1. Introduction
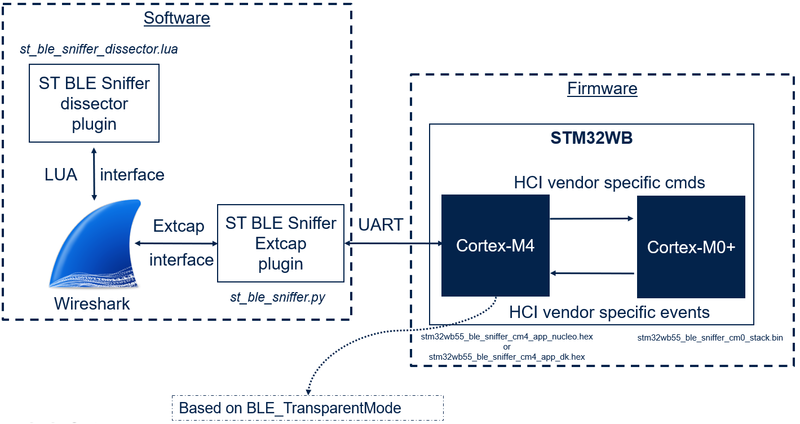
The STM32 Sniffer for Bluetooth® Low Energy is composed of two main parts:
- The software part running on the computer: analyzes and displays packets.
- The firmware part running on the STM32WB MCU: intercepts over the air packets.
| System Architecture |
|---|
Download the necessary files on the STM32 hotspot.
2. Minimum requirements
The following software and hardware parts are needed.
2.1. Hardware
At least one of these development boards is needed:
2.2. Software
Operating system:
- Windows 10
- Version 4.0.3 or later
- During the setup, accept the installation of Ncap.
- Version 3.11.2 or later
- Add Python to your path (you can select “Add Python to environment variable.” during setup).
- Version 3.5 or later
- Make sure that PySerial is installed on the correct version of Python if you have multiple installations. Use pip3 for example to force install on Python3.
3. Programming the board
There are two files to flash:
- The sniffer application: stm32wb55_ble_sniffer_cm4_app_nucleo.hex or stm32wb55_ble_sniffer_cm4_app_dk.hex
- The sniffer Bluetooth® LE wireless stack: stm32wb55_ble_sniffer_cm0_stack.bin
1. Install STM32CubeProgrammer
2. Update the wireless stack:
- Use the stm32wb55_ble_sniffer_cm0_stack.bin file at the start address: 0x080CE000.
