under construction
1. Environment setup
1.1. HW
1.1.1. Board setup
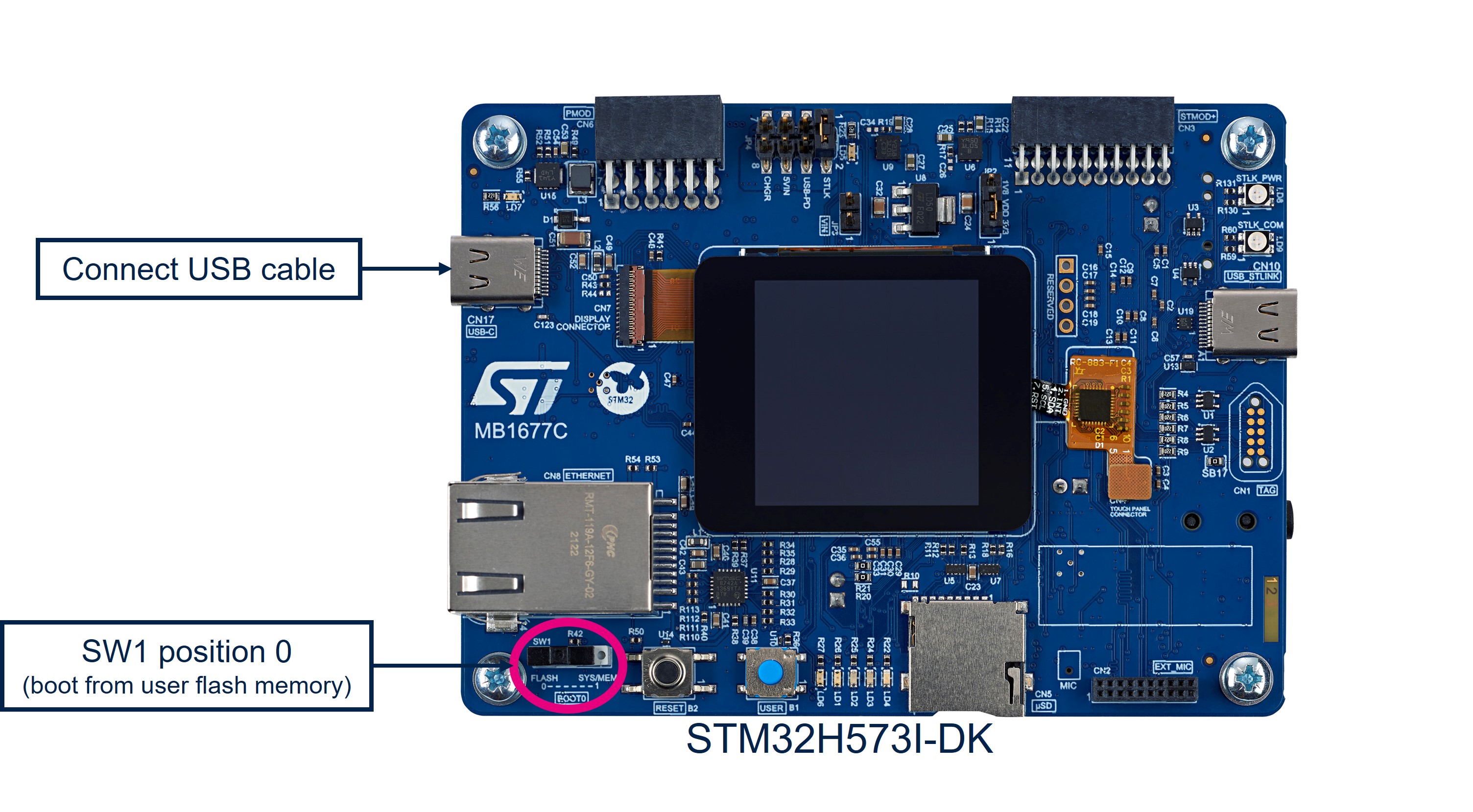
To set up the hardware environment, STM32H573_DK MB1677 board shall be connected to a personal computer via a USB cable. This connection with the PC allows the user:
- Programming the STM32TRUSTEE SM package in the board.
- Interacting with the board via a UART console
- Debugging Integrator’s non-secure application when STM32TRUSTEE Integrator’s configuration enables it.
