1. What is debug authentication ?
Debug authentication is a process used to properly disable the security features on the STM32. The user leverages on the debug authentication security feature to either:
- Perform secure regression testing on the OPEN or TZ-CLOSED product states, erasing user data in: user flash memory, SRAM and OBKeys.
- Safely re-open debug access on the STM32.
Debug authentication is only used when the STM32 is CLOSED product state.
Debug authentication only grants its services when user enters a legitimate user password or a certificate authentication.
The STM32 life cycle management drives the STM32 debug authentication method, password or certificate. Refer to the life-cycle management section of the appropriate STM32 reference manual on how to implement the debug authentication security feature.
The user sends a password or certificicate to the STM32 via a limited debug access port that does not grant access to STM32 hardware resources such as the CPU registers, memory, peripheral registers, and so on. When a debug access on a closed device is opened, a new debug access port is also opened, granting access to the STM32 hardware resources.
Refer to the following itmes for more information:
- STM32 Product State Life cycle
- STM32 ARM TrustZone enablement or not.
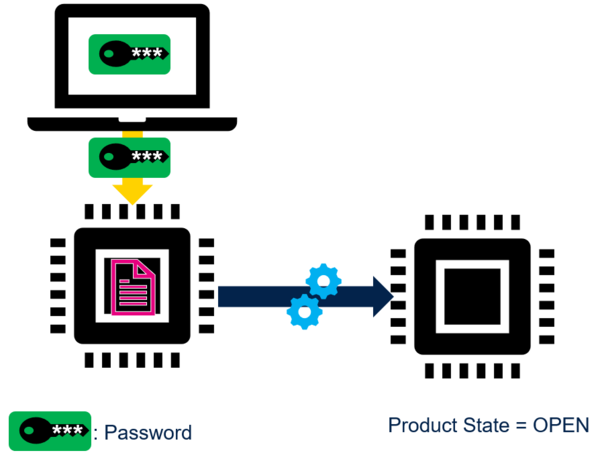
1.1. Password
In order to access the debug authentication feature, the host sends the debug authentication password to the STM32. When the STM32 recieves the password, it verifies that it corresponds to the one that is provisioned.
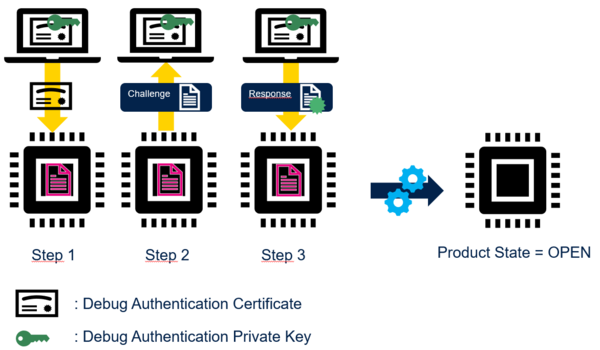
1.2. Certificate
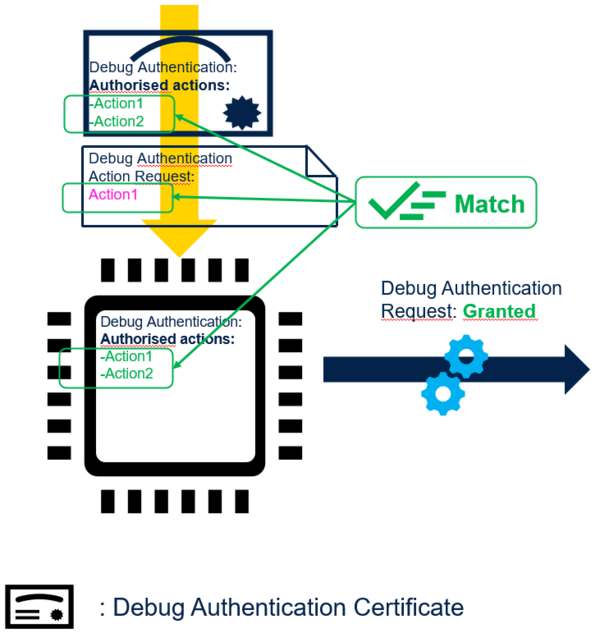
When the user access the debug authentication feature (regression or debug re-opening), he sends first a certificate and a debug authentication action request to the STM32. When the STM32 recieves the certificate, it verifies that:
- Certificate fits the one that is provisioned.
- The authorized actions sent with the certificate matches the ones provisioned.
- The action request match the authorized action list carried by the certificate.
