1. RDP level management
The STM32U0 silicon device life cycle is based on the RDP mechanism implemented for the FLASH interface, as specified in the STM32U0 reference manual (RM0503[1], section 3.5.1).
| RDP protection level | Debug | Comments |
|---|---|---|
| Level 0: device open | Allowed | The boot address can be either the user flash memory, bootloader in system memory, or embedded SRAM, depending on the boot mode configuration. Any security configuration including OEM1 and OEM2 keys can be provisioned in the flash memory user option bytes. |
| Level 1: device memories protected | Limited | The boot address can be either the user flash memory, bootloader in system memory, or embedded SRAM, depending on the boot mode configuration. Debug access to the user flash memory, embedded SRAM, and backup registers is not allowed. |
| Level 2: device closed | None | The boot address must target the user flash memory. The flash memory user option bytes are read-only, so RDP level 2 cannot be changed, unless the OEM2 unlocking key is activated. |
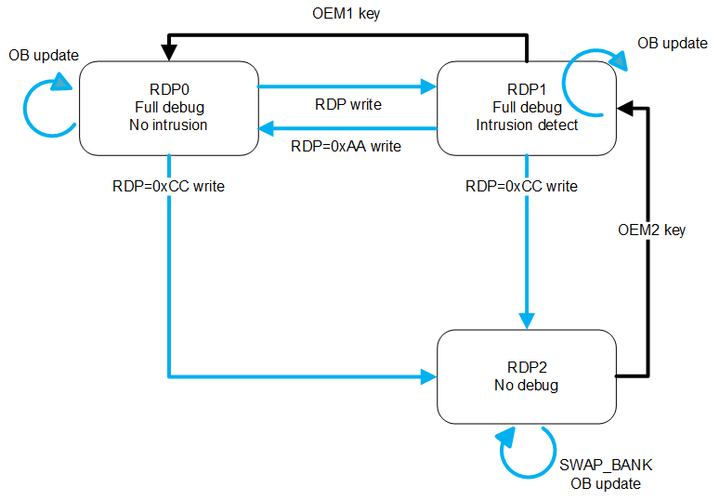
The figure below illustrates the level transitions:
Changing the read protection level:
- From level 0 to level 1: write any other values than 0xCC or 0xAA in the RDP register.
- From level 0 or 1 to level 2: write 0xCC in the RDP register.
- From level 2 to level 1: inject the OEM2KEY value through the debug interface during reset. This operation is relevant only if the OEM2 password lock activation was executed previously.
- From level 1 to level 0:
- If the OEM1 password lock activation was done: inject the OEM1KEY value through the debug interface during reset.
- If the OEM1 password lock activation was not done: write 0xAA in the RDP register.
2. RDP password regression
Regression allows the reopening of the product by returning to RDP level 0. A full user flash memory mass erase is applied prior to the reopening.
The devices support both the permanent and password-based RDP level 2 regression to level 1. This level 2 to level 1 regression does not erase the application code, nor does it change the RDP level 1 protections in place.
The provisioning of two 128-bit passwords independently controls the unlocking of:
- The RDP level 2 to level 1 regression password, configured when OEM2LOCK=1.
- The RDP level 1 to level 0 regression password, configured when OEM1LOCK=1.
The table below describes the possible combinations of mutual password usage:
| OEM2LOCK | OEM1LOCK | |
|---|---|---|
| 0 | 1 | |
| 0 | RDP 1 to 0 always granted RDP 2 to 1 never granted |
RDP 1 to 0 needs OEM1KEY unlock sequence RDP 2 to 1 never granted |
| 1 | RDP 1 to 0 always granted RDP 2 to 1 needs OEM2KEY unlock sequence |
RDP 1 to 0 needs OEM1KEY unlock sequence RDP 2 to 1 needs OEM2KEY unlock sequence |
3. References