Registered User m (→Boot the board) |
Registered User |
||
| (35 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
<bookshelf src="Book:Getting started" /> | <bookshelf src="Book:Getting started" /> | ||
{| class="st-table" style="text-align:center; margin: auto" | |||
| colspan="9" style="border-style: hidden;" | [[Image:STM32MP157X-DK2.png | 80px | link=]] | |||
{| class=" | |||
| colspan="9" style=" | |||
|- | |- | ||
| colspan="4" style="text-align:left; | | colspan="4" style="border-style: hidden; text-align:left;" | [[Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start | {{GSModuleCurrent|Let's start}}]] | ||
| colspan="5" style="text-align:right; | | colspan="5" style="border-style: hidden; text-align:right;" | [[Getting started/STM32MP1 boards/STM32MP157C-DK2/Develop on Arm® Cortex®-A7 | {{GSModuleNext|Develop on Arm® Cortex®-A7}}]] | ||
|- | |- | ||
| style="border- | | style="border-style: hidden;" | [[Image:step_category_in.png|link=]] | ||
| style=" | | style="border-style: hidden; width:110px;" | [[Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start/Unpack the STM32MP157C-DK2 board | {{GSStepNext|Unpack the board}}]] | ||
| style="border- | | style="border-style: hidden;" | [[Image:step.png|link=]] | ||
| style=" | | style="border-style: hidden; width:110px;" | [[Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start/Populate the target and boot the image | {{GSStepCurrent|Populate the target and boot the image}}]] | ||
| style="border- | | style="border-style: hidden;" | [[Image:step.png|link=]] | ||
| style=" | | style="border-style: hidden; width:110px;" | [[Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start/Execute basic commands | {{GSStepNext|Execute basic commands}}]] | ||
| style="border- | | style="border-style: hidden;" | [[Image:step.png|link=]] | ||
| style=" | | style="border-style: hidden; width:110px;" | [[Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start/Use the demo launcher | {{GSStepNext|Use the demo launcher}}]] | ||
| style="border- | | style="border-style: hidden;" | [[Image:step_category_out.png|link=]] | ||
|} | |} | ||
<br> | <br> | ||
| Line 32: | Line 25: | ||
* Set the boot switches (located at the back of the board) to the off position | * Set the boot switches (located at the back of the board) to the off position | ||
[[File: STM32MP157C-DK2_jumper_flash.jpg|frame|center|link=|boot switches position to flash the board]] | [[File: STM32MP157C-DK2_jumper_flash.jpg|frame|center|link=|boot switches position to flash the board]] | ||
* Connect USB Type A to Type C cable between PC and CN7/USB_OTG port of the STM32MP157C-DK2 board | |||
* Power up the board | * Power up the board | ||
* Press the reset button to reset the board | * Press the reset button to reset the board | ||
* | * Launch '''STM32CubeProgrammer''' to get the GUI | ||
* | [[File: STM32CubePro GUI.png|800px|center|STM32CubeProgrammer GUI]] | ||
* On the right, select USB (not STLINK, set by default) in the connection picklist and click on "Refresh" button. Serial Number is displayed if USB is detected. Click on "Connect" | |||
[[File: STM32CubePro SelectUSB.png|800px|center|Select USB for connection with board]] | |||
* Select "Open File" tab and select $HOME/STM32MPU_workspace/STM32MP15-Ecosystem-v1.x.0/stm32mp1-openstlinux-xx-yy-zz/images/stm32mp1/flashlayout_st-image-weston the FlashLayout_sdcard_stm32mp157c-dk2-trusted.tsv, in the Starter Package installation folder. | |||
* Fill the "Binaries Path" by browsing up to folder $[Starter_Pack_Path]/images/stm32mp1 | |||
[[File: STM32CubePro TSandBinary.png|800px|center|open .tsv and fill Binaries Path]] | |||
* Click on "Download" to start the flashing process. | |||
* Progress is displayed with progress bar till completion popup message. | |||
==Boot the board== | ==Boot the board== | ||
* Set the boot switches (located at the back of the board) to the | * Set the boot switches (located at the back of the board) to the ON position | ||
[[File: STM32MP157C-DK2_jumper_boot.jpg|frame|center|link=|boot switches position to boot the board]] | [[File: STM32MP157C-DK2_jumper_boot.jpg|frame|center|link=|boot switches position to boot the board]] | ||
* Power up the board | * Power up the board | ||
* Press the | * Press the "Reset "button to reset the board | ||
* After few seconds, the board starts and automatically | * After few seconds, the board starts and automatically goes through the following screens | ||
[[File: STM32MP1_uboot_splashscreen.png|thumb|upright=2|center|link=|UBoot splash screen]] | [[File: STM32MP1_uboot_splashscreen.png|thumb|upright=2|center|link=|UBoot splash screen]] | ||