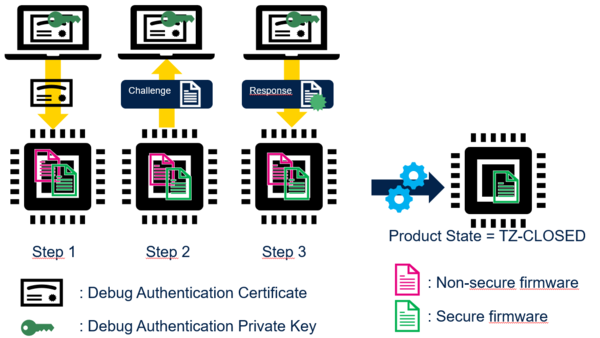
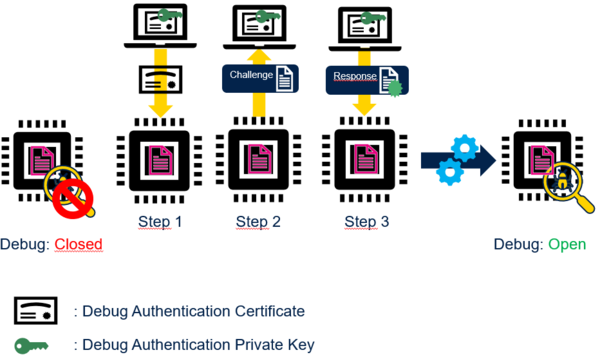
The STM32 starts the challenge-response procedure (Step 2 and Step 3): the STM32 verifies that the host owns the debug authentication private key before performing the requested action (regression or debug re-opening).
The certificate carries the requested action.
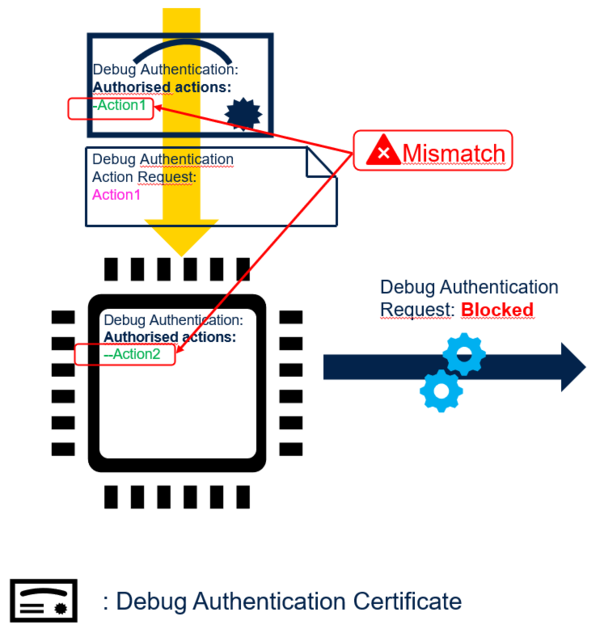
The next figure illustrates how the STM32 blocks the debug authentication action request when authorized actions in certificate do not match the provisioned authorized actions.
The figure below illustrates how the STM32 blocks the debug authentication action request because the action request does not fit with certificate authorized actions.
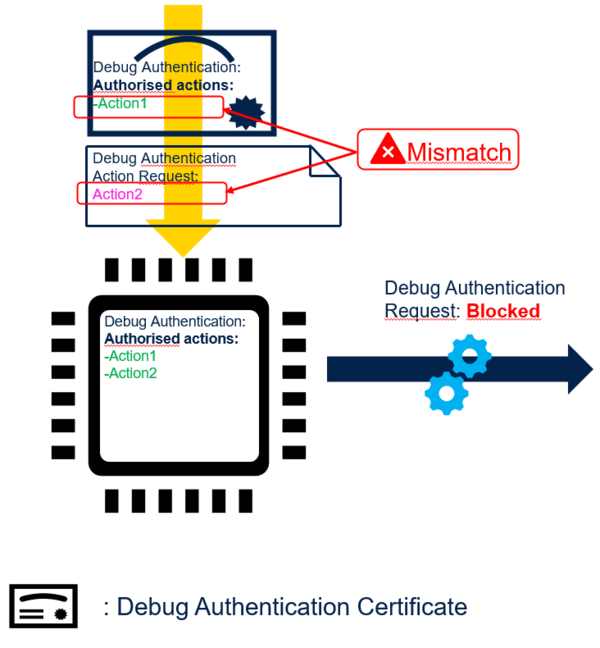
The figure below illustrates that the certificate authorized actions fits the provisioned authorized action and the action request fits the certificate authorized actions, then STM32 grants debug authentication action request.
2. Provisioning
Before configuring STM32 in a product state below PROVISIONING (i.e. PROVISONED, TZ-CLOSED or CLOSED) , user must provision either:
- The hash of the Certificate Public Key and Authorized Actions. Authorized actions are a combination of Regression, Partial Regression and Debug re-opening.
or
- The hash of the Password.
3. Regression
3.1. Full regression
Debug Authentication erases full user Flash, SRAM and OBKEys1. Full regression erases Debug Authentication Provisioned data, i.e. Certificate and Authorized Actions, hence user must provision again Debug Authentication data. After Full regression STM32 is in product state OPEN.
Note1: When STM32 supports OBKeys.
3.2. Partial regression
Debug Authentication erases non-secure user Flash, non-secure SRAM and non-secure OBKEys1. After partial regression STM32 is in product state TZ-CLOSED.
Please note that STM32 not supporting TrustZone or not enabling TrustZone do not support Partial regression.
Note1: When STM32 supports OBKeys.
4. Debug Re-opening
Only Debug Authentication by Certificate supports Debug Re-opening. After Debug Re-opening user can debug STM32. Debug Re-opening does not change STM32 product state. Debug Re-opening is temporary, power off the STM32 disables Debug Re-opening and Debug is closed again.