The boot pin shall be forced to user Flash via the switch SW1.
1.2. SW
1.2.1. Install STM32CubeH5 SW Package
- Download[1] STM32Cube MCU Package for STM32H5 series
- Register on www.st.com web site if necessary
- Unzip the downloaded file
STM32CubeH5 SW Package is now installed on your computer.
This package provides scripts used to run STM32TRUSTEE SM installation using STM32CubeProgrammer.
1.2.2. Install X-CUBE-SEC-M-H5 SW package
- Download X-CUBE-SEC-M-H5[2] STM32Cube Expansion Package STM32TRUSTEE-SM for STM32H5 series
- Register on www.st.com web site if necessary
- Unzip the downloaded files and copy them within the installation directory of the STM32CubeH5 SW package.
X-CUBE-SEC-M-H5 SW package is now installed on your computer.
This package delivers STM32TRUSTEE SM.
1.3. Tools
1.3.1. Install STM32CubeProgrammer and STM32TrustedPackageCreator
STM32CubeProgrammer (STM32CubeProg) is an all-in-one multi-OS software tool for programming STM32 products. STM32CubeProgrammer provides an easy-to-use and efficient environment for reading, writing, and verifying device memory through both the debug interface (JTAG and SWD) and the bootloader interface (UART, USB DFU, I2C, SPI, and CAN).
STM32TrustedPackageCreator is part of the STM32CubeProgrammer toolset and allows the generation of secure firmware and modules to be used for STM32 secure programming solutions.
- Download the latest version of STM32CubeProgrammer[3] Software programming tool for STM32
- Unzip the downloaded file and launch the SetupSTM32CubeProgrammer-xxx.exe corresponding to your OS, and follow the instructions.
Make sure to select STM32TrustedPackageCreator add-on during the installation of STM32CubeProgrammer
STM32CubeProgrammer and STM32TrustedPackageCreator are now installed on your computer.
1.3.2. Terminal emulator
A terminal emulator software is needed to run the non-secure application. It allows to display some information to understand operations done by the embedded applications and it allows to interact with the non-secure application in order to trig some operations. The example in this document is based on Tera Term, an open source free software terminal emulator that can be downloaded from the https://osdn.net/projects/ttssh2/ webpage. Any other similar tool can be used instead (Ymodem protocol support is required).
1.4. Working directory
In the next steps, we will manipulate several files.
For that purpose,
you must create your own working directory “WorkDir”
2. Development @ OEM: Firmware creation
3. Secure Room @ OEM: SFI package generation and HSM provisioning
3.1. Package structure overview
copy windows directories tree
3.2. SFI package generation
3.2.1. Inputs preparation
3.2.1.1. Key
3.2.1.2. IV
3.2.1.3. OEM FW
3.2.1.4. OEM OBK
3.2.1.4.1. DA
from C:\STM32CubeFirmware_Installation_path\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\DA\Config\DA_Config.xml SMAK getting started: slide 50
3.2.1.4.2. HDPL1_for_STiRoT
from C:\STM32CubeFirmware_Installation_path\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Config\SM_Config_Others.xml SMAK getting started: slide 49
3.2.1.4.3. HDPL2_for_3NS_Config
from C:\STM32CubeFirmware_Installation_path\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Config\SM_Config_General.xml SMAK getting started: slide 46
3.2.1.4.4. HDPL2_for_3NS
from C:\STM32CubeFirmware_Installation_path\Firmware\Projects\STM32H573I-DK\ROT_Provisioning\SM\Config\SM_Config_Keys.xml generate obk %stm32tpccli% -pb %projectdir%ST\SM_ST_Settings_1.xml %stm32tpccli% -obk %projectdir%ST\SM_ST_Settings_2.xml SMAK getting started: slide 48
3.2.1.5. Modules
3.2.1.6. OB
3.2.1.7. output
Output SFI file is the file to be created with sfi extension.
3.2.2. SFI package generation using STM32 Trusted Package Creator CLI (command line interface)
3.2.3. SFI package generation using STM32 Trusted Package Creator GUI (graphical user interface)
3.3. HSM programming
![]() 10min
10min
To program the HSM, you can follow the same steps described in this section of the SFI article using the STM32H573_DK MB1677 board: HSM programming.
After programming the HSM, it is now ready to be shipped to the CM together with the xxx.sfi package created before.