. This article will explore how an RTOS can be used with the Secure Manager, with a focus on the mechanism provided to ensure secure, thread-safe calls.
Prerequisite:
- Installed the Secure Manager
- Have a nonsecure application compatible with the Secure Manager
- Have the RTOS library chosen by the user imntegrated in the nonsecure application
2. Implementation example
Using the Secure Manager from a nonsecure application is used in a single thread, which does not pose any concurrent access to it. To have a real-time operating system multithreading application while making calls to the secure manager, it is necessary to protect these calls. This ensures that only one call at a time can be made in the Secure Manager.
2.1. Thread-safe secure calls
The implementation will protect calls through the interface functions between the Secure Manager and the nonsecure application.
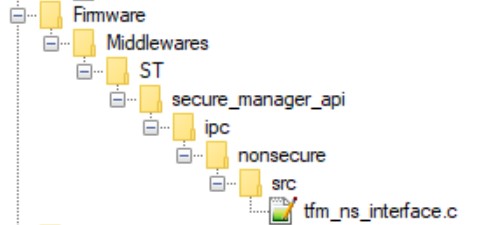
There is a mechanism in the middleware secure_manager_api that interfacing with the Secure Manager.
This mechanism, based on functions defined as __weak, will have to be re-implemented by integrating a protection, called mutex.
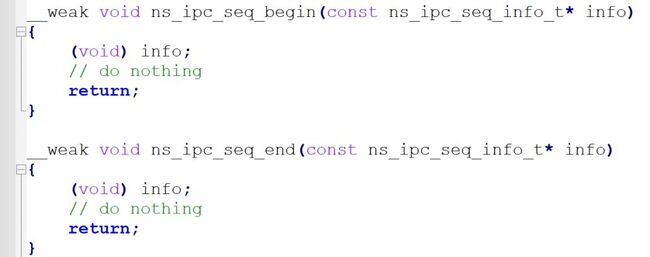
The functions ns_ipc_seq_begin and ns_ipc_seq_end, which are declared by default in the Secure Manager in the file tfm_ns_interface.c, will need to be re-implemented in the RTOS project due to multithreaded use.
2.2. Step by step implementation
Here are the different steps to follow, to implement mutex in the Secure Manager with RTOS in your project in the file where the user decide to reimplement interface function :
- Initialize the mutex
- Create the mutex
- Implement the acquisition and release of the mutex in interface functions.
2.2.1. Detailed example applied with FreeRTOS.
1. Declare a mutex and initialize it to 0 :
static SemaphoreHandle_t nsIpcMutex = { 0 };
2. Create a function that creates the mutex and assigns it to the nsIpcMutex variable. If the mutex creation fails, log an error:
void tfm_ns_interface_init( void )
{
nsIpcMutex = xSemaphoreCreateMutex();
if(nsIpcMutex == NULL)
{
// Logging Error
}
}
3. Re-implement the acquisition and release of the mutex with functions defines in semphr.c from library FreeRTOS, in the ns_ipc_seq_begin and ns_ipc_seq_end functions reimplemented in your project.
void ns_ipc_seq_begin(const ns_ipc_seq_info_t* info)
{
/* Lock mutex */
if(nsIpcMutex != NULL)
{
xSemaphoreTake(nsIpcMutex, portMAX_DELAY );
}
….
}
void ns_ipc_seq_end(const ns_ipc_seq_info_t* info)
{
/* Unlock mutex */
if(nsIpcMutex != NULL)
{
xSemaphoreGive(nsIpcMutex);
}
….
}
For more concrete examples, an actual implementations can be found in X-Cube-AWS & X-Cube-Azure using the Secure Manager with a real-time operating system.