[[File: STM32MP1_psplash.png|thumb|upright=2|center|link=|Linux splash screen]] | [[File: STM32MP1_psplash.png|thumb|upright=2|center|link=|Linux splash screen]] | ||
[[File: STM32MP1_weston_desktop.png|thumb|upright=2|center|link=|Weston desktop]] | [[File: STM32MP1_weston_desktop.png|thumb|upright=2|center|link=|Weston desktop]] | ||
[[File: STM32MP1_gtk_demo_launcher.png|thumb|upright=2|center|link=|GTK demo launcher]] | [[File: STM32MP1_gtk_demo_launcher.png|thumb|upright=2|center|link=|GTK demo launcher]] | ||
:* If the board power supply doesn't supply enough current (3A), the red LED indicates the issue following the rules below: | |||
:::{| | |||
! blink | |||
! console message | |||
! boot process | |||
|- | |||
| 2 times | |||
| WARNING 500mA power supply detected | |||
Current too low, use a 3A power supply! | |||
| Continue and red LED stays ON | |||
|- | |||
| 3 times | |||
| WARNING 1500mA power supply detected | |||
Current too low, use a 3A power supply! | |||
| Continue and red LED stays ON | |||
|- | |||
| forever | |||
| ERROR USB TYPE-C connection in unattached mode | |||
Check that USB TYPE-C cable is correctly plugged | |||
| stop | |||
|- | |||
| forever | |||
| USB TYPE-C charger not compliant with USB specification | |||
| stop | |||
|} | |||
<br> | <br> | ||
{| class=" | {| class="st-table" style="margin: auto" | ||
| style="border- | | style="border-style: hidden; width:120px; text-align:left" | [[Image:back_button.png|link=Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start/Unpack the STM32MP157C-DK2 board]] | ||
| style="border- | | style="border-style: hidden; width:360px; text-align:center" | [[Image:overview_button.png|link=Getting started/STM32MP1 boards/STM32MP157C-DK2]] | ||
| style="border- | | style="border-style: hidden; width:120px; text-align:right" | [[Image:next_button.png|link=Getting started/STM32MP1 boards/STM32MP157C-DK2/Let's start/Execute basic commands]] | ||
|} | |} | ||
<noinclude> | |||
{{DISPLAYTITLE:{{SUBPAGENAME}}}} | |||
__NOTOC__ | |||
[[Category:STM32MP157C-DK2 - let's start | 02]] | |||
{{PublicationRequestId | Auto}} | |||
</noinclude> | |||
Revision as of 14:43, 21 February 2020
1. Overview[edit | edit source]
This stage explains how to get, install and boot the STM32MP15 Discovery kit with the Starter Package.
2. Open a terminal[edit | edit source]
Open a terminal on the host computer.
All the commands preceded by have to be executed from the host computer terminal.
- Create your STM32MPU workspace directory on the host computer:
mkdir $HOME/STM32MPU_workspace
cd $HOME/STM32MPU_workspace
3. Check the host computer Internet access[edit | edit source]
- An Internet access through http and https protocols must be provided.
The command below enables checking for Internet access through http/https protocols:
wget -q www.google.com && echo "Internet access over HTTP/HTTPS is OK !" || echo "No internet access over HTTP/HTTPS ! You may need to set up a proxy."
If an 'OK' message is returned, the network is correctly configured.
In this case, skip the rest of this section.
Otherwise, a proxy for http/https protocols is required.
The best solution is to set this proxy through the shell variables http_proxy and https_proxy:
export http_proxy=http://<MyProxyLogin>:<MyProxyPassword>@<MyProxyServerUrl>:<MyProxyPort>
export https_proxy=http://<MyProxyLogin>:<MyProxyPassword>@<MyProxyServerUrl>:<MyProxyPort>
Check again the Internet access using the command:
wget -q www.google.com && echo "Internet access over HTTP/HTTPS is OK !" || echo "No internet access over HTTP/HTTPS ! You may need to set up a proxy."
4. Install the tools[edit | edit source]
4.1. STM32CubeProgrammer[edit | edit source]
- Create your "STM32MPU tools" directory on the host computer:
mkdir $HOME/STM32MPU_workspace/STM32MPU-Tools
mkdir $HOME/STM32MPU_workspace/STM32MPU-Tools/STM32CubeProgrammer-x.y.z
- Create a temporary directory in your STM32MPU workspace:
mkdir $HOME/STM32MPU_workspace/tmp
cd $HOME/STM32MPU_workspace/tmp
4.2. Installing the STM32CubeProgrammer tool[edit | edit source]
| STM32CubeProgrammer for Linux® host PC | STM32CubeProgrammer for Windows® host PC | |
|---|---|---|
| Download |
Version v2.20.0
unzip en.stm32cubeprog.zip | |
| Installation |
$> ./SetupSTM32CubeProgrammer-2.20.0.linux
$> export PATH=<my STM32CubeProgrammer install directory>/bin:$PATH
$> ln -s <my STM32CubeProgrammer install directory>/bin/STM32_Programmer_CLI /home/bin/STM32_Programmer_CLI
|
|
| User manual |
| |
| Detailed release note |
| |
4.3. Preparing the USB serial link for flashing[edit | edit source]
It is recommended to use the USB (in DFU mode) for flashing rather than the UART, which is too slow.
Below indications on how to install the USB in DFU mode under Linux and Windows OS, respectively.
