| Coming soon |
Cryptography is a fundamental block for implementing information security. It deals with algorithms that process data in order to grant certain properties, depending on the application needs:
- Data integrity services address the unauthorized or accidental modification of data. This includes data insertion, deletion, and modification. To ensure data integrity, a system must be able to detect unauthorized data modification. The goal is for the receiver of the data to verify that the data has not been altered.
- Confidentiality services restrict access to the content of sensitive data to only those individuals who are authorized to view the data. Confidentiality measures prevent the unauthorized disclosure of information to unauthorized individuals or processes.
- Identification and authentication services establish the validity of a transmission, message, and its originator. The goal is for the receiver of the data to determine its origin.
- Non-repudiation services prevent an individual from denying that previous actions had been performed. The goal is to ensure that the recipient of the data is assured of the sender’s identity.
These services can be used by one of the below cryptography branches.
1. Encryption
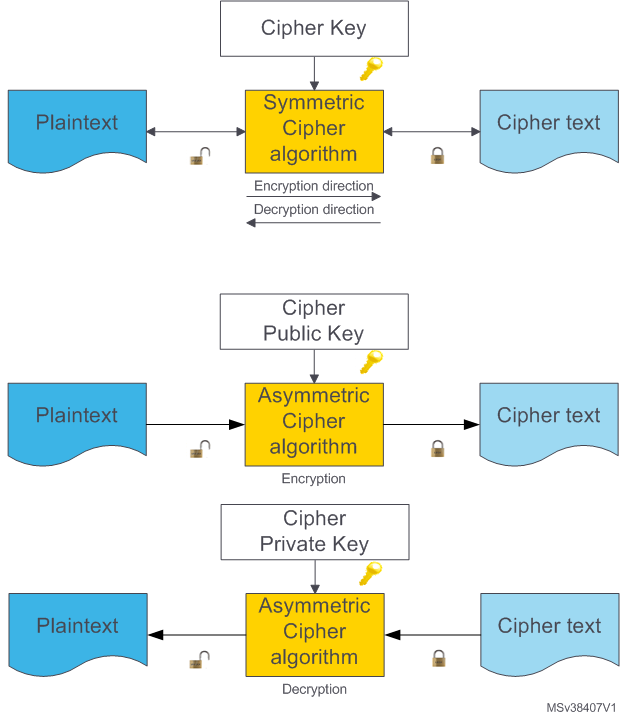
Encryption is a branch of cryptography science. It converts clear-data / raw-data, called Plaintext, to unreadable data, called Cipher-text, using secret key(s), called Cipher key(s), to perform cryptographic operations. The cipher text can be decrypted into human readable (clear text) form only using a secret key.
This operation can be based on:
- symmetric cipher: cipher that uses a single key for encryption and decryption;
- asymmetric cipher: cipher that uses two keys, one for encryption and the other for decryption.
2. Hash
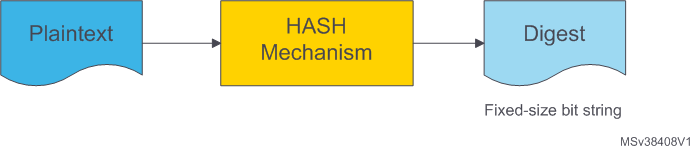
A cryptographic Hash function is a type of one-way function with additional properties. This deterministic algorithm takes an input data block of arbitrary size and returns a fixed size bit string, called digest. Hash functions are built in such a way that it is computationally infeasible to:
- find the data value given the “digest” of an unknown data,
- find two messages that hash to the same digest.
3. Message Authentication Code
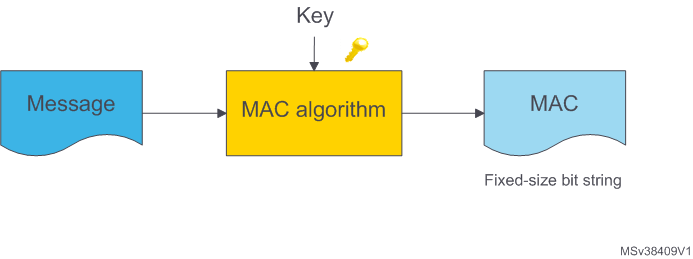
A MAC (message authentication code) requires two inputs: a message and a secret key known only by the originator of the message and its intended recipient(s). This allows the recipient(s) of the message to verify its integrity and ensure that the message’s sender has the shared secret key. If a sender doesn’t know the secret key, the hash value would then be different, allowing the recipient to understand that the message was not from the original sender.
4. Digital signature
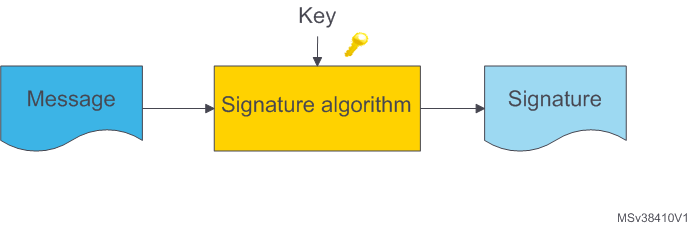
Digital signature is a mechanism by which a message is authenticated, i.e. proving that a message is effectively coming from a given sender, pretty much like a signature on a paper document. This is based on asymmetric cryptography: the private key is used to sign message, while only the public key is required to verify signatures. Therefore only the owner of the private key can compute signatures, while several other parties can verify them.
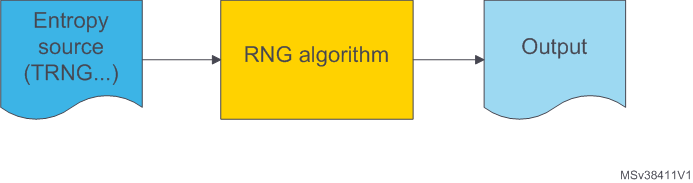
5. Random Number Generator
RNG (Random Number Generator): the secure aspect of cryptography algorithms is based on the impossibility of guessing the key or the additional, one-time usage, data used to sign a message for example. Therefore, jeys and additional data must be random. To perform this generation an RNG algorithm can be used: it receives as input a short entropy string and produces a cryptographically strong random output of much larger size.
6. Cryptographic branches usage
Each of the above branches of the cryptography standard needs to be used according to the application level requirement.
| Application | Data integrity | Confidentiality | Identification and authentication | Non-repudiation |
|---|---|---|---|---|
| Symmetric key encryption | NO | YES | NO | NO |
| Secure Hash Functions | YES | NO | NO | NO |
| MAC | YES | NO | YES | NO |
| Digital signatures | YES | NO | YES | YES |