1. Different ways to secure STM32CubeMonitor
There are many ways to secure the STM32CubeMonitor tool. Each of these secured ways is easy to set up:
- Prevent or allow remote access: allow any machine different from the host to see the STM32CubeMonitor tool
- Secure the flow: create accounts with different permissions to modify the flow
- Secure the dashboard: create an account to regulate accesses to the dashboard
2. How to prevent or allow the connection of other machines to the tool?
This configuration prevents or allows the connection to the user's STM32CubeMonitor environment by someone who knows its IP address. From STM32CubeMonitor 1.5.0 onwards, the default value is to prevent external access. External accesses should be open only on secured networks.
Go in the ~/STMicroelectronics/stm32cubemonitor folder. Open the settings.js file and comment or uncomment the uiHost line :
uiHost: "127.0.0.1",
If this line is uncommented, nobody can access the STM32CubeMonitor tool except from the host machine. If the line is commented, anybody can access the STM32CubeMonitor tool.
3. How to secure my flow?
You can add a login and a password to your STM32CubeMonitor tool. This authentication will prevent non-logged users to modify and deploy your flow. Nevertheless, they will be able to go in dashboard mode and start the acquisition.
To secure your flow :
- Generate a password hash to hide the new password (see below)
- Go in the ~/STMicroelectronics/stm32cubemonitor folder. Open the settings.js file
- Uncomment the adminAuth block.
- Choose the username, and replace the default password by your new password hash. Finally, you can choose between two permissions :
- * : the user will be able to do whatever he wants on the flow.
- read : the user will only be able to see the flow configuration an switch in dashboard view but not to deploy. This is a "read-only" mode.
The "default" key gives the "read" permission to any user, even to the non-logged users.
adminAuth: {
type: "credentials",
users: [{
username: "admin",
password: "$2b$08$jLZtZBM8ySdwPGpbGsDaE.kZagU4cetH5c7QPhspaOJ60QSOahaoa", //password : admin
permissions: "*"
},
{
username: "user",
password: "$2b$08$f1pbalRjiHDBjOoPJ3fsmO6caEvFwGmbh0kFsTMmHuSkM6Z/BT8O.", //password : user
permissions: "read"
}],
default: {
permissions: "read"
}
},
Your tool is now secured you'll need an authentication to deploy your flow.
To go further, see the node-red page on how to secure a Node-RED® flow.
4. How to secure my dashboard?
You can add a login and a password in order to access to the dashboard window. The connection will be done after the click on the "dashboard" button, a popup will display. Thus, an user without account to connect on the dashboard will however be able to modify and deploy the flow. You can also combine the flow and the dashboard security.
Like the flow security, to secure your dashboard, go in the ~/STMicroelectronics/stm32cubemonitor folder. Open the settings.js file and uncomment the httpNodeAuth line. You may change the username and generate a new password following the same method (see below) :
httpNodeAuth: {user:"demo",pass:"$2b$08$50L83HdgJESfdUETL1f2ceyJVhi.Yi77XJ2C/.8rPRZZGTZpR5Zoy"}, //password : demo
To have more information see the node-red page on how to secure a node-red dashboard.
5. How to generate the password hash?
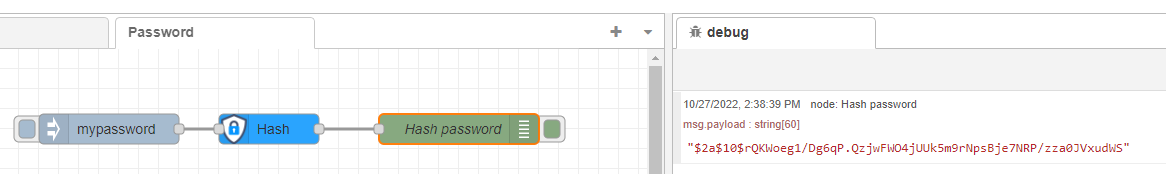
It is easy to generate the password hash with a flow in the editor:
- In the editor add the node "bcrypt". (Need STM32CubeMonitor 1.5.0 or above)
- Connect an inject node to send the password,
- Connect a debug node to log the result.
Copy/paste this code to import the nodes:
[{"id":"8c42fc7298eddcf0","type":"inject","z":"0c142a1d01775c4b","name":"","props":[{"p":"payload"}],"repeat":"","crontab":"","once":false,"onceDelay":0.1,"topic":"","payload":"mypassword","payloadType":"str","x":430,"y":80,"wires":[["fc91ac3519e28fee"]]},{"id":"fc91ac3519e28fee","type":"bcrypt","z":"0c142a1d01775c4b","name":"Hash","action":"encrypt","field":"payload","hash":"payload","target":"payload","assignment":"replace","match":"match","outputs":1,"rounds":10,"x":590,"y":80,"wires":[["22350cdbe3af32a8"]]},{"id":"22350cdbe3af32a8","type":"debug","z":"0c142a1d01775c4b","name":"Hash password","active":true,"tosidebar":true,"console":false,"tostatus":false,"complete":"payload","targetType":"msg","statusVal":"","statusType":"auto","x":780,"y":80,"wires":[]}]
In the inject node, set the password you want to use. Then click on the square button of the inject node. The hashed password is visible in the log on the right side of the tool.