- For Linux host PC or Windows host PC with VMWare:
The libusb1.0 package (including USB DFU mode) must be installed to be able to connect to the board via the USB port. This is achieved by typing the following command from the host PC terminal:
sudo apt-get install libusb-1.0-0
To allow STM32CubeProgrammer to access the USB port through low-level commands, proceed as follows:
cd <your STM32CubeProgrammer install directory>/Drivers/rules
sudo cp *.* /etc/udev/rules.d/
- For Windows host PC:
Run the “STM32 Bootloader.bat” file to install the STM32CubeProgrammer DFU driver and activate the STM32 microprocessor device in USB DFU mode. This driver (installed by STM32 Bootloader.bat) is provided within the STM32CubeProgrammer release package. It is located in the DFU driver folder, \Drivers\DFU_Driver.
In case of issue, refer to How to proceed when the DFU driver installation fails on Windows host PC.
To validate the installation, the DFU driver functionality can be verified by following the FAQ instructions provided in how to check if the DFU driver is functional.
5. Test[edit | edit source]
- Check that the STM32CubeProgrammer tool is properly installed and accessible:
STM32_Programmer_CLI --h
-------------------------------------------------------------------
STM32CubeProgrammer vx.y.z
-------------------------------------------------------------------
6. Download the image[edit | edit source]
6.1. For STM32MP1 series[edit | edit source]
- The STM32MP1 image (binaries) is delivered through one tarball file named
- Download and install the STM32MP1 image (binaries):
The software package is provided AS IS, and by downloading it, you agree to be bound to the terms of the software license agreement (SLA0048). The detailed content licenses can be found here.
| STM32MP1 Starter Package image - STM32MP1-Ecosystem-v6.1.0 release | |
|---|---|
| Download |
|
| Installation |
cd <working directory path>/Starter-Package
tar xvf FLASH-stm32mp1-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz
|
| Release note |
Details of the content of this software package are available in the associated STM32 MPU OpenSTLinux release note. |
- The binaries and the Flash layout files are in the <Starter Package installation directory>/stm32mp1-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11/images/stm32mp1/ directory. The most important ones are:
stm32mp1 ├── arm-trusted-firmware TF-A binaries │ ├── bl2 TF-A binary for FIP binaries creation │ │ ├── tf-a-<board name>-<boot chain>-<storage>.bin │ │ └── [...] │ ├── debug Debug binaries for TF-A │ │ ├── debug-tf-a-<board name>-<boot chain>-<storage>.stm32 Debug file for FSBL │ │ ├── tf-a-bl2-<soc name>-<boot chain>-<storage>.elf Debug symbol file for TF-A │ │ └── [...] │ ├── fwconfig TF-A device tree for FIP binaries creation │ │ ├── <board name>-fwconfig-<boot chain>-<storage>.dtb │ │ └── [...] │ ├── metadata.bin Meta data binary for METADATA partition for the supported boards │ ├── tf-a-<board name>-<boot chain>-<storage>.stm32 TF-A binary for FSBL partition │ └── [...] ├── fip FIP binaries for FIP partitions and supported boot chains │ ├── fip-<board name>-<boot chain>-<storage>.bin FIP binary for FIP partition │ ├── fip-<board name>-<boot chain>-<storage>.txt Configuration file for FIP binary content │ └── [...] ├── flashlayout_st-image-weston Flash layout files (description of the partitions) for the supported boot chains on supported boot devices and boards │ ├── extensible Flash layout files for microSD card boot device with no userfs partition but a rootfs partition extended to microSD card size │ │ ├── FlashLayout_sdcard_<board name>-extensible.tsv (recommended setup for package repository service) microSD card boot device with rootfs partition extended to microSD card size │ │ └── [...] │ ├── fastboot │ │ ├── FlashLayout_<boot device>_<board name>-fastboot.tsv │ │ └── [...] │ ├── fastboot-opteemin │ │ ├── FlashLayout_<boot device>_<board name>-fastboot-opteemin.tsv │ │ └── [...] │ ├── optee │ │ ├── FlashLayout_<boot device>_<board name>-optee.tsv │ │ └── [...] │ └── opteemin │ ├── FlashLayout_<boot device>_<board name>-opteemin.tsv │ └── [...] ├── Kernel Debug binaries for Linux kernel │ ├── config-6.6.78 Reference config file for Linux kernel │ ├── [...] │ └── vmlinux Image of the Linux kernel ├── optee OPTEE-OS binaries │ ├── debug Debug binaries for OPTEE-OS │ │ ├── tee-<board name>-<boot chain>.elf Debug symbol file for OPTEE-OS │ │ ├── tee-<board name>-<boot chain>-programmer.elf Debug symbol file for OPTEE-OS configured for usb/serial │ │ └── [...] │ ├── tee-header_v2-<board name>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-header_v2-<board name>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ ├── tee-pageable_v2-<board name>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-pageable_v2-<board name>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ ├── tee-pager_v2-<board name>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-pager_v2-<board name>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ └── [...] ├── scripts │ └── create_sdcard_from_flashlayout.sh ├── u-boot U-BOOT binaries │ ├── debug Debug binaries for U-BOOT │ │ ├── u-boot-<soc name>-<u-boot config>.elf Debug symbol file for U-BOOT │ │ └── [...] │ ├── configuration-<soc name>-<u-boot config>_defconfig Reference configuration file for U-Boot │ ├── u-boot-nodtb-<soc name>-<u-boot config>.bin U-BOOT binary for FIP binaries creation │ ├── u-boot-<board name>-<u-boot config>.dtb U-BOOT device tree for FIP binaries creation │ └── [...] ├── st-image-bootfs-openstlinux-weston-stm32mp1.bootfs.ext4 Binary for bootfs partition on eMMC and microSD card devices ├── st-image-bootfs-openstlinux-weston-stm32mp1.bootfs.manifest ├── st-image-bootfs-efi-openstlinux-weston-stm32mp1.bootfs.vfat Binary for bootfs for EFI partition on eMMC and microSD card devices ├── st-image-bootfs-efi-openstlinux-weston-stm32mp1.bootfs.manifest ├── st-image-userfs-openstlinux-weston-stm32mp1.userfs.ext4 Binary for userfs partition on eMMC and microSD card devices ├── st-image-userfs-openstlinux-weston-stm32mp1.userfs.manifest ├── st-image-vendorfs-openstlinux-weston-stm32mp1.vendorfs.ext4 Binary for vendorfs partition on eMMC and microSD card devices ├── st-image-vendorfs-openstlinux-weston-stm32mp1.vendorfs.manifest ├── st-image-weston-openstlinux-weston-stm32mp1.rootfs.ext4 Binary for rootfs partition on eMMC and microSD card devices ├── st-image-weston-openstlinux-weston-stm32mp1.rootfs.license ├── st-image-weston-openstlinux-weston-stm32mp1.rootfs-license_content.html License summary for all packages needed to feed all partitions ├── st-image-weston-openstlinux-weston-stm32mp1.rootfs.manifest ├── st-image-weston-openstlinux-weston-stm32mp1.rootfs_nand_4_256_1024_multivolumde.ubi Binary for ubi partition on NAND device └── [...]
Description:
<board name>: * stm32mp135f-dk * stm32mp157a-dk1, stm32mp157a-ev1, stm32mp157c-dk2, stm32mp157c-ed1, stm32mp157c-ev1, stm32mp157d-dk1, stm32mp157d-ev1, ,stm32mp157f-dk2, stm32mp157f-ed1, stm32mp157f-ev1 <soc name>: * stm32mp13 * stm32mp15 <boot chain>: * fastboot optee boot chain for flashing via fastboot * fastboot-opteemin opteemin boot chain for flashing via fastboot * optee optee boot chain * opteemin opteemin boot chain <boot device>: * emmc Boot via emmc storage * nor-sdcard Boot via nor storage for first stage (fsbl, fip) and files system are located on sdcard * nand-4-256-1024-sdcard Boot via nand storage for first stage (fsbl, fip) and files system are located on sdcard * sdcard Boot via sdcard storage * sdcard-EFI Boot via sdcard storage and bootfs is configurated on EFI <storage>: * emmc emmc storage * nor nor storage * nand nand storage * programmer-uart storage programmation via UART * programmer-usb storage programmation via USB * sdcard sdcard storage <u-boot config>: * default * fastboot-emmc Fastboot config enabled with MMC_DEV Id for emmc * fastboot-sdcard Fastboot config enabled with MMC_DEV Id for sdcard * programmer Programmer config enabled
6.2. For STM32MP2 series[edit | edit source]
- The STM32MP2 image (binaries) is delivered through one tarball file named FLASH-stm32mp2-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz applicable to STM32MP215F-DK
 , STM32MP257F-DK
, STM32MP257F-DK  for STM32MP23x lines evaluation
for STM32MP23x lines evaluation  , STM32MP257x-DK
, STM32MP257x-DK  and STM32MP257x-EV1
and STM32MP257x-EV1 
- Download and install the STM32MP2 image (binaries):
The software package is provided AS IS, and by downloading it, you agree to be bound to the terms of the software license agreement (SLA0048). The detailed content licenses can be found here.
