This page explains how to use the STM32 cryptographic firmware library software expansion for STM32Cube package once you've downloaded it.
1. Package Structure & Contents
After uncompressing the package, you'll have this usual folder structure: File:ADD AN IMAGE OF THE FOLDER CONTENTS
- ...\Drivers\STM32xx_HAL_Drivers
- Help on HAL/LL drivers
- HAL release notes
- HAL and LL drivers source files
- ...\Drivers\BSP
- BSP drivers for all supported boards
- Drivers for all the external components used on the supported boards
- ...\Drivers\CMSIS
- CMSIS files that define peripherals register declaration, bit definition and address mapping
- CMSIS files that define peripherals register declaration, bit definition and address mapping
- ...\Middlewares
- Middleware libraries
- Middleware release notes
- Middleware libraries
- ...\Projects
- STM32CubeProjectsList.html, an exhaustive list of all applications supported for each board
- Then organized by board / feature, a set of applications demonstrating various cryptographic algorithms provided for several compatible IDEs.
The Cryptographic Library middleware folder in details:
- ...\Middlewares\ST\STM32_Cryptographic\include
- Cryptographic library header files
- ...\Middlewares\ST\STM32_Cryptographic\interface
- Low layer template files to implement in your project to use the Cryptographic Library
- ...\Middlewares\ST\STM32_Cryptographic\lib
- Cryptographic libraries to link into your project
- ...\Middlewares\ST\STM32_Cryptographic\legacy_v3
- Legacy Cryptographic library migration helpers (for more details: refer to Migration_from_previous_Cryptographic_Library_version)
- ...\Middlewares\ST\STM32_Cryptographic\CMOX.chm
- The complete Cryptographic Library API documentation
2. Creating a project that embeds the Cryptographic Library
2.1. Select a library
Add the library corresponding to your needs to your project.
Example: choose libSTM32Cryptographic_CM33.a to build a project for a Arm® Cortex®-M33 based STM32 SoC.
2.2. Include path
Add the path to the include folder to your project settings.
2.3. Interface files
- Copy the cmox_low_level_template.c file from the interface folder to your project specific source folder, renaming it into “cmox_low_level.c”.
- Add this copied file to your project.
- Tune this file by including the right STM32 HAL driver header instead of the comment:
/* #include "stm32<series>xx_hal.h" */
2.4. Implement your application
Everything is ready, you can now write your own application calling the cryptographic library services.
3. Lirary configuration
3.1. Link time configuration mechanism
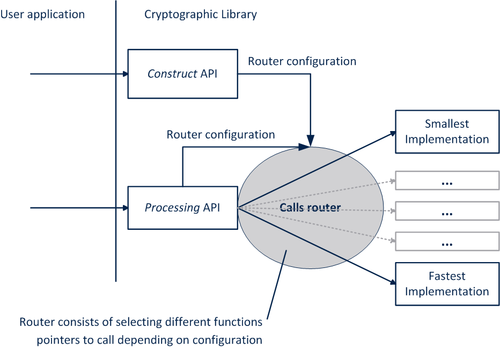
The Cryptographic Library, instead of being built under different configurations, incorporates different implementations of the same service with different levels of performance and/or size.
The implementation to use is selected either in the service configuration through the Construct API or in the service Processing API.
Examples of configuration selection:
- Cipher AES CBC encryption: shall be done either in the call to cmox_cbc_construct (when doing the encryption on several API calls) or in the call to cmox_cipher_encrypt (when doing the encryption on one signle API call).
- RSA: shall be done in the call to cmox_rsa_construct.
- ECDSA signature: shall be done in the call to cmox_ecc_construct and in the call to cmox_ecdsa_sign".
Note: For more details on the way to select the configuration with these APIs and others, refer to the CMOX.chm fine.