- Follow the part 3.2 of the tutorial to learn how to update the wireless stack.
3. Flash the application firmware:
- Use the stm32wb55_ble_sniffer_cm4_app_nucleo.hex or stm32wb55_ble_sniffer_cm4_app_dk.hex file.
- Follow the part 3.3 of the tutorial to learn how to flash the application firmware.
4. Installing Wireshark plugins
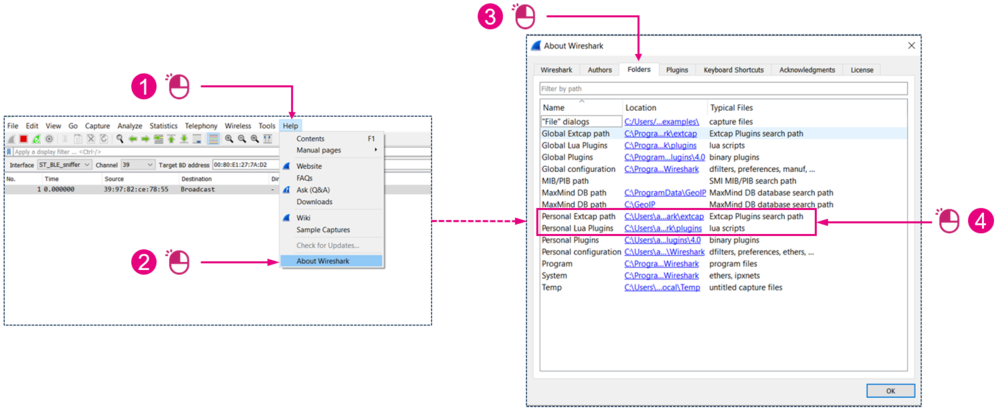
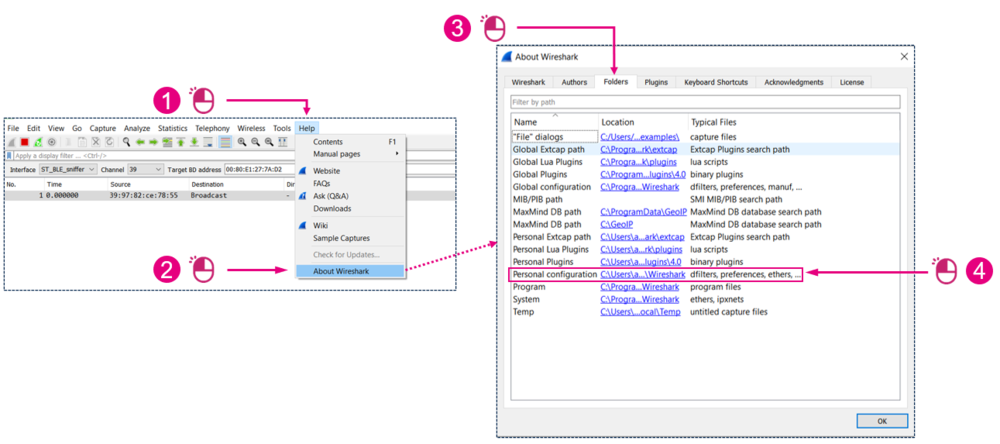
Launch Wireshark:
| Finding the Wireshark plugins directories |
|---|
4.1. Installing the plugins
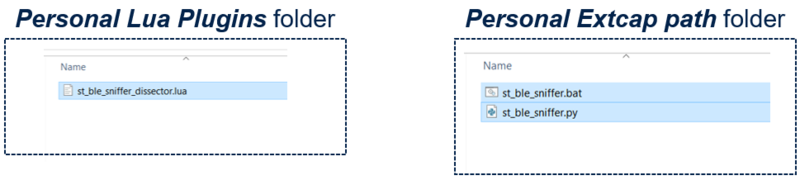
- Copy the st_ble_sniffer_dissector.lua file into your Wireshark Personal Lua Plugins folder.
- Copy the st_ble_sniffer.py and st_ble_sniffer.bat files into your Wireshark Personal Extcap path folder.
Your folders should look like this:
| Plugins folders |
|---|
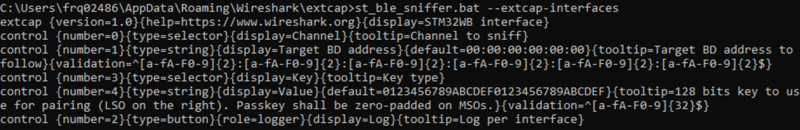
- Open a command prompt in your Personal Extcap path folder.
- Run: st_ble_sniffer.bat --extcap-interfaces
You should have an output similar to this:
| Verifying that the extcap plugin runs |
|---|
- Make sure that the board with the sniffer firmwares is plugged, and that no other programs use the com port such as the serial terminal.
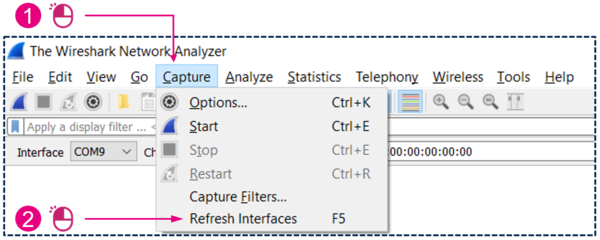
- In Wireshark, refresh the capture interfaces list:
| Verifying extcap plugin can run in Wireshark |