| STM32MP2 Starter Package image - STM32MP2-Ecosystem-v6.1.0 release for A35-TD flavor | |
|---|---|
| Download |
Go on st.com to download the STM32MP2 Starter Package image, FLASH-stm32mp2-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz file. |
| Installation |
cd <working directory path>/Starter-Package
tar xvf FLASH-stm32mp2-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz
|
| Release note |
Details of the content of this software package are available in the associated STM32 MPU OpenSTLinux release note. |
- The binaries and the Flash layout files are in the <Starter Package installation directory>/stm32mp2-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11/images/stm32mp2/ directory. The most important ones are:
stm32mp2 ├── arm-trusted-firmware TF-A binaries for FSBL partitions and supported boot chains │ ├── bl2 TF-A BL2 binary for FIP binaries creation │ │ ├── tf-a-<board name>-<hardware security>-<boot chain>-<storage>.bin │ │ └── [...] │ ├── bl31 TF-A BL31 binary for FIP binaries creation │ │ ├── debug Debug binaries for BL31 │ │ │ ├── tf-a-bl31-<board name>-<hardware security>-<boot chain>-<storage>.elf Debug symbol file for TF-A BL31 │ │ │ └── [...] │ │ ├── <board name>-<hardware security>-<boot chain>-<storage>.dtb TF-A BL31 device tree for FIP binaries creation │ │ ├── tf-a-bl31-<board name>-<hardware security>-<boot chain>-<storage>.bin TF-A BL31 binary for FIP binaries creation │ │ └── [...] │ ├── ddr Trained DDR binary for FIP binaries creation │ │ ├── ddr_pmu-<board name>-<hardware security>-<boot chain>-<storage>.bin │ │ └── [...] │ ├── debug Debug binaries for TF-A │ │ ├── debug-tf-a-<board name>-<hardware security>-<boot chain>-<storage>.stm32 Debug file for FSBL │ │ ├── tf-a-bl2-<soc name>-<boot chain>-<storage>.elf Debug symbol file for TF-A │ │ └── [...] │ ├── fwconfig TF-A device tree for FIP binaries creation │ │ ├── <board name>-<hardware security>-fwconfig-<boot chain>-<storage>.dtb │ │ └── [...] │ ├── metadata.bin Meta data binary for METADATA partition for the supported boards │ ├── tf-a-<board name>-<hardware security>-<boot chain>-<storage>.stm32 TF-A binary for FSBL partition │ └── [...] ├── arm-trusted-firmware-m TF-M binaries │ ├── debug Debug binaries for TF-M │ │ ├── tfm-<board name>-<hardware security>_s.elf Debug symbol file for TF-M │ │ └── [...] │ ├── tfm-<board name>-<hardware security>_s.bin TF-M binary for m33 firmware as copro │ └── [...] ├── fip FIP binaries for FIP partitions and supported boot chains │ ├── fip-<board name>-<hardware security>-ddr-<boot chain>-<storage>.bin FIP binary for FIP DDR partition │ ├── fip-<board name>-<hardware security>-<boot chain>-<storage>.bin FIP binary for FIP partition │ └── [...] ├── flashlayout_st-image-weston Flash layout files (description of the partitions) for the supported boot chains on supported boot devices and boards │ ├── [...] │ ├── extensible Flash layout files for microSD card boot device with no userfs partition but a rootfs partition extended to microSD card size │ │ ├── FlashLayout_sdcard_<board name>-<hardware security>-extensible.tsv (recommended setup for package repository service) microSD card boot device with rootfs partition extended to microSD card size │ │ └── [...] │ ├── fastboot Flash layout files for flashing via fastboot with optee boot chain │ │ ├── FlashLayout_<boot device>_<board name>-<hardware security>-fastboot.tsv │ │ └── [...] │ ├── fastboot-opteemin Flash layout files for flashing via fastboot with opteemin boot chain │ │ ├── FlashLayout_<boot device>_<board name>-<hardware security>-fastboot-opteemin.tsv │ │ └── [...] │ ├── optee Flash layout files for optee boot chain │ │ ├── FlashLayout_<boot device>_<board name>-<hardware security>-optee.tsv │ │ └── [...] │ └── opteemin Flash layout files for opteemin boot chain │ ├── FlashLayout_<boot device>_<board name>-<hardware security>-opteemin.tsv │ └── [...] ├── Kernel Debug binaries for Linux kernel │ ├── config-6.6.78 Reference config file for Linux kernel │ └── vmlinux Image of the Linux kernel ├── optee OPTEE-OS binaries │ ├── debug Debug binaries for OPTEE-OS │ │ ├── tee-<board name>-<hardware security>-<boot chain>.elf Debug symbol file for OPTEE-OS │ │ ├── tee-<board name>-<hardware security>-<boot chain>-programmer.elf Debug symbol file for OPTEE-OS configured for usb/serial │ │ └── [...] │ ├── tee-header_v2-<board name>-<hardware security>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-header_v2-<board name>-<hardware security>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ ├── tee-pageable_v2-<board name>-<hardware security>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-pageable_v2-<board name>-<hardware security>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ ├── tee-pager_v2-<board name>-<hardware security>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-pager_v2-<board name>-<hardware security>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ └── [...] ├── scripts │ └── create_sdcard_from_flashlayout.sh ├── u-boot U-BOOT binaries │ ├── debug Debug binaries for U-BOOT │ │ ├── u-boot-<soc name>-<u-boot config>.elf Debug symbol file for U-BOOT │ │ └── [...] │ ├── configuration-<soc name>-<u-boot config>_defconfig Reference configuration file for U-Boot │ ├── u-boot-nodtb-<soc name>-<u-boot config>.bin U-BOOT binary for FIP binaries creation │ ├── u-boot-<board name>-<hardware security>-<u-boot config>.dtb U-BOOT device tree for FIP binaries creation │ └── [...] ├── st-image-bootfs-openstlinux-weston-stm32mp2.bootfs.ext4 Binary for bootfs partition on eMMC and microSD card devices ├── st-image-bootfs-openstlinux-weston-stm32mp2.bootfs.manifest ├── st-image-bootfs-efi-openstlinux-weston-stm32mp2.bootfs.vfat Binary for bootfs for EFI partition on eMMC and microSD card devices ├── st-image-bootfs-efi-openstlinux-weston-stm32mp2.bootfs.manifest ├── st-image-userfs-openstlinux-weston-stm32mp2.userfs.ext4 Binary for userfs partition on eMMC and microSD card devices ├── st-image-userfs-openstlinux-weston-stm32mp2.userfs.manifest ├── st-image-vendorfs-openstlinux-weston-stm32mp2.vendorfs.ext4 Binary for vendorfs partition on eMMC and microSD card devices ├── st-image-vendorfs-openstlinux-weston-stm32mp2.vendorfs.manifest ├── st-image-weston-openstlinux-weston-stm32mp2.rootfs.ext4 Binary for rootfs partition on eMMC and microSD card devices ├── st-image-weston-openstlinux-weston-stm32mp2.rootfs.license ├── st-image-weston-openstlinux-weston-stm32mp2.rootfs-license_content.html License summary for all packages needed to feed all partitions ├── st-image-weston-openstlinux-weston-stm32mp2.rootfs.manifest └── [...]
