1. Article purpose[edit | edit source]
The purpose of this article is to:
- briefly introduce the HASH peripheral and its main features,
- indicate the peripheral instances assignment at boot time and their assignment at runtime (including whether instances can be allocated to secure contexts),
- list the software frameworks and drivers managing the peripheral,
- explain how to configure the peripheral.
2. Peripheral overview[edit | edit source]
The HASH peripheral is used to compute a message digest.
The HASH peripheral is also able to give the HMAC[1] used for authentication using the same algorithm support.
2.1. On STM32MP13x lines  [edit | edit source]
[edit | edit source]
Secure Hash algorithms supports:
- SHA-1 [2]
- SHA-2 :
- SHA-224
- SHA-256
- SHA-384
- SHA-512
- Truncated output SHA-512/224, SHA512/256
- SHA-3 [3]:
- SHA3-224
- SHA3-256
- SHA3-384
- SHA3-512
- SHAKE128 and 256
- Keccak-based functions
- HMAC support for all supported algorithm
Refer to the STM32MP13 reference manuals for the complete list of features, and to the software frameworks and drivers, introduced below, to see which features are implemented.
2.2. On STM32MP15x lines  [edit | edit source]
[edit | edit source]
Secure Hash algorithms supports:
Refer to the STM32MP15 reference manuals for the complete list of features, and to the software frameworks and drivers, introduced below, to see which features are implemented.
3. Peripheral usage[edit | edit source]
This chapter is applicable in the scope of the OpenSTLinux BSP running on the Arm® Cortex®-A processor(s), and the STM32CubeMPU Package running on the Arm® Cortex®-M processor.
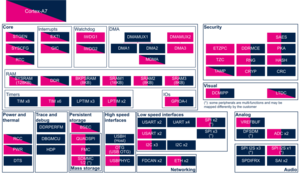
3.1. Boot time assignment[edit | edit source]
The HASH instance is used as boot device to support binary authentication.
3.1.1. On STM32MP13x lines  [edit | edit source]
[edit | edit source]
Click on the right to expand the legend...
Check boxes illustrate the possible peripheral allocations supported by STM32 MPU Embedded Software:
- ☐ means that the peripheral can be assigned (☑) to the given boot time context.
- ⬚ means that the peripheral can be assigned to the given boot time context, but this configuration is not supported in STM32 MPU Embedded Software distribution.
- ✓ is used for system peripherals that cannot be unchecked because they are statically connected in the device.
The present chapter describes STMicroelectronics recommendations or choice of implementation. Additional possibilities might be described in STM32 MPU reference manuals.
| Domain | Peripheral | Boot time allocation | Comment | |||
|---|---|---|---|---|---|---|
| Instance | Cortex-A7 secure (ROM code) |
Cortex-A7 secure (TF-A BL2) |
Cortex-A7 non-secure (U-Boot) | |||
| Security | HASH | HASH | ✓ | ☑ | ||
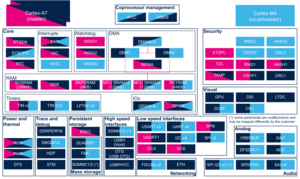
3.1.2. On STM32MP15x lines  [edit | edit source]
[edit | edit source]
Click on the right to expand the legend...
Check boxes illustrate the possible peripheral allocations supported by STM32 MPU Embedded Software:
- ☐ means that the peripheral can be assigned (☑) to the given boot time context.
- ⬚ means that the peripheral can be assigned to the given boot time context, but this configuration is not supported in STM32 MPU Embedded Software distribution.
- ✓ is used for system peripherals that cannot be unchecked because they are statically connected in the device.
The present chapter describes STMicroelectronics recommendations or choice of implementation. Additional possibilities might be described in STM32 MPU reference manuals.
| Domain | Peripheral | Boot time allocation | Comment | |||
|---|---|---|---|---|---|---|
| Instance | Cortex-A7 secure (ROM code) |
Cortex-A7 secure (TF-A BL2) |
Cortex-A7 non-secure (U-Boot) | |||
| Security | HASH | HASH1 | ✓ | ☑ | ||
| HASH2 | not used at boot time. | |||||
3.2. Runtime assignment[edit | edit source]
3.2.1. On STM32MP13x lines  [edit | edit source]
[edit | edit source]
Click on the right to expand the legend...
Check boxes illustrate the possible peripheral allocations supported by STM32 MPU Embedded Software:
- ☐ means that the peripheral can be assigned (☑) to the given runtime context.
- ⬚ means that the peripheral can be assigned to the given runtime context, but this configuration is not supported in STM32 MPU Embedded Software distribution.
- ✓ is used for system peripherals that cannot be unchecked because they are statically connected in the device.
Refer to How to assign an internal peripheral to an execution context for more information on how to assign peripherals manually or via STM32CubeMX.
The present chapter describes STMicroelectronics recommendations or choice of implementation. Additional possibilities might be described in STM32MP13 reference manuals.
| Domain | Peripheral | Runtime allocation | Comment | ||
|---|---|---|---|---|---|
| Instance | Cortex-A7 secure (OP-TEE) |
Cortex-A7 non-secure (Linux) | |||
| Security | HASH | HASH | ☐ | ☐ | Assignment (single choice) |
3.2.2. On STM32MP15x lines  [edit | edit source]
[edit | edit source]
Click on the right to expand the legend...
Check boxes illustrate the possible peripheral allocations supported by STM32 MPU Embedded Software:
- ☐ means that the peripheral can be assigned (☑) to the given runtime context.
- ⬚ means that the peripheral can be assigned to the given runtime context, but this configuration is not supported in STM32 MPU Embedded Software distribution.
- ✓ is used for system peripherals that cannot be unchecked because they are statically connected in the device.
Refer to How to assign an internal peripheral to an execution context for more information on how to assign peripherals manually or via STM32CubeMX.
The present chapter describes STMicroelectronics recommendations or choice of implementation. Additional possiblities might be described in STM32MP15 reference manuals.
| Domain | Peripheral | Runtime allocation | Comment | |||
|---|---|---|---|---|---|---|
| Instance | Cortex-A7 secure (OP-TEE) |
Cortex-A7 non-secure (Linux) |
Cortex-M4 (STM32Cube) | |||
| Security | HASH | HASH1 | ☐ | ☐ | Assignment (single choice) | |
| HASH2 | ☐ | |||||
4. Software frameworks and drivers[edit | edit source]
Below are listed the software frameworks and drivers managing the HASH peripheral for the embedded software components listed in the above tables.
- Linux®: crypto framework
- OP-TEE: HASH driver and Cryptographic Provider API (CP API)
- STM32Cube: HASH HAL driver and header file of HASH HAL module
- TF-A BL2: HASH driver
5. How to assign and configure the peripheral[edit | edit source]
The peripheral assignment can be done via the STM32CubeMX graphical tool (and manually completed if needed).
This tool also helps to configure the peripheral:
- partial device trees (pin control and clock tree) generation for the OpenSTLinux software components,
- HAL initialization code generation for the STM32CubeMPU Package.
The configuration is applied by the firmware running in the context in which the peripheral is assigned.
6. References[edit | edit source]