This message will disappear after all relevant tasks have been resolved.
Semantic MediaWiki
There are 1 incomplete or pending task to finish installation of Semantic MediaWiki. An administrator or user with sufficient rights can complete it. This should be done before adding new data to avoid inconsistencies.1. Introduction
It is advised to start by reading the New product state article.
From the development phase until the maintenance phase a product can be configure under many product states ( also called lifecycle states).
The lifecycle controls the access to code and data.
This article lists in which product states a STM32H5 can be configured.
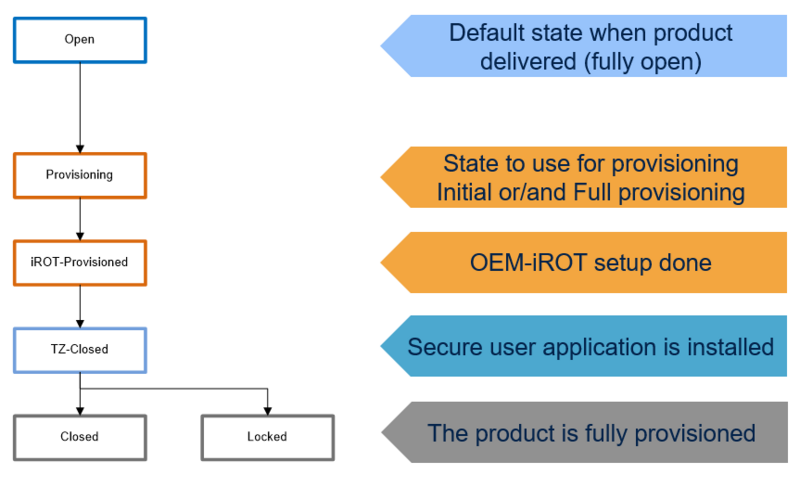
2. Product states
2.1. Product state : Open
- This state is mainly used during the development phase since the device is fully open.
- Debug is fully open.
- The Trust Zone can be disabled or enabled (TZEN option byte programming).
- Bootloader is usable.
- This state is mainly used during the development phase since the device is fully open.
2.2. Product state : provisioning
- This state is used during the provisioning.
- It is the device state during the provisioning script execution (Provisioning.bat given as an example in STM32CubeH5 firmware).
- So, this state is not part of the proposed state selectable at the end of the script execution.
- The debug is only available when executing a nonsecure user application.
- The Trust Zone can be disabled or enabled (TZEN option byte programming).
- Bootloader is usable.
- Secure Firmware install can be launched in this state (not anymore possible in the following states).
- This state is used during the provisioning.
2.3. Product state : Provisioned
- In this state, the OEM-iROT setup is done.
- Debug is available only when executing a nonsecure user application.
- Debug access for secure applications can be available by launching the Debug Authentication (see Debug Authentication setting).
- The OEM-iROT can launch the bootloader if the verification of the code located in the next isolation level is failing (authentication, integrity, or missing code)
- In this state, the OEM-iROT setup is done.
2.4. Product state : TZ-Closed
- The Trust Zone closed state is used when
- the OEM-iROT and the secure user application are provisioned (case 1)
- the OEM-iROT and the uROT+Secure user application are provisioned (case2) (see section 5.1.2).
- For case 2, the uROT allows updating the next isolation level (Code and Data).
- uROT can launch the bootloader if the verification of the code located in the next isolation level is failing (authentication, integrity, or missing code).
- uROT can launch the bootloader if the verification of the code located in the next isolation level is failing (authentication, integrity, or missing code).
- The debug is only available when executing a nonsecure user application.
- Debug access for secure applications can be available by launching the Debug Authentication (see Debug Authentication setting).
2.5. Product state : Closed
- This state occurs with the fully provisioned product.
- The debug is fully closed but can be opened by launching the Debug Authentication (see Debug Authentication setting).
- This state occurs with the fully provisioned product.
2.6. Product state : Locked
- This state is used with the fully provisioned product without any more changes.
- Locked is a final unchangeable product state. No method can modify the embedded firmware and product configuration.
- The debug is definitively closed and cannot be reopened through debug authentication.
- No regression is possible anymore
- This state is used with the fully provisioned product without any more changes.