Description:
<soc name>: * stm32mp21 * stm32mp23 * stm32mp25 <board name>: * stm32mp215-df, stm32mp235f-dk, stm32mp257f-dk, stm32mp257f-ev1 <hardware security>: * if nothing declared then there is a minimal hardware configuration for RIFF profile OPEN * ca35tdcid-ostl custom hardware configuration (can be different following use-case and hardware) for RIFF profile CUSTOM (CLOSED) * ca35tdcid-ostl-m33-examples custom hardware configuration (can be different following use-case and hardware) for RIFF profile CUSTOM (CLOSED) <boot chain>: * fastboot optee boot chain for flashing via fastboot * fastboot-opteemin opteemin boot chain for flashing via fastboot * optee optee boot chain * opteemin opteemin boot chain <storage>: * emmc eMMC storage * nand NAND storage * nor NOR storage * programmer-uart storage programmation via UART * programmer-usb storage programmation via USB * sdcard microSD card storage <boot device>: * emmc boot via emmc storage * nand-4-256-1024 (nand-x-y-z) boot via nand storage * nand-4-256-1024-sdcard boot via nand storage for first stage (fsbl, fip) and files system are located on sdcard * nor boot via nor storage * nor-sdcard boot via nor storage for first stage (fsbl, fip) and files system are located on sdcard * sdcard boot via sdcard storage * sdcard-EFI boot via sdcard but bootfs is configurated on EFI <u-boot config>: * default * fastboot-emmc Fastboot config enabled with MMC_DEV Id for emmc * fastboot-sdcard Fastboot config enabled with MMC_DEV Id for sdcard * programmer Programmer config enabled
- The STM32MP2 image (binaries) is delivered through one tarball file named FLASH-stm32mp2-m33td-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz applicable to STM32MP215F-DK
 and STM32MP257x-EV1
and STM32MP257x-EV1 
- Download and install the STM32MP2 image (binaries):
The software package is provided AS IS, and by downloading it, you agree to be bound to the terms of the software license agreement (SLA0048). The detailed content licenses can be found here.
| STM32MP2 Starter Package image - STM32MP2-Ecosystem-v6.1.0 release for M33-TD flavor | |
|---|---|
| Download |
Go on st.com to download the STM32MP2 Starter Package image, FLASH-stm32mp2-m33td-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz file. |
| Installation |
cd <working directory path>/Starter-Package
tar xvf FLASH-stm32mp2-m33td-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11.tar.gz
|
| Release note |
Details of the content of this software package are available in the associated STM32 MPU OpenSTLinux release note. |
- The binaries and the Flash layout files are in the <Starter Package installation directory>/stm32mp2-m33td-openstlinux-6.6-yocto-scarthgap-mpu-v25.06.11/images/stm32mp2-m33td/ directory. The most important ones are:
stm32mp2-m33td ├── arm-trusted-firmware TF-A binaries for FSBLa partitions and supported boot chains │ ├── bl2 TF-A BL2 binary for FIP binaries creation │ │ ├── tf-a-<board name>-<hardware security>-<boot chain>-<storage>.bin │ │ └── [...] │ ├── bl31 TF-A BL31 binary for FIP binaries creation │ │ ├── debug Debug binaries for BL31 │ │ │ ├── tf-a-bl31-<board name>-<hardware security>-<boot chain>-<storage>.elf Debug symbol file for TF-A BL31 │ │ │ └── [...] │ │ ├── <board name>-<hardware security>-<boot chain>-<storage>.dtb TF-A BL31 device tree for FIP binaries creation │ │ ├── tf-a-bl31-<board name>-<hardware security>-<boot chain>-<storage>.bin TF-A BL31 binary for FIP binaries creation │ │ └── [...] │ ├── ddr Trained DDR binary for FIP binaries creation │ │ ├── ddr_pmu-<board name>-<hardware security>-<boot chain>-<storage>.bin │ │ └── [...] │ ├── debug Debug binaries for TF-A │ │ ├── debug-tf-a-<board name>-<hardware security>-<boot chain>-<storage>.stm32 Debug file for FSBL │ │ ├── tf-a-bl2-<soc name>-<boot chain>-<storage>.elf Debug symbol file for TF-A │ │ └── [...] │ ├── fwconfig TF-A device tree for FIP binaries creation │ │ ├── <board name>-<hardware security>-fwconfig-<boot chain>-<storage>.dtb │ │ └── [...] │ ├── metadata.bin Meta data binary for METADATA partition for the supported boards │ ├── tf-a-<board name>-<hardware security>-<boot chain>-<storage>.stm32 TF-A binary for FSBL partition │ └── [...] ├── arm-trusted-firmware-m TF-M binaries for FSBLm partitions and supported boot chains │ ├── debug Debug binaries for TF-M │ │ ├── debug-bl2-<board name>-<hardware security>.stm32 Debug file for FSBLm │ │ ├── tfm-<board name>-<hardware security>-<storage m33>-<storage a35>_s.elf Debug symbol file for TF-M │ │ └── [...] │ ├── key