|---|
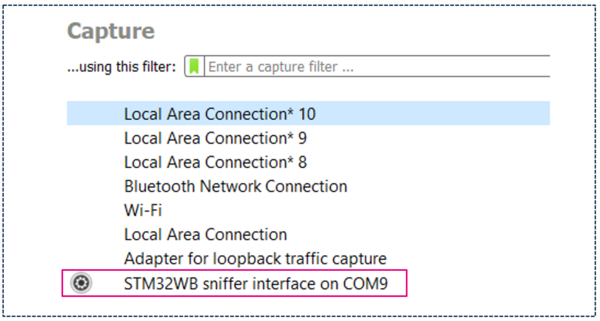
You should now see the STM32WB sniffer interface like this:
| Verifying that extcap plugin runs in Wireshark |
|---|
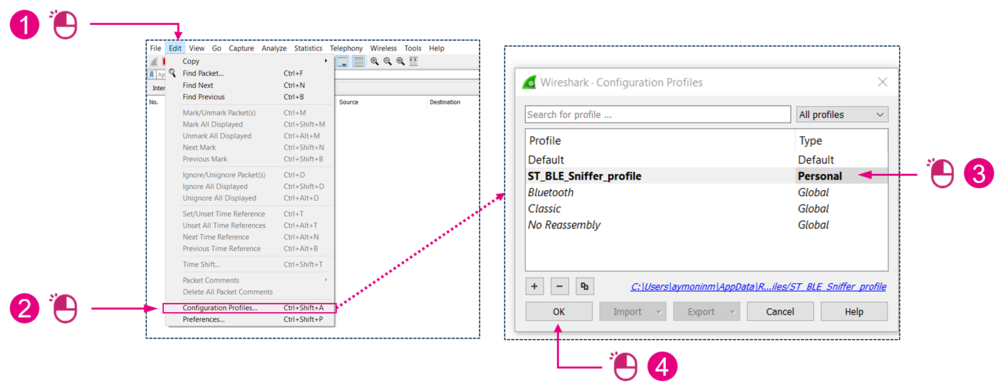
4.2. Installing the profile
In Wireshark:
| Finding the Wireshark profiles directory |
|---|
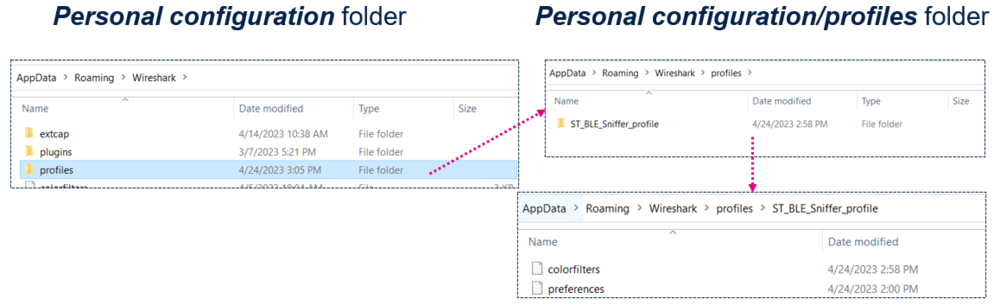
Copy the ST_BLE_Sniffer_profile folder into your Wireshark Personal configuration/profiles folder.
Your folder should look like this:
| Verifying that extcap plugin runs in Wireshark |
|---|
5. Configuring Wireshark
5.1. Enabling the sniffer profile
In Wireshark:
| Enabling the profile |
|---|
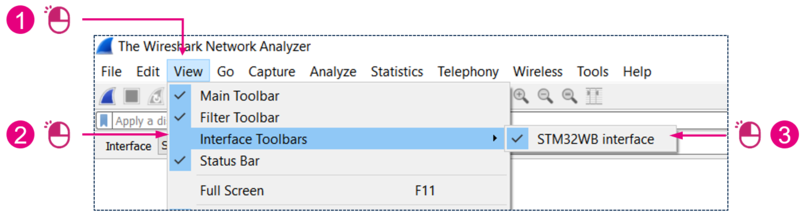
5.2. Enabling the interface toolbar
Open Wireshark:
| Enabling the interface toolbar |
|---|
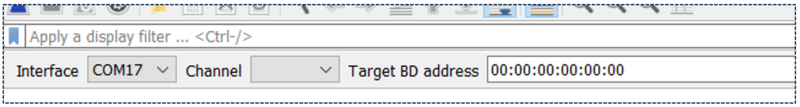
This toolbar should be visible:
| Interface toolbar |
|---|
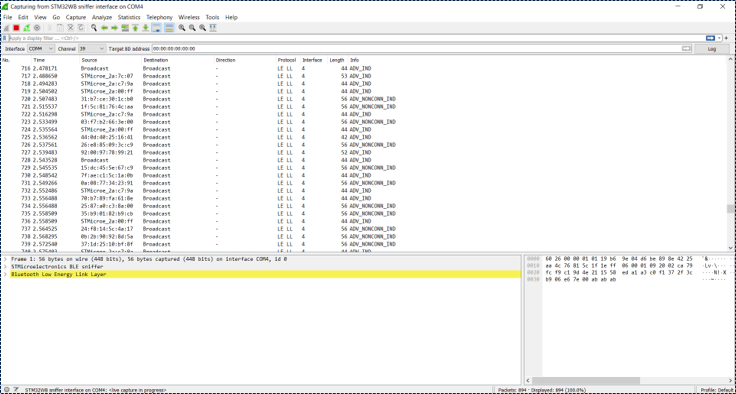
5.3. Testing
Double click on the STM32WB sniffer interface to launch the capture.
| Verifying that extcap plugin runs in Wireshark |
|---|
If advertising packets are visible like in the graphic below, it means that the installation of the STM32 Sniffer for Bluetooth® Low Energy is successful.
| Verifying the installation |
|---|
Refer to the user guide to learn more about how to use the sniffer.