1. Article purpose[edit source]
To meet the new market security requests and protect customers against any leakage of their IPs
, STMicroelectronics
introduces a security feature, the secure secret provisioning (SSP), allowing the programming of OEM secrets into STM32 MPU
one time programming (OTP) area in a secure way (with confidentiality, authentication and integrity checks).
The STM32MP1 Series supports protection mechanisms allowing the protection of critical operations (such as cryptography
algorithms) and critical data (such as secret keys) against unexpected access.
This wiki gives an overview of the STM32MP1 Series SSP solution with its associated tools ecosystem.
2. SSP overview[edit source]
The SSP is a secure system mechanism implemented in STM32 microprocessors that allows secured and counted
installation of OEM secrets in untrusted production environment (such the OEM contract manufacturer).
The SSP process prevents the OEM secrets from:
- being accessed by the contract manufacturer.
- being extracted or disclosed.
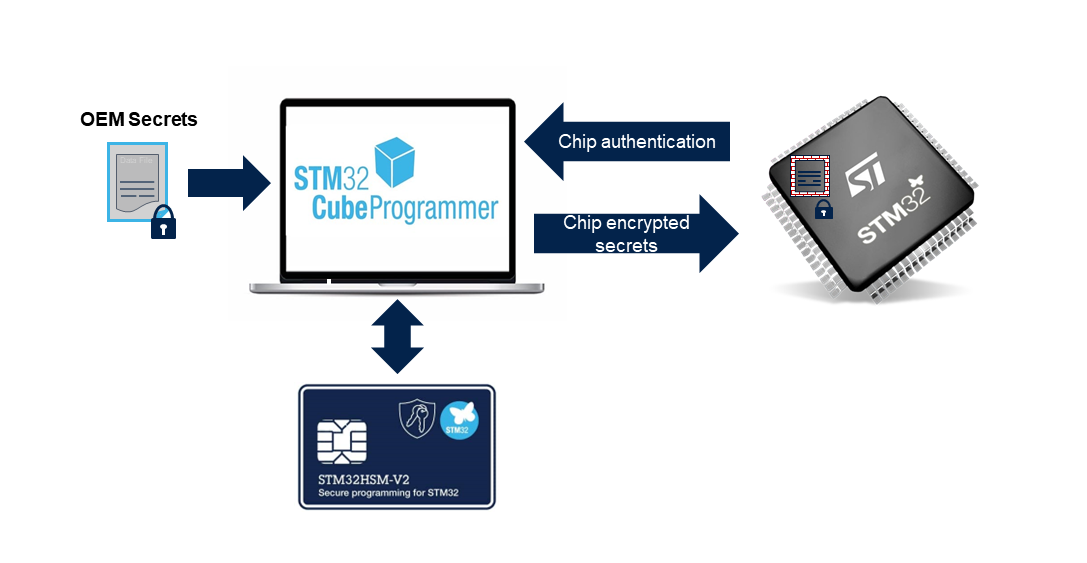
Following the SFI strategy, the SSP processing relies on a STM32 Hardware Security Module[1] (HSM) to manage chip authentication and encrypted dedicated communication to exchange data with STM32 chip. This chip authentication allows to count the number of provisioned devices. The STM32 HSM is connected to the programing tool (STM32CubeProgrammer presented as example) that will upload the encrypted data to the chip.
3. SSP embedded software implementation[edit source]
The SSP chip implementation relies on two embedded software parts:
- The ROM code SSP.
- A TF-A BL2 based SSP dedicated firmware.
3.1. ROM Code SSP implementation[edit source]
The ROM code has a complete access to chip data. During the SSP process, it is in charge of:
- Generate the chip certificate.
- Download the TF-A SSP Firmware from the programming tool.
- Decrypt the secret data.
- Authenticate the TF-A SSP Firmware.
3.2. TF-A SSP Firmware[edit source]
The TF-A BL2 SSP firmware is a specific part of code that will extend the communication with the programming tool and will be in charge of specific SSP commands:
- Initialize the SSP processing by changing the chip life cycle state.
- Send the ROM code prepared certificate to the programming tool to allow chip authentication.
- Receive the secret data from the programming tool and store them in a dedicated secure memory region for the ROM code.
- Write all the decrypted secrets in the chip and set the chip to CLOSE SECURE state.
This part of code is using part of TF-A BL2 generic code but only restricted to serial connection mode and OTP access. It limits the TF-A SSP size to the minimum but required a dedicated board configuration (over device tree).
4. SSP STM32 tools[edit source]
Trusted Package Creator offers the way to:
- Generate OEM keys
- Provision the ST HSMv2 card
- Generate secret file (coming soon)
This is the essential tool for the OEM to manage a complete encrypted secret package and customized HSMv2 to the untrusted manufacturer.
5. Running the SSP process[edit source]
The SSP required different stages:
- At OEM level:
- Generate OEM keys
- HSM provisioning
- Generate secret files
- Customize TF-A BL2 SSP firmware
- Sign the TF-A BL2 SSP firmware
- At untrusted manufacturer level
- Set the chip in SSP provisioning state
- Send the data to the chip
A dedicated page How to manage SSP explains all the steps (from the OEM key generation till the final provisioning) to complete a SSP sequence.