Security key used by TF-M │ │ ├── image_ns_signing_public_key-<board name>-<hardware security>-<storage m33>.pem │ │ ├── image_s_signing_private_key-<board name>-<hardware security>-<storage m33>.pem │ │ ├── image_s_signing_public_key-<board name>-<hardware security>-<storage m33>.pem │ │ └── [...] │ ├── bl2-<board name>-<hardware security>-<storage m33>.stm32 TF-M binary for FSBLm partition │ ├── ddr_phy_signed-<board name>-<hardware security>-<storage m33>.bin TF-M binary for M33ddr partition │ └── [...] ├── arm-trusted-firmware-m-cube TF-M/CubeMp2 binaries for M33FW partitions and supported boot chains │ ├── debug Debug binaries for TF-M/CubeMp2 │ │ ├── tfm-starterapp-<board name>-<hardware security>-<storage m33>-<storage a35>_CM33_NonSecure.elf Debug symbol file for TF-m/CubeMp2 │ │ └── [...] │ ├── tf-m-starterapp-<board name>-<hardware security>-<storage m33>-<storage a35>_s_ns.bin TF-M/CubeMP2 binary for M33FW partition │ └── [...] ├── fip FIP binaries for FIP partitions and supported boot chains │ ├── fip-<board name>-<hardware security>-ddr-<boot chain>-<storage>.bin FIP binary for FIP DDR partition │ ├── fip-<board name>-<hardware security>-<boot chain>-<storage>.bin FIP binary for FIP partition │ └── [...] ├── flashlayout_st-image-weston Flash layout files (description of the partitions) for the supported boot chains on supported boot devices and boards │ ├── [...] │ ├── extensible Flash layout files for microSD card boot device with no userfs partition but a rootfs partition extended to microSD card size │ │ ├── FlashLayout_sdcard_<board name>-<hardware security>-extensible.tsv (recommended setup for package repository service) microSD card boot device with rootfs partition extended to microSD card size │ │ └── [...] │ └── optee Flash layout files for optee boot chain │ ├── FlashLayout_<boot device>_<board name>-<hardware security>-optee.tsv │ └── [...] ├── Kernel Debug binaries for Linux kernel │ ├── config-6.6.78 Reference config file for Linux kernel │ └── vmlinux Image of the Linux kernel ├── optee OPTEE-OS binaries │ ├── debug Debug binaries for OPTEE-OS │ │ ├── tee-<board name>-<hardware security>-<boot chain>.elf Debug symbol file for OPTEE-OS │ │ ├── tee-<board name>-<hardware security>-<boot chain>-programmer.elf Debug symbol file for OPTEE-OS configured for usb/serial │ │ └── [...] │ ├── tee-header_v2-<board name>-<hardware security>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-header_v2-<board name>-<hardware security>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ ├── tee-pageable_v2-<board name>-<hardware security>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-pageable_v2-<board name>-<hardware security>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ ├── tee-pager_v2-<board name>-<hardware security>-<boot chain>.bin OPTEE-OS binary for FIP binaries creation (FIP partition) │ ├── tee-pager_v2-<board name>-<hardware security>-<boot chain>-programmer.bin OPTEE-OS binary for FIP binaries creation (FIP-BOOT partition) │ └── [...] ├── scripts │ └── create_sdcard_from_flashlayout.sh ├── u-boot U-BOOT binaries │ ├── debug Debug binaries for U-BOOT │ │ ├── u-boot-<soc name>-<u-boot config>.elf Debug symbol file for U-BOOT │ │ └── [...] │ ├── configuration-<soc name>_defconfig Reference configuration file for U-Boot │ ├── u-boot-nodtb-<soc name>-<u-boot config>.bin U-BOOT binary for FIP binaries creation │ ├── u-boot-<board name>-<hardware security>-<u-boot config>.dtb U-BOOT device tree for FIP binaries creation │ └── [...] ├── st-image-bootfs-openstlinux-weston-stm32mp2-m33td.bootfs.ext4 Binary for bootfs partition on eMMC and microSD card devices ├── st-image-bootfs-openstlinux-weston-stm32mp2-m33td.bootfs.manifest ├── st-image-userfs-openstlinux-weston-stm32mp2-m33td.userfs.ext4 Binary for userfs partition on eMMC and microSD card devices ├── st-image-userfs-openstlinux-weston-stm32mp2-m33td.userfs.manifest ├── st-image-vendorfs-openstlinux-weston-stm32mp2-m33td.vendorfs.ext4 Binary for vendorfs partition on eMMC and microSD card devices ├── st-image-vendorfs-openstlinux-weston-stm32mp2-m33td.vendorfs.manifest ├── st-image-weston-openstlinux-weston-stm32mp2-m33td.rootfs.ext4 Binary for rootfs partition on eMMC and microSD card devices ├── st-image-weston-openstlinux-weston-stm32mp2-m33td.rootfs.license ├── st-image-weston-openstlinux-weston-stm32mp2-m33td.rootfs-license_content.html License summary for all packages needed to feed all partitions ├── st-image-weston-openstlinux-weston-stm32mp2-m33td.rootfs.manifest └── [...]
Description:
<soc name>: * stm32mp21 * stm32mp25 <board name>: * stm32mp215-df, stm32mp257f-ev1 <hardware security>: * if nothing declared then there is a minimal hardware configuration for RIFF profile OPEN * cm33tdcid-ostl custom hardware configuration (can be different following use-case and hardware) for RIFF profile CUSTOM (CLOSED) * cm33tdcid-ostl-serial-ca35tdcid specific configuration used for programmation <boot chain>: * optee optee boot chain <storage>: * emmc eMMC storage * nor NOR storage * programmer-uart storage programmation via UART * programmer-usb storage programmation via USB * sdcard microSD card storage <storage a35>: * emmc eMMC storage * nor NOR storage * sdcard microSD card storage <storage m33>: * emmc eMMC storage * nor NOR storage * sdcard microSD card storage <boot device>: * emmc boot Cortex M33 via emmc storage and Cortex A35 via emmc storage * nor-emmc boot Cortex M33 via nor storage and Cortex A35 via emmc storage * nor-nor-sdcard boot Cortex M33 via nor storage and Cortex A35 via nor storage for first stage (fsbl, fip) and files system are located on sdcard storage * nor-sdcard boot Cortex M33 via nor storage and Cortex A35 via sdcard * sdcard boot Cortex M33 via sdcard storage and Cortex A35 via sdcard storage <u-boot config>: * default * programmer Programmer config enabled
7. Populate the SDCard[edit | edit source]
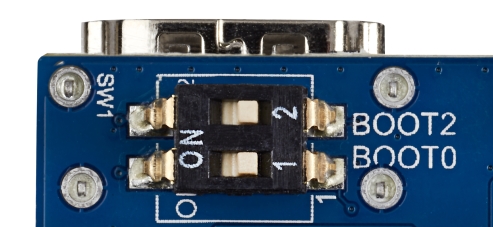
- Set the boot switches (located at the back of the board) to the off position
- Connect USB Type A to Type C cable between PC and CN7/USB_OTG port of the STM32MP157C-DK2 board
- Power up the board
- Press the reset button to reset the board
- Launch STM32CubeProgrammer to get the GUI
- On the right, select USB (not STLINK, set by default) in the connection picklist and click on "Refresh" button. Serial Number is displayed if USB is detected. Click on "Connect"
- Select "Open File" tab and select $HOME/STM32MPU_workspace/STM32MP15-Ecosystem-v1.x.0/stm32mp1-openstlinux-xx-yy-zz/images/stm32mp1/flashlayout_st-image-weston the FlashLayout_sdcard_stm32mp157c-dk2-trusted.tsv, in the Starter Package installation folder.
- Fill the "Binaries Path" by browsing up to folder $[Starter_Pack_Path]/images/stm32mp1
- Click on "Download" to start the flashing process.
- Progress is displayed with progress bar till completion popup message.
8. Boot the board[edit | edit source]
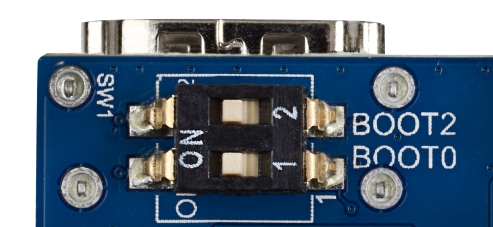
- Set the boot switches (located at the back of the board) to the ON position
- Power up the board
- Press the "Reset "button to reset the board
- After few seconds, the board starts and automatically goes through the following screens
- If the board power supply doesn't supply enough current (3A), the red LED indicates the issue following the rules below:
blink console message boot process 2 times WARNING 500mA power supply detected Current too low, use a 3A power supply!
Continue and red LED stays ON 3 times WARNING 1500mA power supply detected Current too low, use a 3A power supply!
Continue and red LED stays ON forever ERROR USB TYPE-C connection in unattached mode Check that USB TYPE-C cable is correctly plugged
stop forever USB TYPE-C charger not compliant with USB specification stop